Inconsistent security controls
Description
This lab’s flawed logic allows arbitrary users to access administrative functionality that should only be available to company employees.
Reproduction and proof of concept
Open the lab then go to the Target -> Site map tab in Burp. Right-click on the lab domain and select Engagement tools -> Discover content to open the content discovery tool.
Click Session is not running to start the content discovery. After a short while, look at the Site map tab in the dialog. Notice that it discovered the path
/admin.Try and browse to
/admin. Although you don’t have access, the error message indicates thatDontWannaCryusers do.
Go to the account registration page. Notice the message telling
DontWannaCryemployees to use their company email address. Register with an arbitrary email address in the format:
attacker@exploit-0acf004f04439081c1c91280010e0052.exploit-server.net
Find your email domain name by clicking the Email client button.
Go to the email client and click the link in the confirmation email to complete the registration.
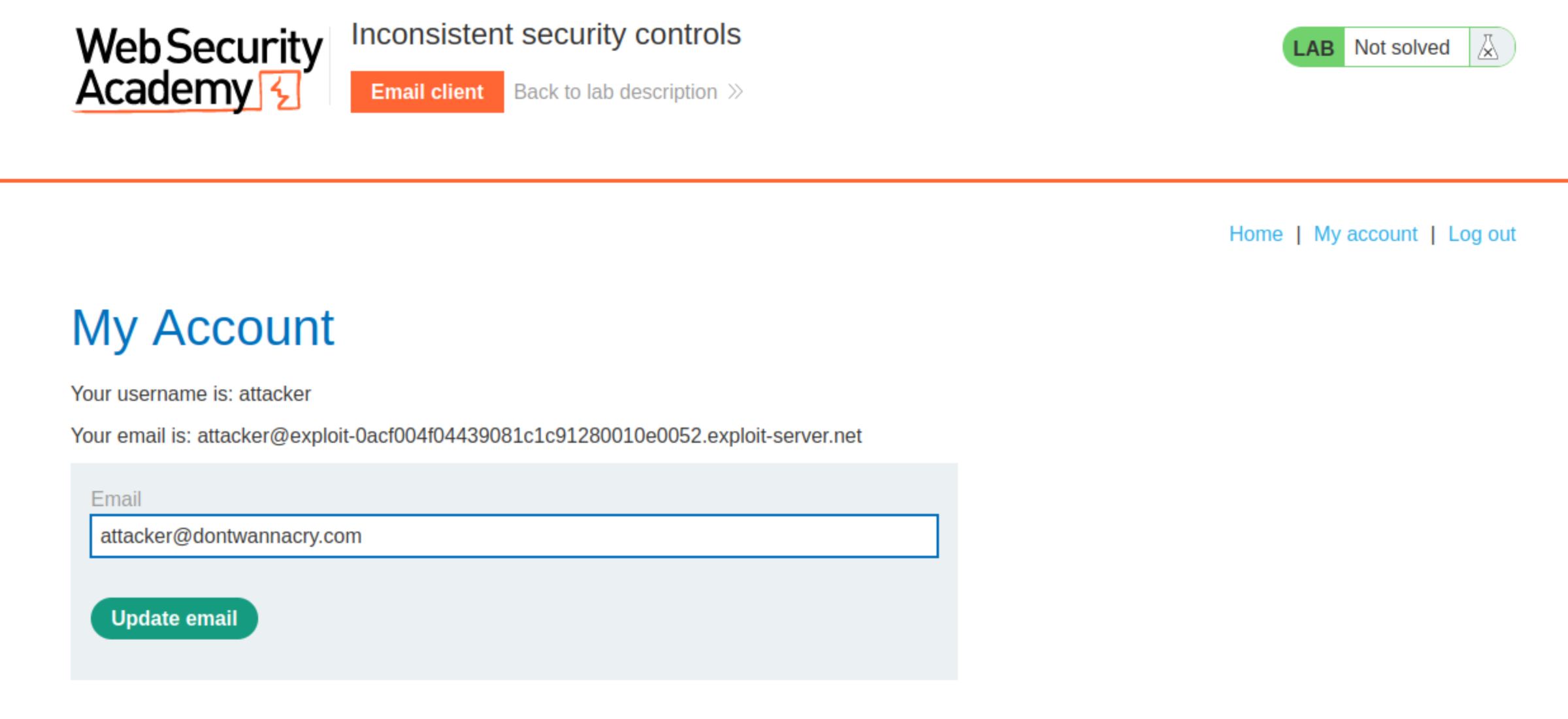
Log in using your new account and go to the My account page. Notice that you have the option to change your email address. Change your email address to an arbitrary
@dontwannacry.comaddress.
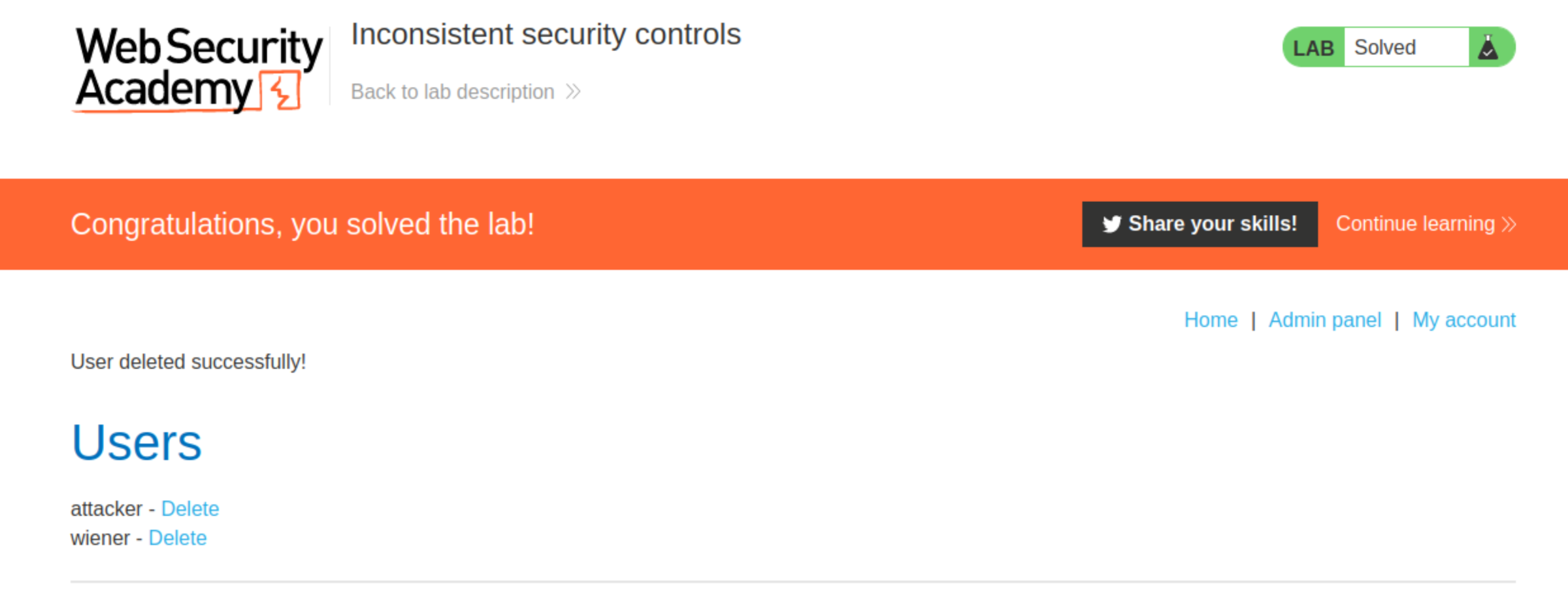
Notice that you now have access to the admin panel, where you can delete Carlos to solve the lab.
Exploitability
An attacker will need to access the admin panel and delete Carlos.