Information disclosure in version control history
Description
This lab discloses sensitive information via its version control history.
Reproduction and proof of concept
Open the lab and browse to
/.gitto reveal the lab’s Git version control data.Download a copy of this entire directory. For non-Windows users, the easiest way to do this is using the command
wget -r https://your-lab-id.web-security-academy.net/.git. Windows users will need to find an alternative method, or install a UNIX-like environment, such as Cygwin, in order to use this command.Explore the downloaded directory using your local Git installation. Notice that there is a commit with the message
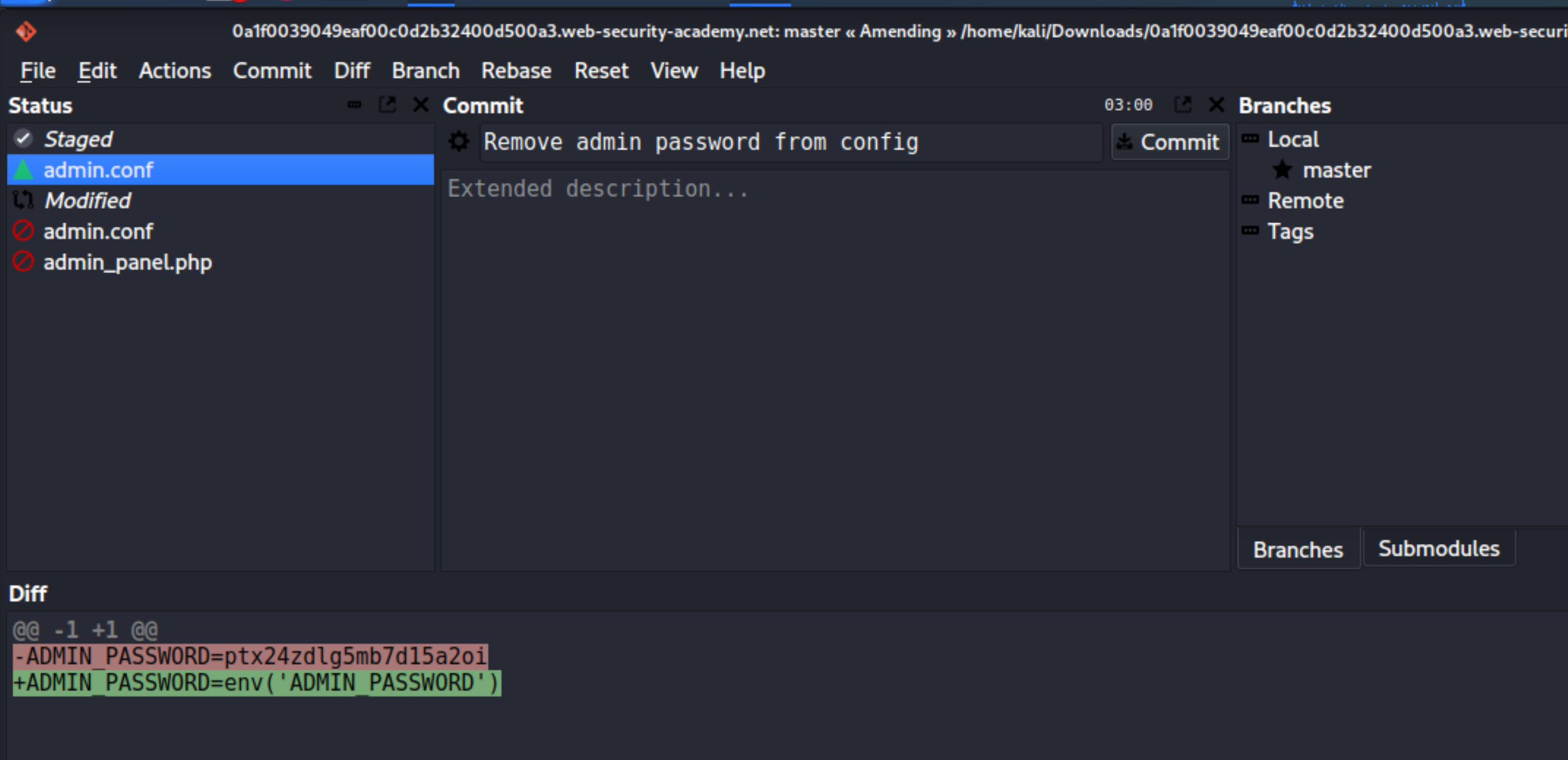
Remove admin password from config.Look closer at the diff for the changed
admin.conffile. Notice that the commit replaced the hard-coded admin password with an environment variableADMIN_PASSWORDinstead. The hard-coded password is still clearly visible in the diff.
Go back to the lab and log in to the administrator account using the leaked password.
To solve the lab, open the admin interface and delete Carlos’s account.
Exploitability
An attacker will need to obtain the password for the administrator user from git; then log in and delete Carlos’s account.