Reflected XSS into attribute with angle brackets HTML-encoded
Description
The website in this lab contains a reflected cross-site scripting vulnerability in the search blog functionality where angle brackets are HTML-encoded.
Also see the leads from HackTricks concerning XSS methodology and XSS Inside HTML tags attribute: 2. If you can escape from the attribute but not from the tag (-> is encoded or deleted), depending on the tag you could create an event that executes JS code:
Reproduction and proof of concept
Put a random alphanumeric string in the search box, then use Burp Suite to intercept the search request and send it to Burp Repeater.
The random string has been reflected inside a quoted attribute.
Replace the input with a payload to escape the quoted attribute and inject an event handler:
" autofocus onfocus=alert(1) x="
Verify the technique worked by right-clicking, selecting “Copy URL”, and pasting the URL in the browser. When you move the mouse over the injected element it should trigger an alert.
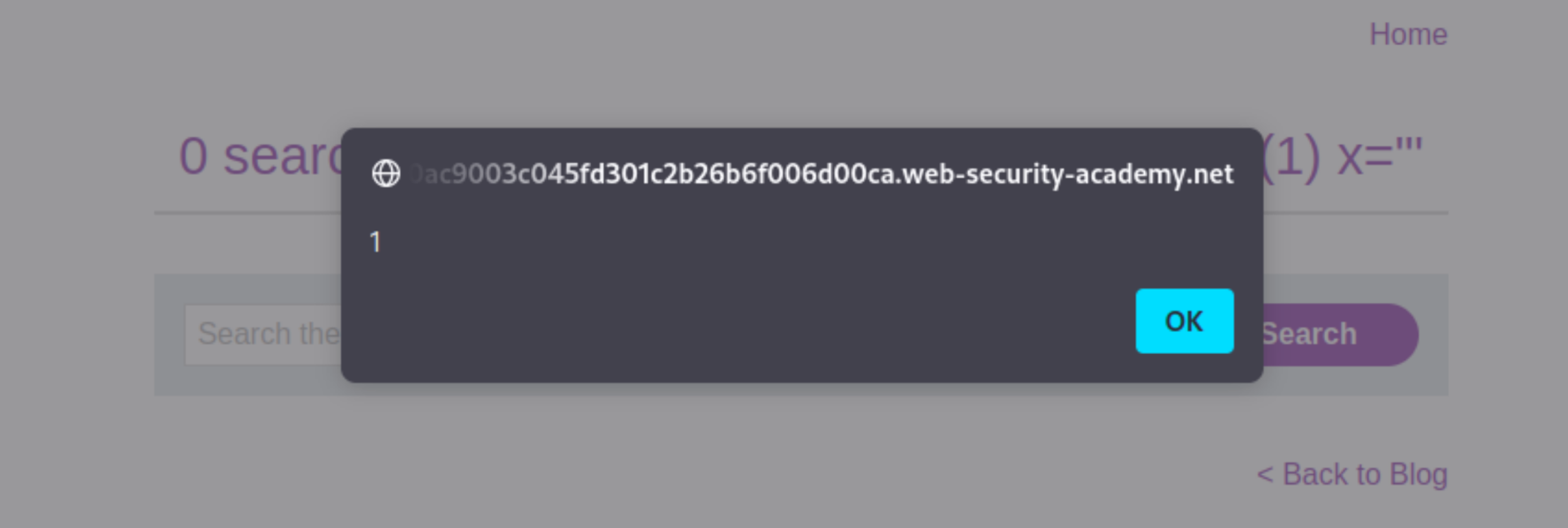
The resulting HTML:
<section class=blog-header>
<h1>0 search results for '" autofocus onfocus=alert(1) x="'</h1>
<hr>
</section>