Manipulating WebSocket messages to exploit vulnerabilities
Description
This online shop has a live chat feature implemented using WebSockets. Chat messages that you submit are viewed by a support agent in real time.
Reproduction and proof of concept
Click Live chat and send a chat message.
In Burp Proxy, go to the WebSockets history tab, and observe that the chat message has been sent via a WebSocket message.
Using your browser, send a new message containing a
<character. In Burp Proxy, find the corresponding WebSocket message and observe that the<has been HTML-encoded by the client before sending.
{"message":"<"}
Ensure that Burp Proxy is configured to intercept WebSocket messages, then send another chat message.
Edit the intercepted message to contain the payload:
<img src=1 onerror='alert(1)'>
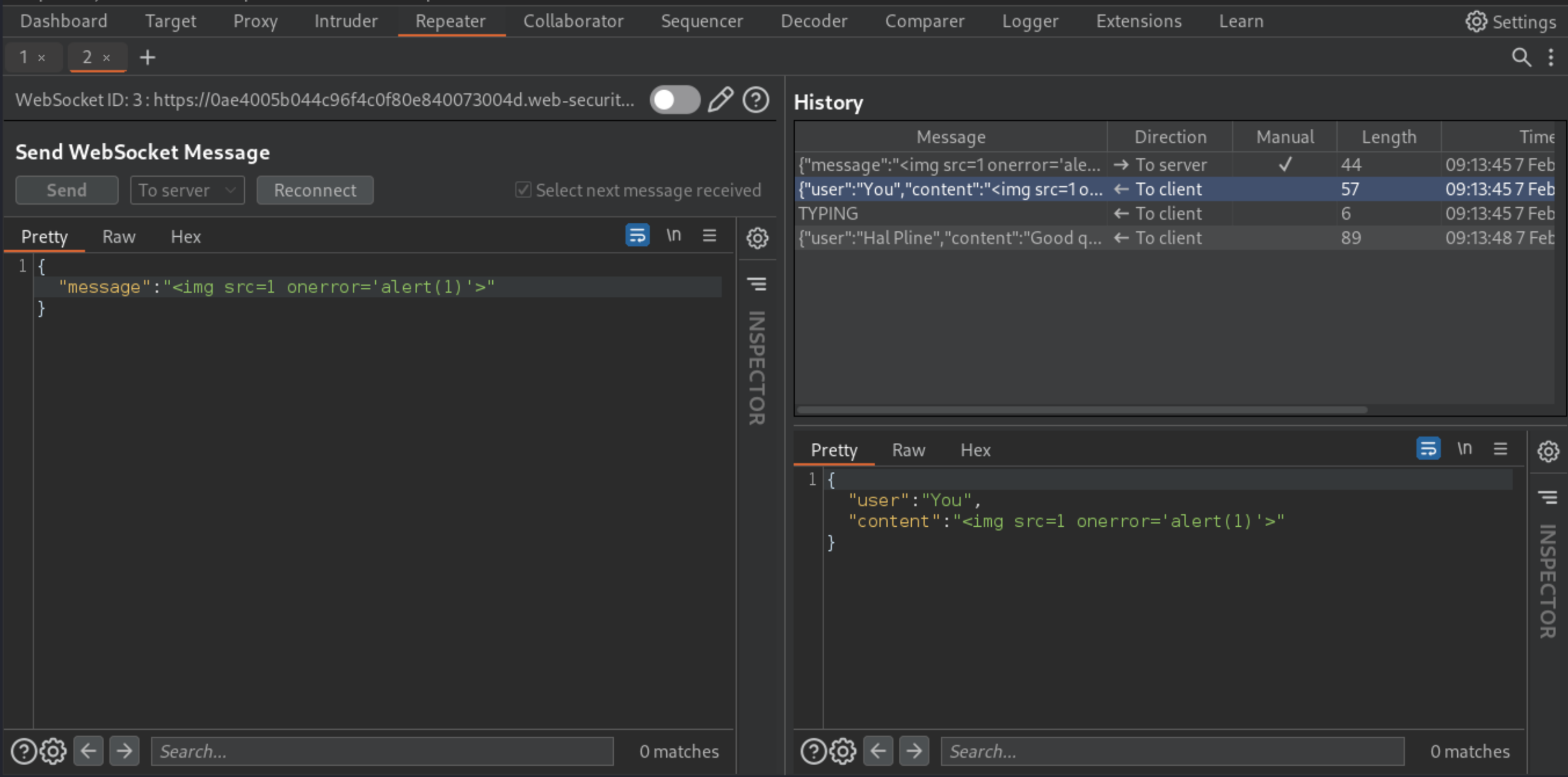
Observe that an alert is triggered in your browser. This will also happen in the support agent’s browser.
Exploitability
An attacker will need to use a WebSocket message to trigger an alert() popup in the support agent’s browser.