Authentication bypass via information disclosure
Description
This lab’s administration interface has an authentication bypass vulnerability, but it is impractical to exploit without knowledge of a custom HTTP header used by the front-end.
Reproduction and proof of concept
In Burp Repeater, browse to
GET /admin. The response discloses that the admin panel is only accessible if logged in as an administrator, or if requested from a local IP.Send the request again, but this time use the
TRACEmethod:TRACE /adminStudy the response. Notice that the
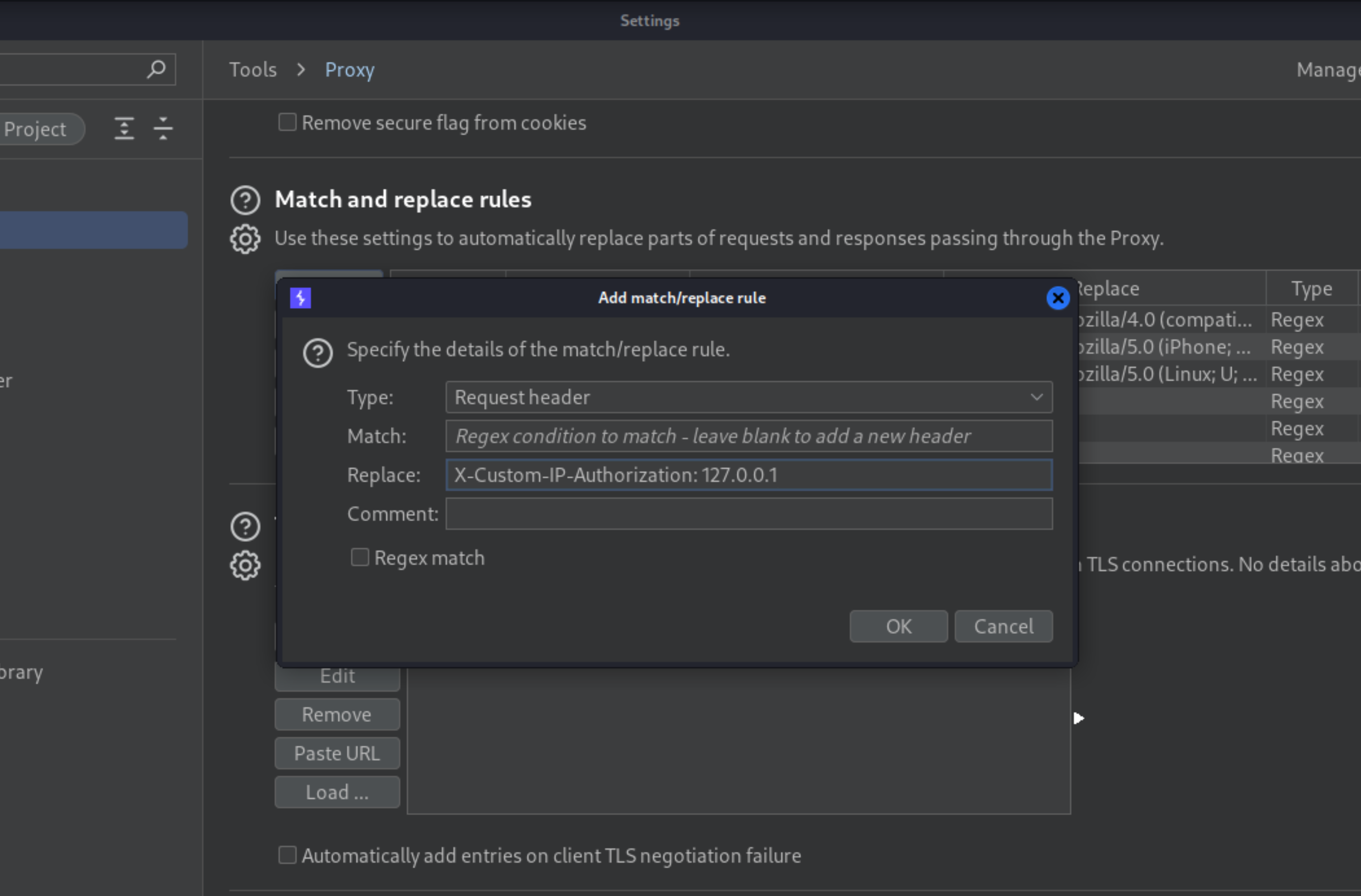
X-Custom-IP-Authorizationheader, containing your IP address, was automatically appended to your request. This is used to determine whether the request came from thelocalhostIP address.Go to Proxy -> Options, scroll down to the Match and Replace section, and click Add. Leave the match condition blank, but in the Replace field, enter
X-Custom-IP-Authorization: 127.0.0.1. Burp Proxy will now add this header to every request you send.
Browse to the home page. You now have access to the admin panel, where you can delete Carlos.
Exploitability
An attacker will need to log in to wiener:peter; obtain the header name then use it to bypass the lab’s authentication; and access the admin interface to delete Carlos’s account.