2FA bypass using a brute-force attack
Description
This lab’s two-factor authentication is vulnerable to brute-forcing.
Reproduction and proof of concept
With Burp running, log in as
carlosand investigate the 2FA verification process. Notice that if you enter the wrong code twice, you will be logged out again. You need to use Burp’s session handling features to log back in automatically before sending each request.In Burp, go to Settings -> Sessions. In the Session Handling Rules panel, click Add. The Session handling rule editor dialog opens.
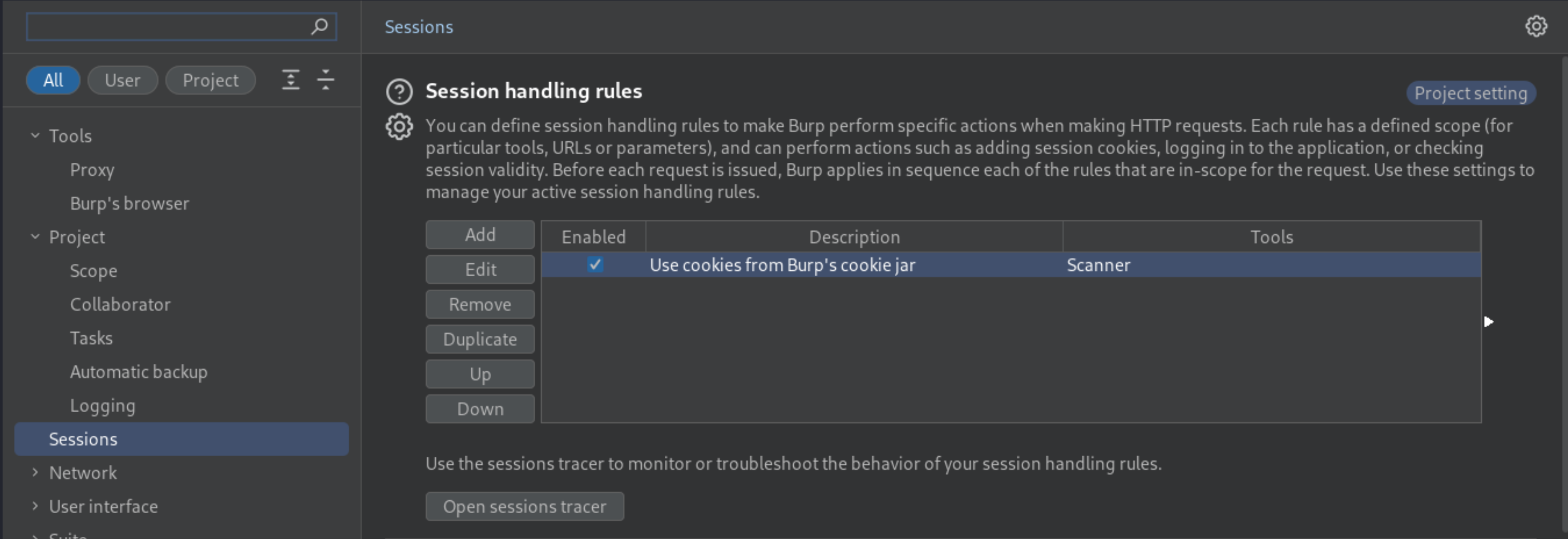
In the dialog, go to the Scope tab. Under URL Scope, select the option Include all URLs.
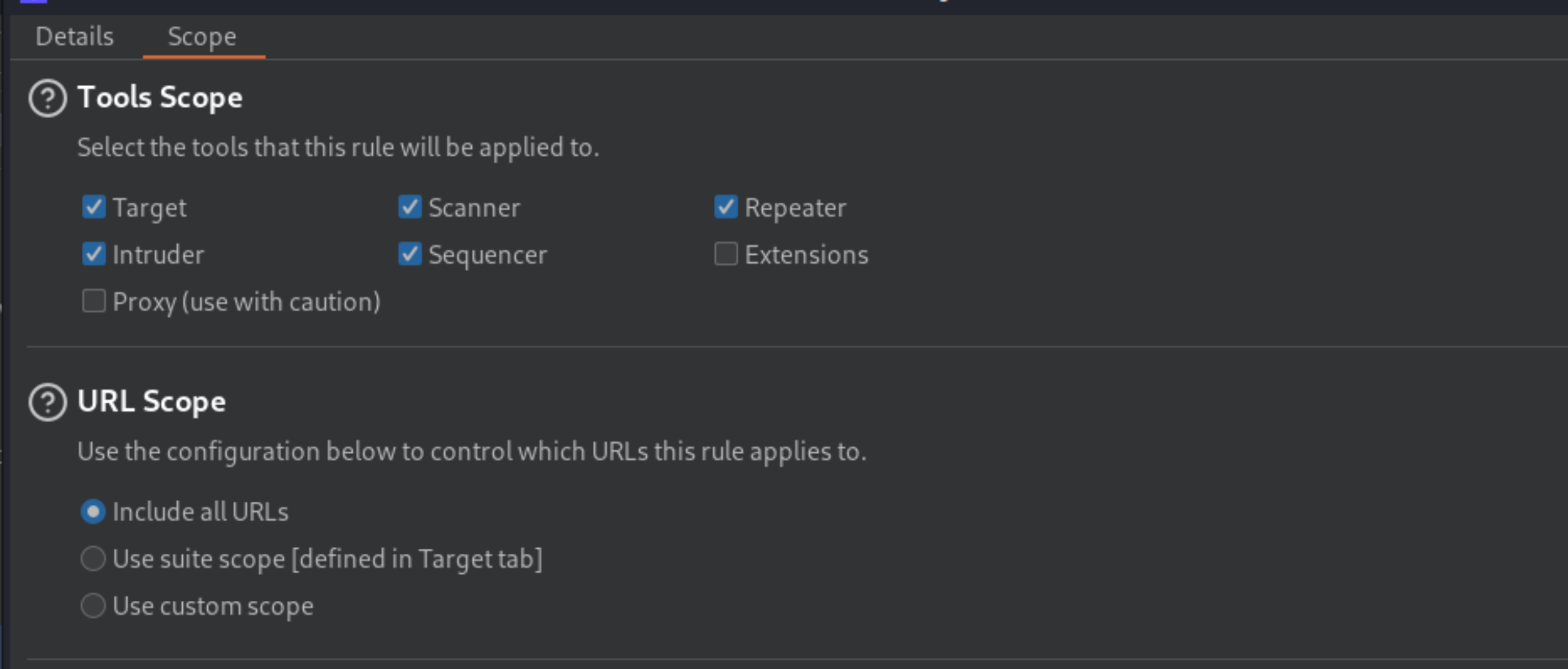
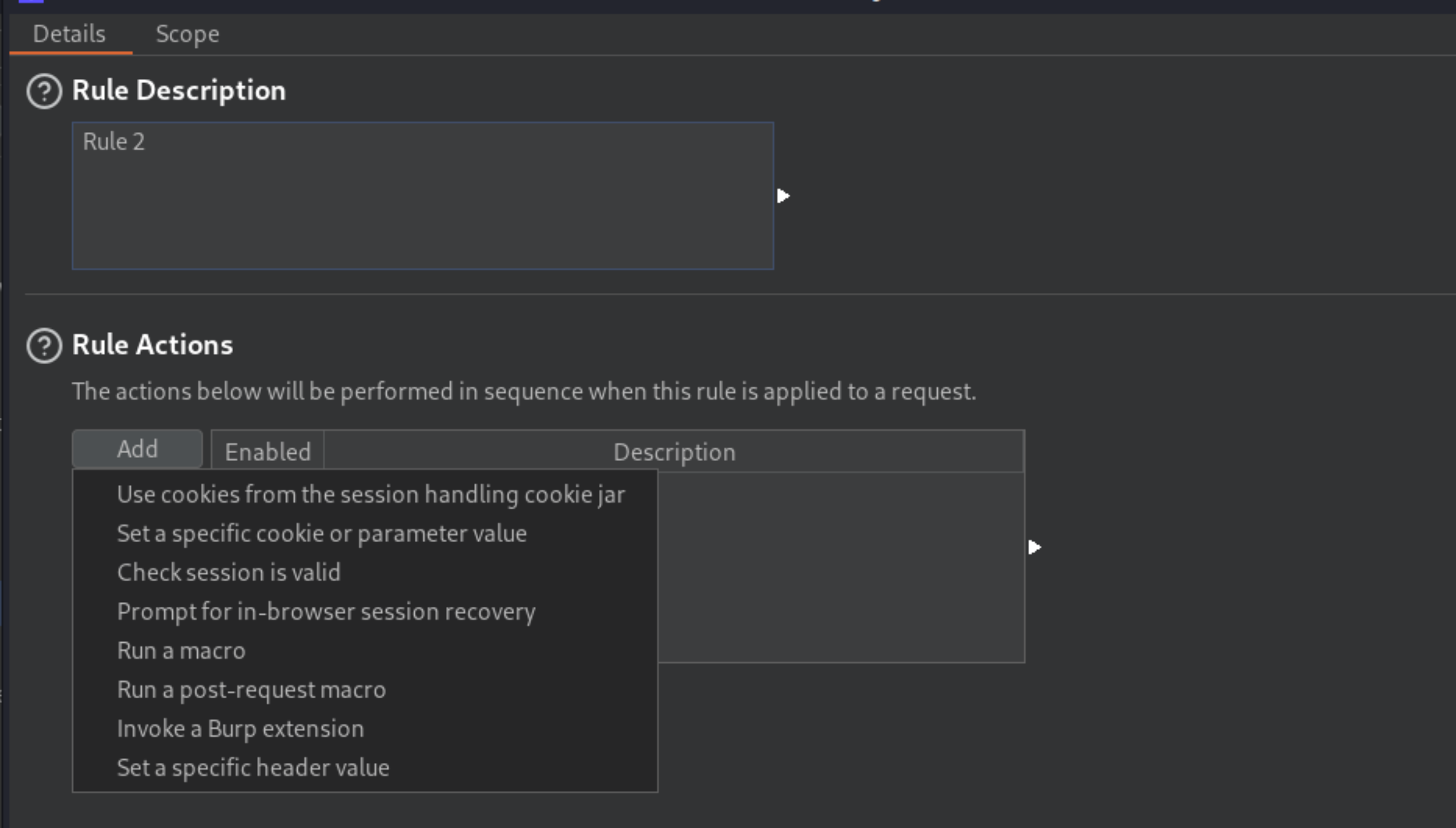
Go back to the Details tab and under Rule Actions, click Add -> Run a macro.
Under Select macro click Add to open the Macro Recorder. Select the following 3 requests:
GET /login
POST /login
GET /login2
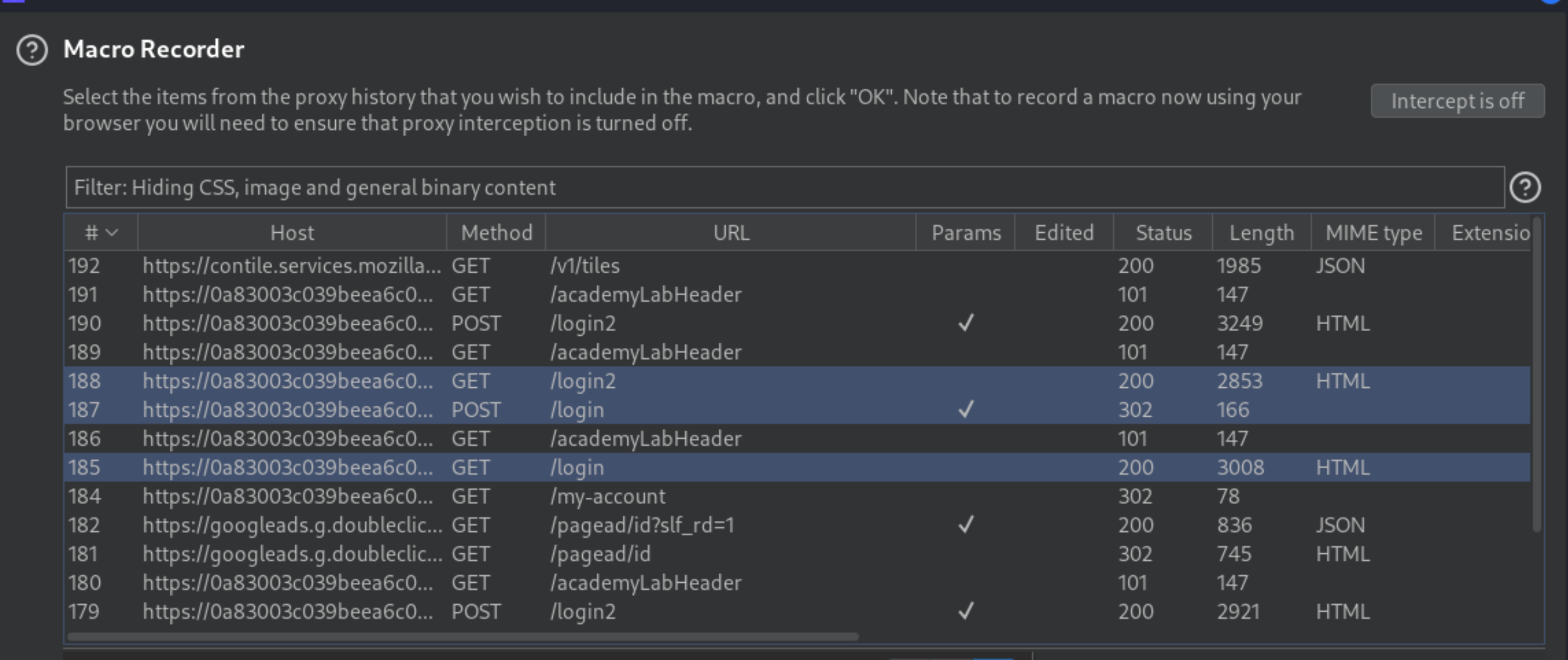
Then click OK. The Macro Editor dialog opens.
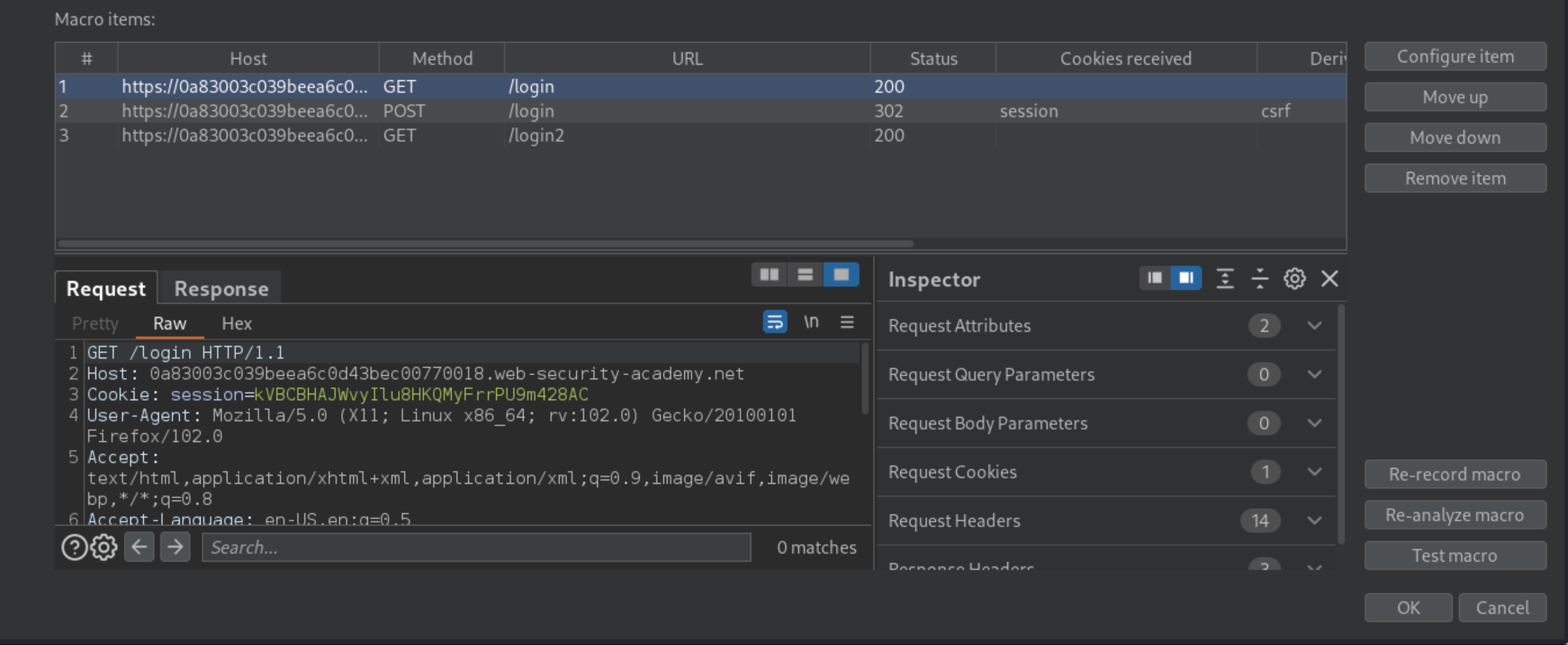
Click Test macro and check that the final response contains the page asking you to provide the 4-digit security code. This confirms that the macro is working correctly.
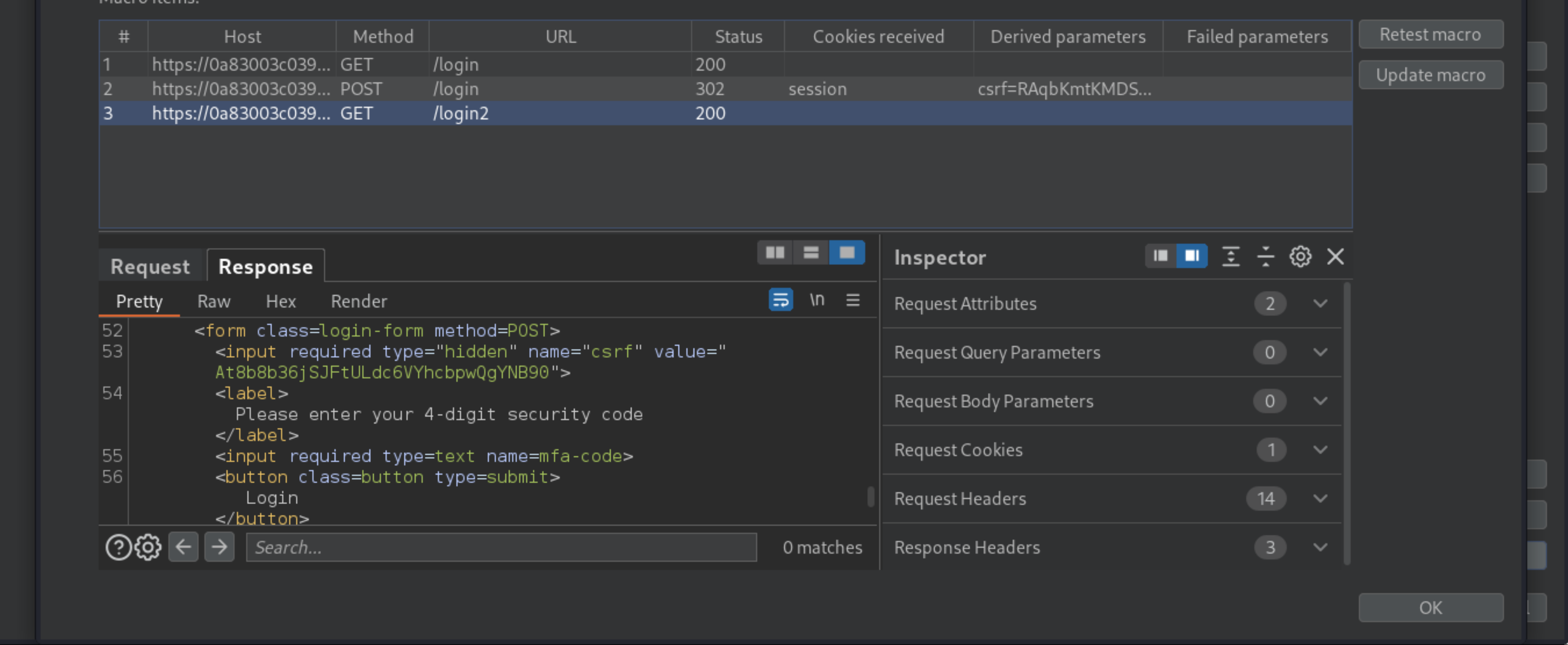
Keep clicking OK to close the various dialogs until you get back to the main Burp window. The macro will now automatically log you back in as Carlos before each request is sent by Burp Intruder.
Send the
POST /login2request to Burp Intruder.In Burp Intruder, add a payload position to the
mfa-codeparameter.On the Payloads tab, select the Numbers payload type. Enter the range
0 - 9999and set the step to1. Set the min/max integer digits to4and max fraction digits to0. This will create a payload for every possible 4-digit integer.Go to the Resource pool tab and add the attack to a resource pool with the Maximum concurrent requests set to
1.Start the attack. Eventually, one of the requests will return a
302status code. Right-click on this request and select Show response in browser. Copy the URL and load it in the browser.Click My account to solve the lab.
Exploitability
An attacker has already obtained a valid username and password (carlos:montoya), but does not have access to the user’s 2FA verification code. The attacker will need to brute-force the 2FA code and access carlos’s account page.