2FA broken logic
Description
This lab’s two-factor authentication is vulnerable due to its flawed logic.
Reproduction and proof of concept
With Burp running, log in with
wiener:peterand investigate the 2FA verification process. Notice that in thePOST /login2request, theverifyparameter is used to determine which user’s account is being accessed.
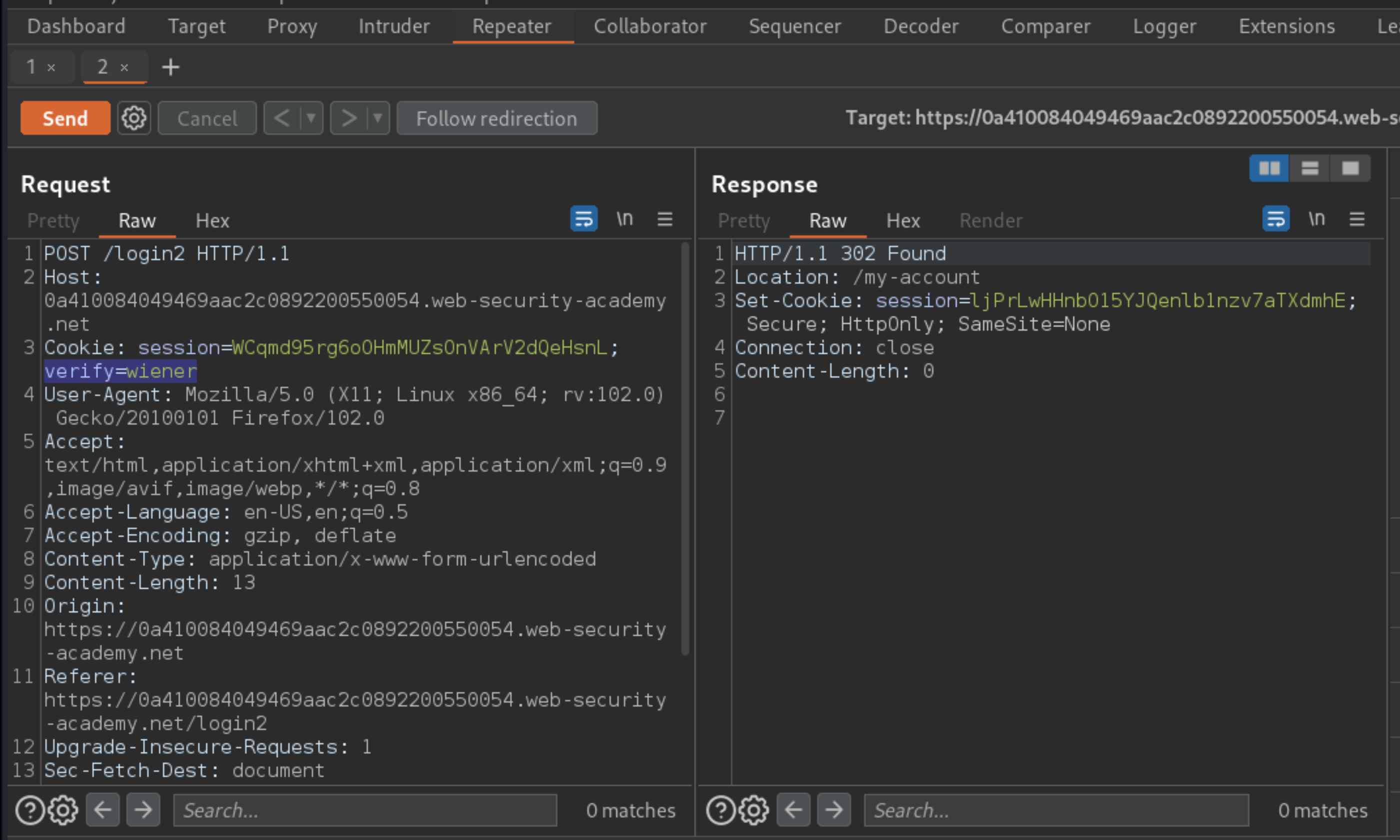
Log out of your account.
Send the
GET /login2request to Burp Repeater. Change the value of theverifyparameter tocarlosand send the request. This ensures that a temporary 2FA code is generated for Carlos.Go to the login page and enter your username and password. Then, submit an invalid 2FA code.
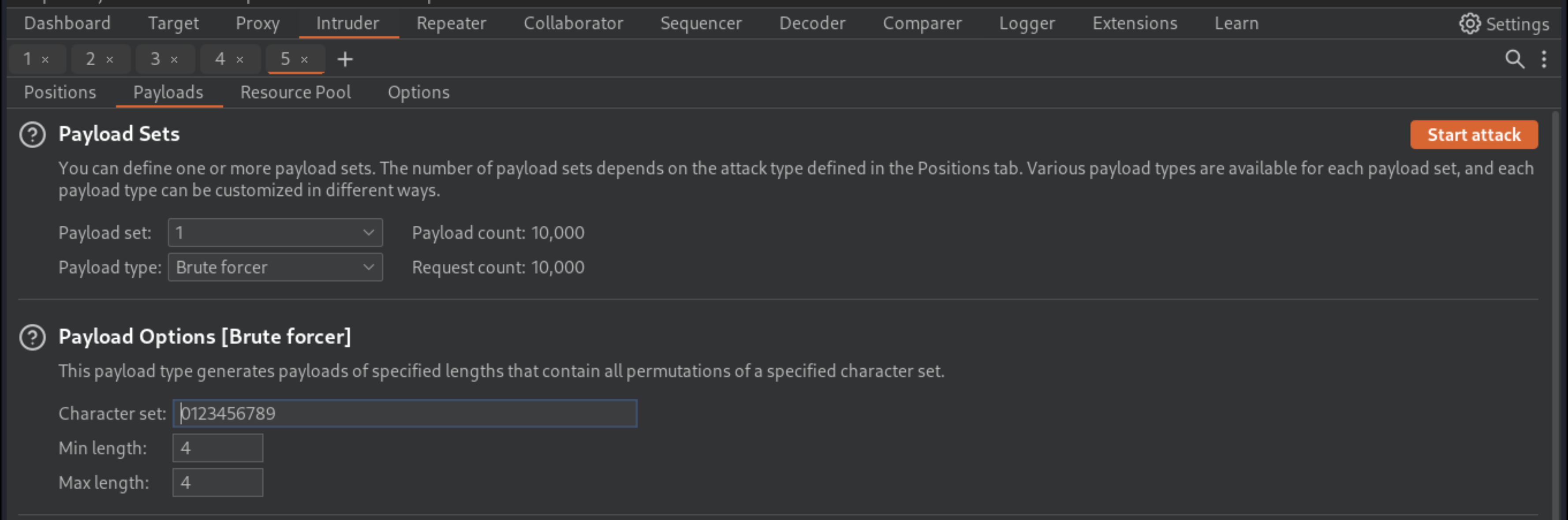
Send the
POST /login2request to Burp Intruder.In Burp Intruder, set the
verifyparameter tocarlosand add a payload position to themfa-codeparameter. Brute-force the verification code.
Load the
302response in your browser.
Exploitability
An attacker will need to make sure a MFA-code verification code is generated for user carlos by issuing a GET request to login2, then bruteforce the POST request to login2 using the Payload type: Brute forcer