DOM XSS via an alternative prototype pollution vector
Description
This lab is vulnerable to DOM XSS via client-side prototype pollution.
Reproduction and proof of concept
Load the lab in Burp’s built-in browser.
Enable DOM Invader and enable the prototype pollution option.
Open the browser DevTools panel and go to the DOM Invader tab and reload the page.
Observe that DOM Invader has identified a prototype pollution vector in the search property i.e. the query string.
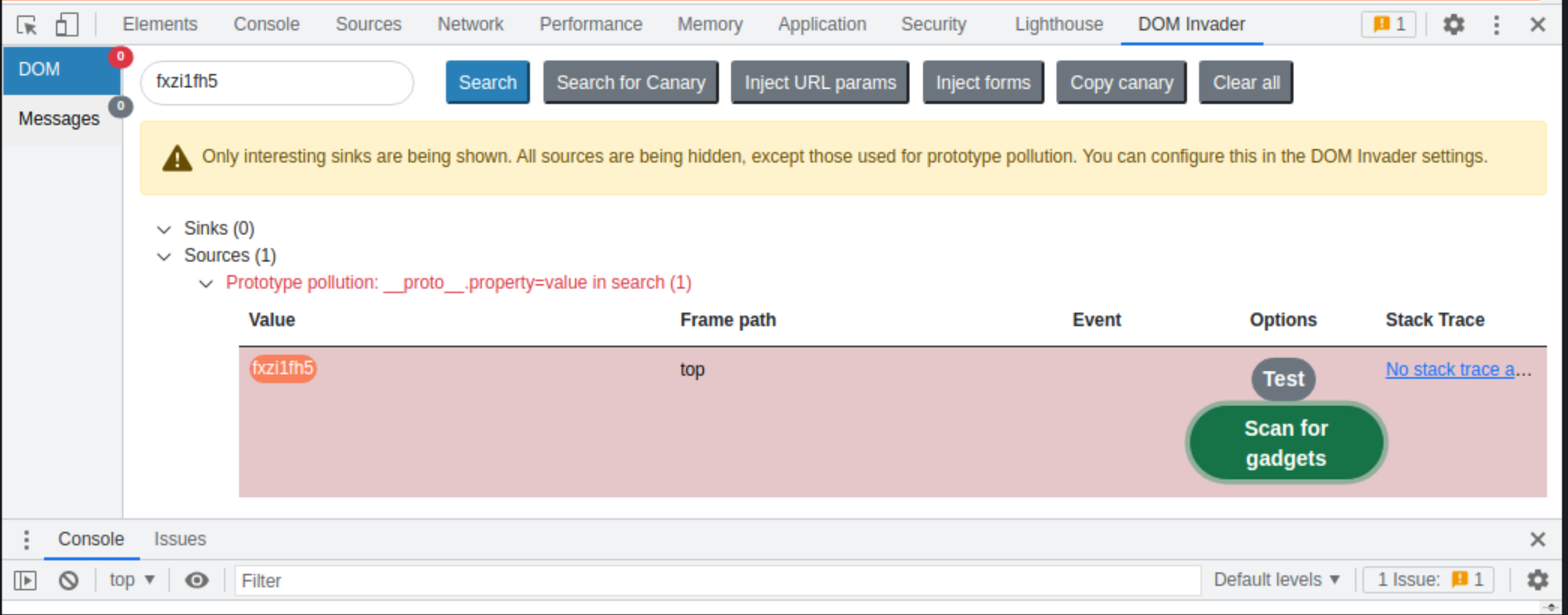
Click Scan for gadgets. A new tab opens in which DOM Invader begins scanning for gadgets using the selected source.
When the scan is complete, open the DevTools panel in the same tab as the scan, then go to the DOM Invader tab.
Observe that DOM Invader has successfully accessed the
eval()sink via the sequence gadget.
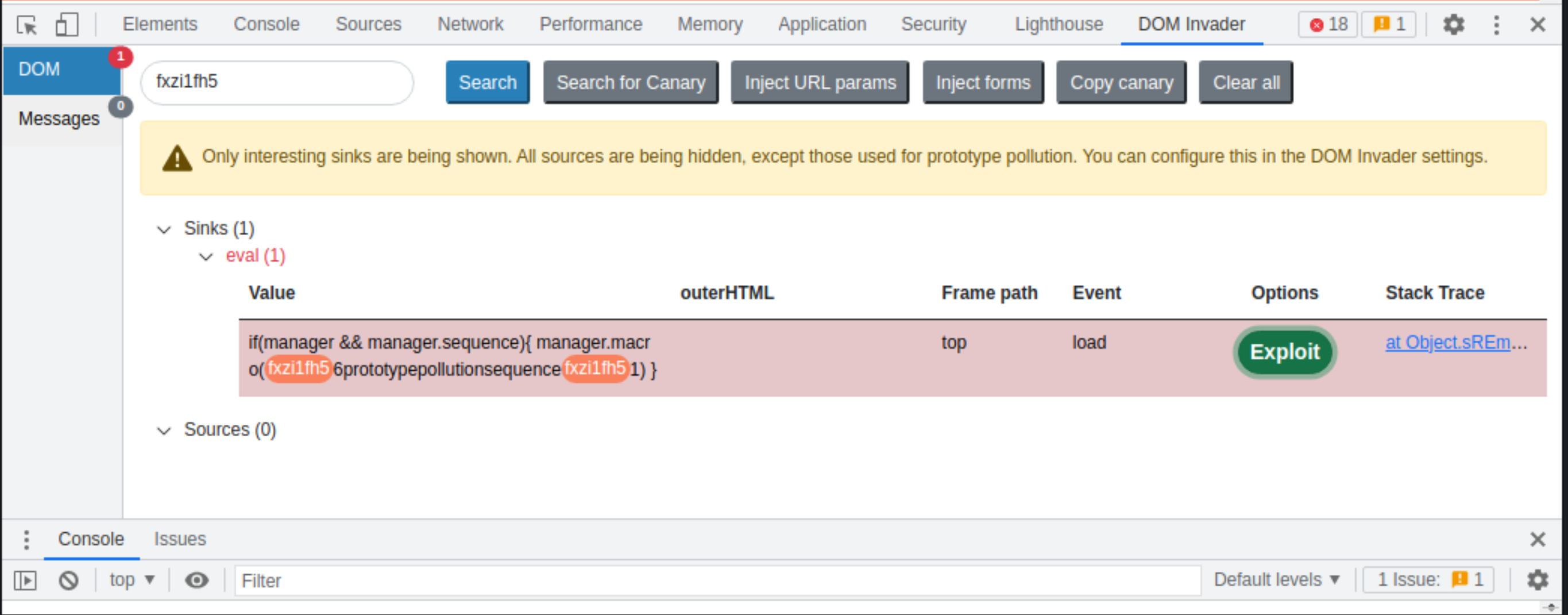
Click Exploit. Observe that DOM Invader’s auto-generated proof-of-concept doesn’t trigger an
alert().Go back to the previous browser tab and look at the
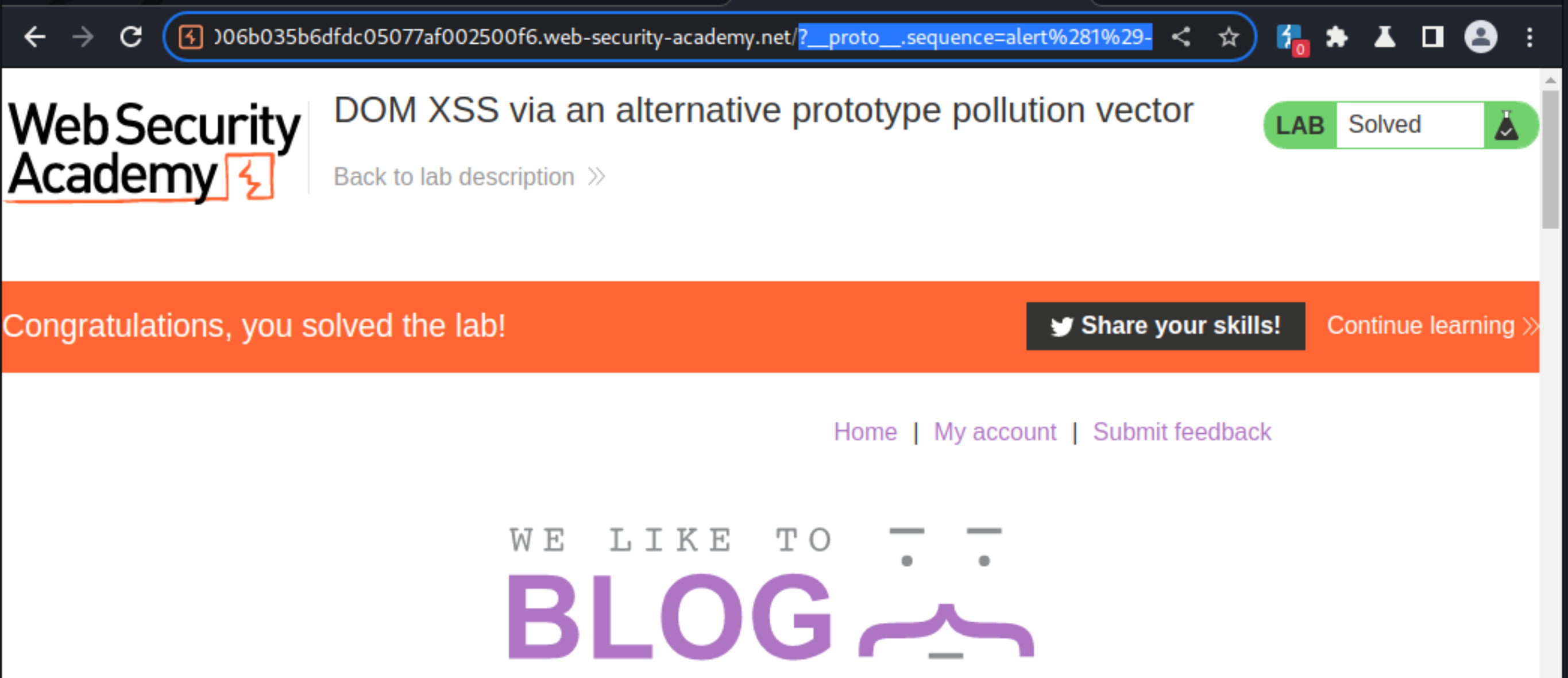
eval()sink again in DOM Invader. Notice that following the closing canary string, a numeric 1 character has been appended to the payload.Click Exploit again. In the new tab that loads, append a minus character (
-) to the URL and reload the page.Observe that the
alert(1)is called and the lab is solved.
Exploitability
An attacker will need to find a source that can be used to add arbitrary properties to the global Object.prototype; identify a gadget property that allows for executing arbitrary JavaScript; combine these to call alert().
This lab can be solved manually in a browser, or by using DOM Invader.